Website Security Checklist for Business Owners
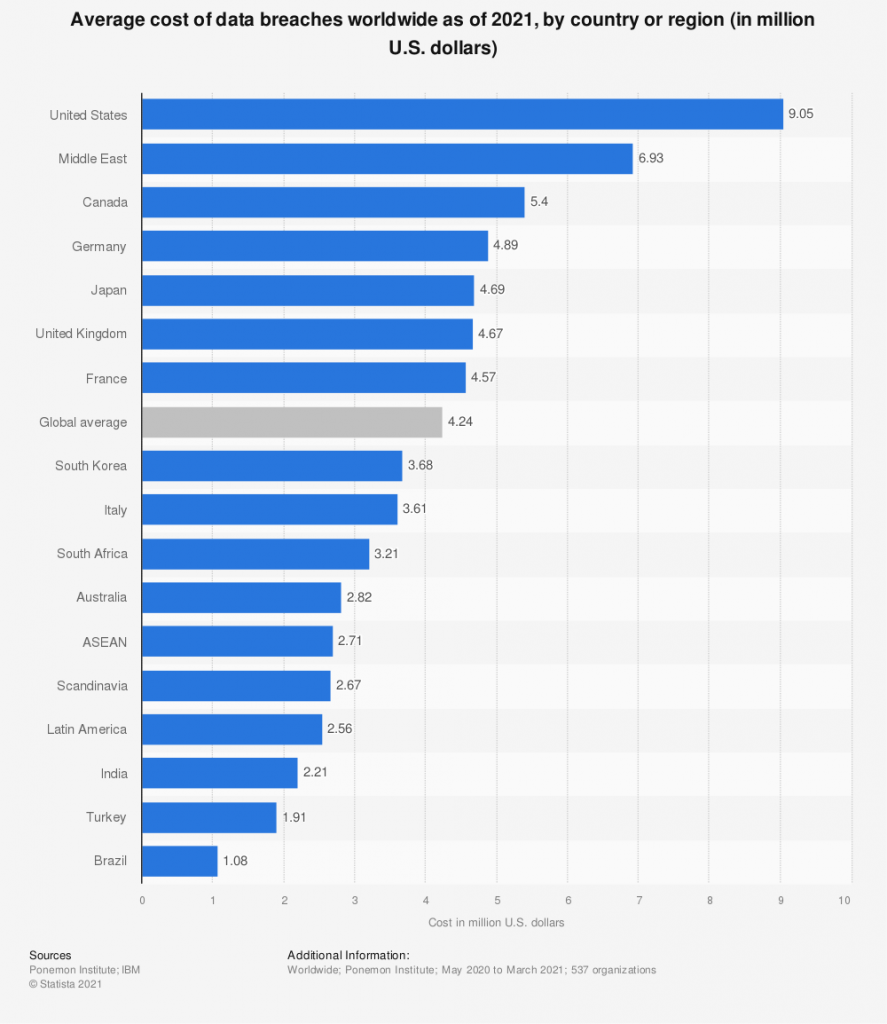
Security experts expect the global cost of cybercrime will reach $10.5 trillion USD annually by 2025. The average cost of a data breach is already over $9 million in the US alone making business owners anxious.
While cloud adoption has solved scaling, customizing, and infrastructure maintenance and delivery problems, securing web assets is a major concern for online businesses. Here is your guide to keeping your business, customers, and transactions secure from hacking attempts.
