The Importance of Vulnerability Assessment: Types and Methodology
What is a Vulnerability Assessment?
Vulnerability assessment is the process of identifying the threats or weaknesses in computer systems, networks, and software, along with the inherent risks they introduce.
Vulnerability assessments done by performing black box or grey box security testing simulate real-life scenarios of how hackers attack applications. After all every application is a black box from a hacker’s perspective and they just brute force various attack types using sophisticated scanners.
Vulnerability Assessment and Penetration Testing(VAPT) helps organizations figure out where they might be at risk to prioritize remediation based on the severity level.
What Is a Vulnerability?
Vulnerabilities refer to errors or weaknesses within a system’s security protocols, structure, execution, or internal management that could potentially breach the system’s security policies.
How to Perform Vulnerability Assessments?
To identify code or security vulnerabilities in advance, performing a SAST or a DAST scan and integrating these tools in your CI/CD pipeline is recommended. These vulnerability scanners use databases of known vulnerabilities to detect potential weaknesses across applications, systems, data, and other elements.
The vulnerability scanner performs a thorough scan across all dimensions of your technology. It examines the target system for known security issues, misconfigurations, outdated software, and potential entry points that attackers could exploit. Once the scans finish, the tool presents a report detailing all uncovered problems and proposes measures to counter potential threats.
More comprehensive tools could go further by providing SIEM Integration. With this integration, the data from vulnerability scanner can be pushed into a SIEM (Security Information & Event Management), enhancing the scope of threat analysis.
Asset discovery and monitoring is a valuable attribute of Indusface WAS, facilitating the creation of a complete asset inventory and enforcing consistent security monitoring for all assets.
Vulnerability Assessment vs. Penetration Testing
Vulnerability assessment is more focused on identifying vulnerabilities and weaknesses, while penetration testing involves actively exploiting those vulnerabilities to assess their real-world impact. Vulnerability assessments help organizations identify areas that need attention and prioritize fixes, while penetration testing helps organizations understand the potential consequences of successful attacks and improve their incident response capabilities.
Key features of a vulnerability assessment:
- Scanning: Automated tools are used to scan the target system for known vulnerabilities.
- Identifying Weaknesses: The assessment identifies security weaknesses and provides a prioritized list of vulnerabilities.
- No Exploitation: Vulnerability assessment does not involve actively exploiting vulnerabilities; it focuses on identification and reporting.
- Remediation Recommendations: The assessment results typically include recommendations for remediation and mitigation.
Key features of penetration testing:
- Active Exploitation: Penetration testing involves actively attempting to exploit vulnerabilities to assess their impact.
- Realistic Scenarios: Testers simulate real-world attack scenarios to identify potential entry points and the extent of damage that could occur.
- Manual and Automated Testing: Both manual techniques and automated tools are used to identify and exploit vulnerabilities.
- Limited Scope: Penetration testing usually focuses on specific target systems or components.
- Actionable Insights: Penetration testing provides actionable insights into the effectiveness of security measures and the potential impact of successful attacks.
Vulnerability Assessment Types
Several types of vulnerability assessments can be conducted, including:
1. Network-Based Vulnerability Assessment
A network-based vulnerability assessment identifies vulnerabilities in network devices such as routers, switches, firewalls, and other network infrastructure components. The primary goal of a network-based vulnerability assessment is to identify weaknesses in the network that attackers could exploit to gain unauthorized access, steal data, or launch attacks.
Network-based vulnerability assessments typically involve specialized software tools and techniques that scan the network for vulnerabilities. These tools may use various methods to identify vulnerabilities, such as port scanning, vulnerability scanning, password cracking, and network mapping.
2. Application-Based Vulnerability Assessment
An application vulnerability assessment is a process of reviewing security weaknesses in software applications(Layer 7) including websites, mobile apps and APIs. It examines if the apps are susceptible to known vulnerabilities and assigns severity/criticality levels to those vulnerabilities, recommending remediation or mitigation if and whenever needed.
These assessments typically involve testing the application for common vulnerabilities, such as SQL injection, cross-site scripting (XSS), and other OWASP Top 10 vulnerabilities. Application vulnerability assessments can be performed using both automated and manual methods.
