Critical Website Security Statistics India
We have repeatedly talked about how website security is a very niche branch of information security. It requires a specific understanding of how Layer 7 interacts over the World Wide Web and also other communication layers within the organization network. But, is it really important to get into these details? Is it really your concern?
Isn’t that covered by the cybersecurity team? In an ideal world, it should be, but there are three solid facts that speak otherwise.
- Every 7 hacking attacks out of 10 happen at the application layer (Gartner)
- 1,000,000,000 (a billion) personal records were stolen globally last year (CNBC)
- The monetary cost of such cyber attacks are huge
These numbers speak volumes about our cybersecurity (mainly about how it’s failing), but the lack of understanding in the web application security domain is pretty clear. Plus, there’s more to be read between the lines here. For instance, why are these stats always on a global scale? Why do we not have anything on Indian companies?
There’s a growing scarcity of subcontinent specific data on cyber hacking that can educate our CIOs and CISOs understand the risks and take better security risks before we ramp on the history of the West and lose billion doing so.
State of Application Security in India
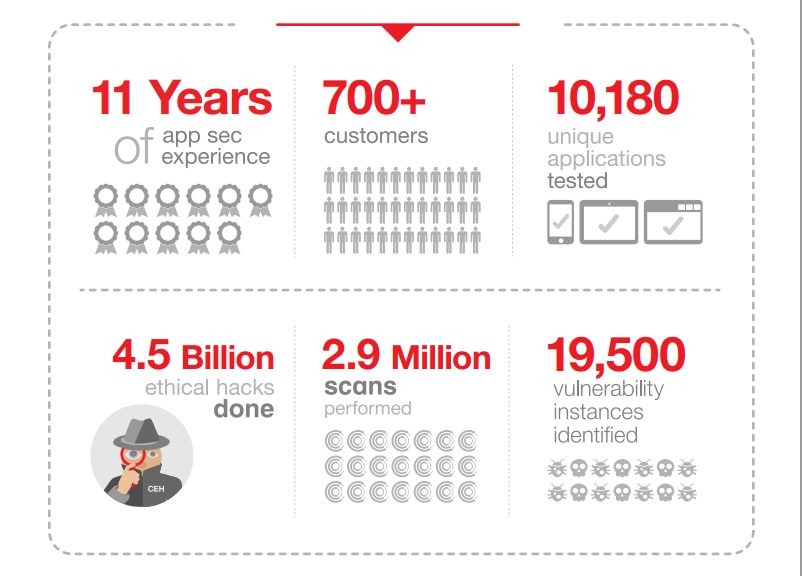
Last year, we realized that subcontinental organizations need a closer look at the local scenario of problems rather than reading about what’s happening with global companies like Target, Sony, and Alibaba. They needed concrete facts about if the risks were real even for companies out here and if so what are the ways that hackers can breach the system, which inspired us to work on ‘State of Application Security’ info graph. Here are some of the key India-centric facts from it.
- 91% of the websites detected with ‘Critical’ vulnerabilities tested by IndusGuard Web had SQL Injection vulnerability
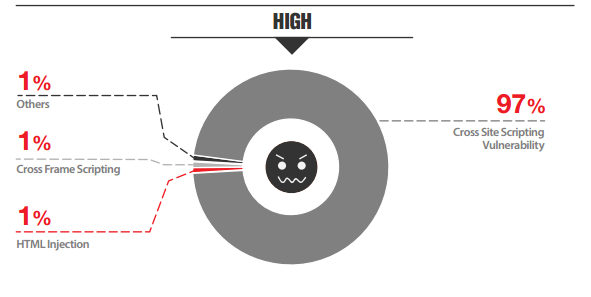
- 97% detected with ‘High’ vulnerabilities were prone to Cross-Site Scripting attacks
- SQL Injection and Sensitive Information Leakage by web application breach have increased significantly
Apart from this, we had also talked about following India-specific facts and figures in Secure Online Business and Transactions, Businesses Lose $3.8 Mn Annually to Cyber Attacks and others.