7 Website Security Checklist
1. Scan the website for weaknesses
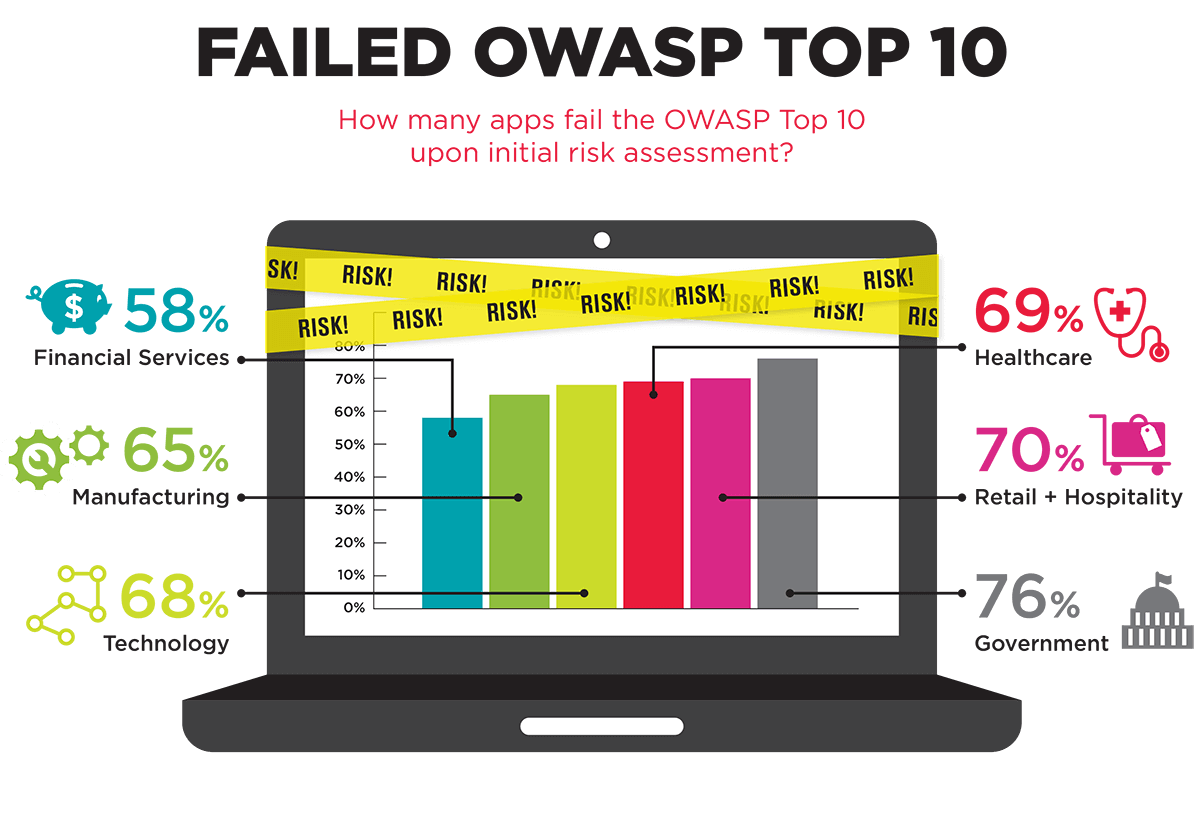
Gartner Group estimated that more than 70% of breaches happen at the application layer. Web applications serve numerous clientele and customers. Clearly, hackers have higher motivation in targeting apps to bring down critical business processes. Automated web application scanning is the most effective way of finding website security loopholes that hackers might target. This is the first step toward securing business websites.
AppTrana Basic Scanning (Free Forever): provides biweekly security scans that look for OWASP Top 10 and SANS Top 25 vulnerabilities. You can scan up to 250 pages of a website and receive a detailed report on security issues like XSS, SQL Injection, and more.
2. Keep software updated
It is obvious yet overlooked. Software patches play a crucial role in keeping your site secure from hackers. This applies to everything in your bucket including server operating systems, CMS, and other software used in the company. When website security holes are found in a third-party application, hackers target all the websites using that susceptible version of the software.
Many developers defer updates citing delivery deadlines. The massive “WannaCrypt” ransomware attack is one example of an attack that crippled computers in at least 150 countries and caused damages worth $4 billion.
3. Validate user data
Allowing users to send or upload anything to your server is a huge security loophole. From a business point of view, interactive interfaces are efficient, but the risks are high. Even a simple non-sanitized string in the username field or file upload in the image section can bring the servers down.
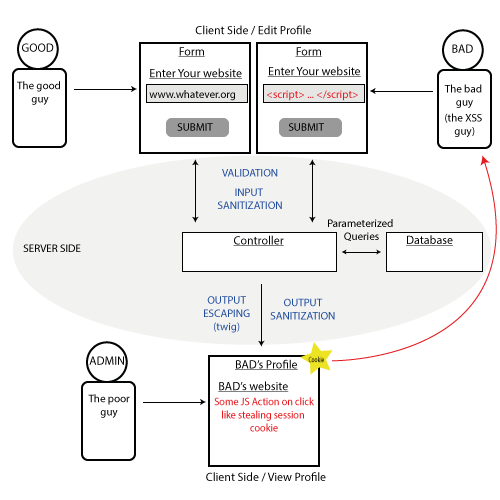
You need to treat all user inputs with great suspicion and ensure that only predetermined input formats are accepted. Ensure that your firewall is blocking all kinds of executable files and other user inputs. Also, prohibit physical access to the server completely.
4. Get periodic penetration testing
Business applications are complex. There are several variable settings across backend/frontend servers and APIs that are exclusive to your business. Automated scanning tools have their limitations, especially if your application is built on varying logic.
- An e-commerce site allows users to add items to their cart, view a summary page, and then pay. What if they could go back to the summary page, maintaining their same valid session and inject a lower cost for an item and complete the payment transaction?
- Can a user hold an item infinitely in their shopping cart and keep others from purchasing it?
- Can a user lock an item in a shopping cart at a discounted price and purchase it several months later?
- What if a user books an item through a loyalty account and gets loyalty points but cancels before the transaction is completed?
Manual penetration testing or ethical hacking replicates all the attempts that a hacker would. They spend hours looking for weaknesses that would compromise the application’s function and suggest fixes to the developers.
5. Use HTTPS
Secured HTTP connections prevent hackers from intruding on the communication between your website and users. Using Non-HTTPS communications, an attacker can trick the user into giving sensitive information or sending malware/executable code to the server.

If your business applications handle sensitive data such as payment information, you will have to invest in quality SSL certificates to force cryptographic protocols across all websites to browser communications.
6. Deploy a Web Application Firewall (WAF)
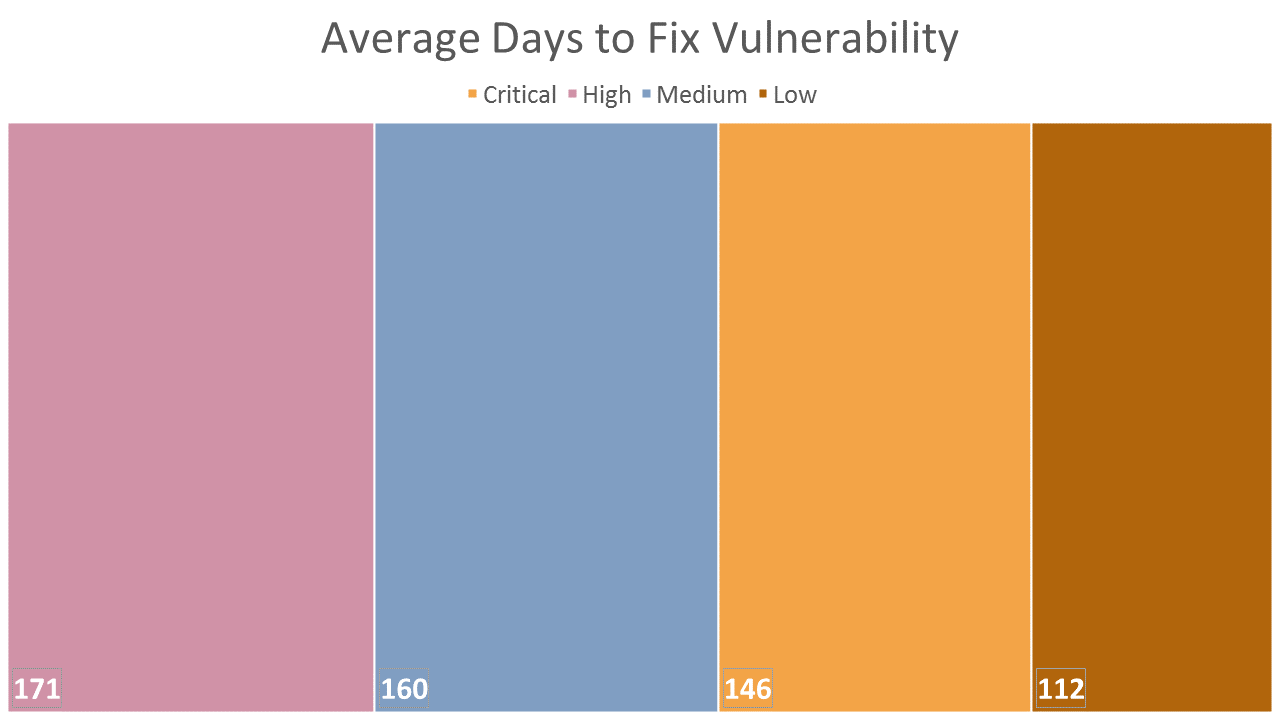
According to the Web Application Security Statistics Report, critical vulnerabilities are fixed in 146 days on average. That’s five months for hackers to try different attack methods. Change that to secure your website.