- More than 10 million internet shoppers, growing yearly by 30%, luring cybercrimes
- 185 million active mobile internet users with 243% growth, a platform which is highly vulnerable
- 58% attacks are for financial gains and 42% by foreign governments
- 155.GOV and.NIC domains were hacked last year
- 32,323 public Indian website was hacked in 2014 with 14% Y-o-Y increase
Real Problems
It’s critically important to dig a little deep into these stats for two reasons. One, our country does not have governmental bodies like National Security Agencies or Defensive Cyberspace Operations & Intelligence Conference that can analyze threats and release advisories, which happens frequently in countries like the United States of America and Israel. Two, global best practices and prevention techniques might not be influential in every scenario.
Indian companies should refer to a lot of sources in order to follow the best practices in application security, which is often incredibly confusing and time-consuming. That’s where this little guide will help you understand the paradigm shift in the web application security domain.
1. Database breach is easier.
Looking at the data that we had collected from more than 2.9 million scans and 4.5 billion ethical hacks, our experts are certain that it’s easier for hackers to infiltrate into the databases. There’re two reasons for it. Firstly, SQL vulnerability was found on many of the applications, which provides direct access to the database where attackers can read and edit files. Secondly, rarely system administrators know about it.
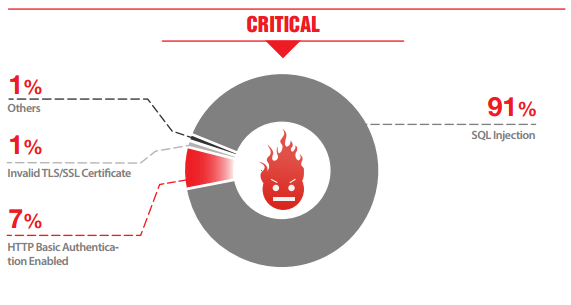
Given that most medium-sized organizations in our country are unable to detect SQL Injection attacks, there are chances that many of them are bleeding sensitive data without knowledge.
2. Cross-Site Scripting is abundant.
Although XSS is not really one of the most pressing issues for most companies, it is as common as SQLi. Approximately 97% detected with ‘High’ vulnerabilities were prone to Cross-Site Scripting attacks, pointing out that many administrators are not looking into it. However, XSS can cause real problems for businesses by not only putting their servers at risk but also users.
You can read about it on Learn About Cross-Site Scripting (XSS) The Way It Matters
3. Most organizations are not testing their applications.
When we said that around 7 out of 10 websites are hacked at the application layer, it’s actually a serious problem, but overemphasis on network security and lack of awareness of application security has made many companies overlook the risks entirely. Most of them do not even know about OWASP Top 10 vulnerabilities or don’t know how they can be used to breach into the system.
Here’s a link to free website analysis and demonstration of attacks.
4. Application patching is procrastinated.
If it isn’t broken, why fix it? Probably one of the primary reasons why most companies overlook application layer vulnerabilities is that these are difficult to fix. E-com and other competitive industries have to frequently make changes, where customer experience is their top priority. On the other hand, banking, insurance, and other finance companies aren’t too keen to change things as it involves complete planning and auditing.
It is understandable that most companies won’t re-code the application until it’s really necessary, but security does not really need to suffer during the process. A WAF is actually the kind of solution that can help here. It can virtually patch vulnerabilities without trouble developers or website admins.
The Future of Web App Security
Attacks on Layer 7 are definitely going to increase primarily because of its public-facing nature. We have already witness giants of the West falling to these breaches and it’s about time to raise the concerned bar before something major happens in the subcontinent.
While enterprises should adopt application security for obvious reasons, a small and medium businesses cannot shy away from it either. They have to begin at the basic level at least. But more importantly, our government websites that handle defense and other sensitive data should test and protect web applications as the cross-country wars heat up at a global scale.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 June 4, 2015
June 4, 2015