A Web Application Firewall (WAF) is designed to patch application weaknesses (OWASP Top 10 and SANS 25) virtually while monitoring and filtering traffic. Also known as the Layer 7 firewall, it stops attacks exploiting cross-site forgery, cross-site scripting (XSS), file inclusion, and SQL injection without development/code changes in the application.
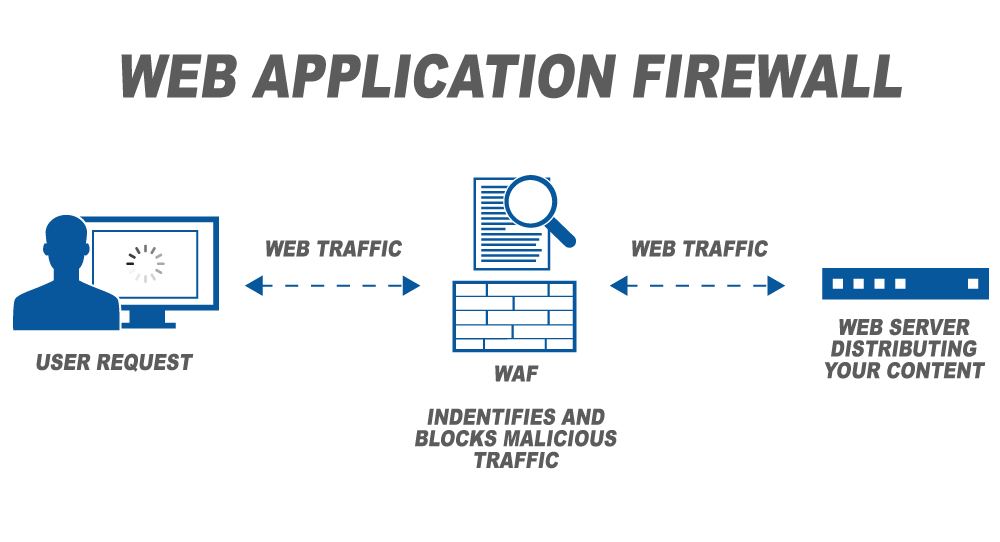
AppTrana WAF (14-Day Trial): Modern web application firewalls provide managed security in sync with scanning. AppTrana patches vulnerabilities to stop and monitor attacks. It’s an intelligent firewall that learns from frequent attack patterns and accepts custom blocking or logging rules instantly.
7. Monitor traffic surges
A distributed denial-of-service (DDoS) attack uses multiple compromised systems or other network resources to overwhelm an online service, making it unavailable.
Any website can be compromised with a DDoS attack.
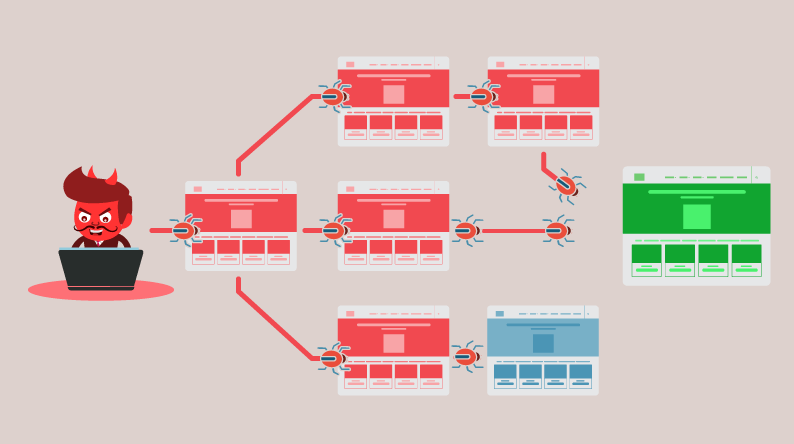
Monitoring fake traffic surges and stopping bots before damage is the only way to manage DDoS attacks. Periodic validation of your network and application’s security performance is advisable.
Keep site secure with this website security checklist
- Scan it with AppTrana Free
- Update all software
- Request penetration testing
- Install SSL
- Route Traffic through WAF
Found this article interesting? Follow Indusface on Facebook, Twitter, and LinkedIn to read more exclusive content we post.


 March 30, 2022
March 30, 2022