OWASP consistently compiles a list of the most critical application vulnerabilities, updated periodically. In its latest OWASP Top 10 risks 2021 ranking, the following vulnerabilities demand attention:
- A01:2021-Broken Access Control
- A02:2021-Cryptographic Failures
- A03:2021-Injection
- A04:2021-Insecure Design
- A05:2021-Security Misconfiguration
- A06:2021-Vulnerable and Outdated Components
- A07:2021-Identification and Authentication Failures
- A08:2021-Software and Data Integrity Failures
- A09:2021-Security Logging and Monitoring Failures
- A10:2021-Server-Side Request Forgery
3. API-Based Vulnerability Assessment
API vulnerability assessment is conducted to identify and mitigate potential security risks in APIs. This process identifies vulnerabilities and weaknesses in the API’s design, implementation, and deployment. The goal is to ensure that the API is secure, reliable, and resilient to attacks.
The following OWASP API Top 10 vulnerabilities require specific attention in vulnerability assessment process to ensure the security and integrity of API interactions:
- API1:2023 Broken Object Level Authorization
- API2:2023 Broken Authentication
- API3:2023 Broken Object Property Level Authorization
- API4:2023 Unrestricted Resource Consumption
- API5:2023 Broken Function Level Authorization (BFLA)
- API6:2023 Unrestricted Access to Sensitive Business Flows
- API7:2023 Server-Side Request Forgery (SSRF)
- API8:2023 Security Misconfiguration
- API9:2023 Improper Inventory Management
- API10:2023 Unsafe Consumption of APIs
4. Host-Based Vulnerability Assessment
A host-based vulnerability assessment identifies vulnerabilities in individual host systems, including servers, workstations, and laptops.
These assessments typically involve scanning the host system for known vulnerabilities, such as missing security patches or outdated software. Host-based vulnerability assessments can be performed using both automated and manual methods.
5. Wireless Network Vulnerability Assessment
A wireless network vulnerability assessment focuses on identifying vulnerabilities in wireless networks, including Wi-Fi networks. These assessments typically involve testing the wireless network for common vulnerabilities, such as weak encryption, default passwords, and rogue access points.
Wireless network vulnerability assessments can be performed using specialized software tools and techniques.
6. Physical Vulnerability Assessment
A physical vulnerability assessment identifies vulnerabilities in physical security measures, such as locks, surveillance cameras, and access control systems. These assessments typically involve physical inspections of the facility and its security measures.
7. Social Engineering Vulnerability Assessment
A social engineering vulnerability assessment identifies vulnerabilities in human behaviour, such as phishing attacks and other social engineering techniques.
This vulnerability assessment type typically involves simulated attacks against employees to test their awareness of security threats and their ability to identify and respond to them.
8. Cloud-Based Vulnerability Assessment
A cloud-based vulnerability assessment identifies vulnerabilities in cloud infrastructure and services, such as Amazon Web Services (AWS) and Microsoft Azure.
These assessments scan the cloud infrastructure for known vulnerabilities and test the security of cloud applications and services.
What Types of Threats Does Vulnerability Assessment Find?
Here are some of the most common types of threats that can be prevented through vulnerability assessment methods:
1. Malware Infections
Malware infections are among the most common cyber threats, which can devastate organizations. Malware is typically delivered through attack vectors such as phishing emails, malicious websites, and software vulnerabilities.
2. Denial of Service (DoS) Attacks
DoS attacks are a type of cyberattack that aims to overwhelm a targeted system or network with traffic or other resources, causing it to crash or become unavailable to legitimate users. Vulnerability assessment can identify vulnerabilities in the network or systems that attackers could exploit to launch DoS attacks.
3. Data Breaches
Data breaches occur when attackers gain unauthorized access to sensitive data, such as personal information, financial data, or intellectual property.
4. Insider Threats
Insider threats are threats that originate from within an organization. These threats could come from current or former employees, contractors, or business partners who can access an organization’s IT resources.
Vulnerability assessment can identify vulnerabilities in applications, systems, and network devices that insiders could exploit to steal data or cause damage to an organization’s IT infrastructure.
5. Phishing Attacks
Phishing attacks are a cyberattack that uses social engineering techniques to trick users into sharing sensitive information, such as login credentials or financial data.
6. Web Application Attacks
Web application attacks are a cyberattack that targets web application vulnerabilities, such as SQL injection or cross-site scripting (XSS) attacks. Application vulnerability assessment can identify vulnerabilities in web applications and help organizations prioritize patching these vulnerabilities.
Vulnerability Assessment Methodology
Vulnerability Assessment steps include identifying the critical assets, performing in-depth security scans and pentests, ranking the vulnerabilities in the descending order of risk posed and finally remediation.
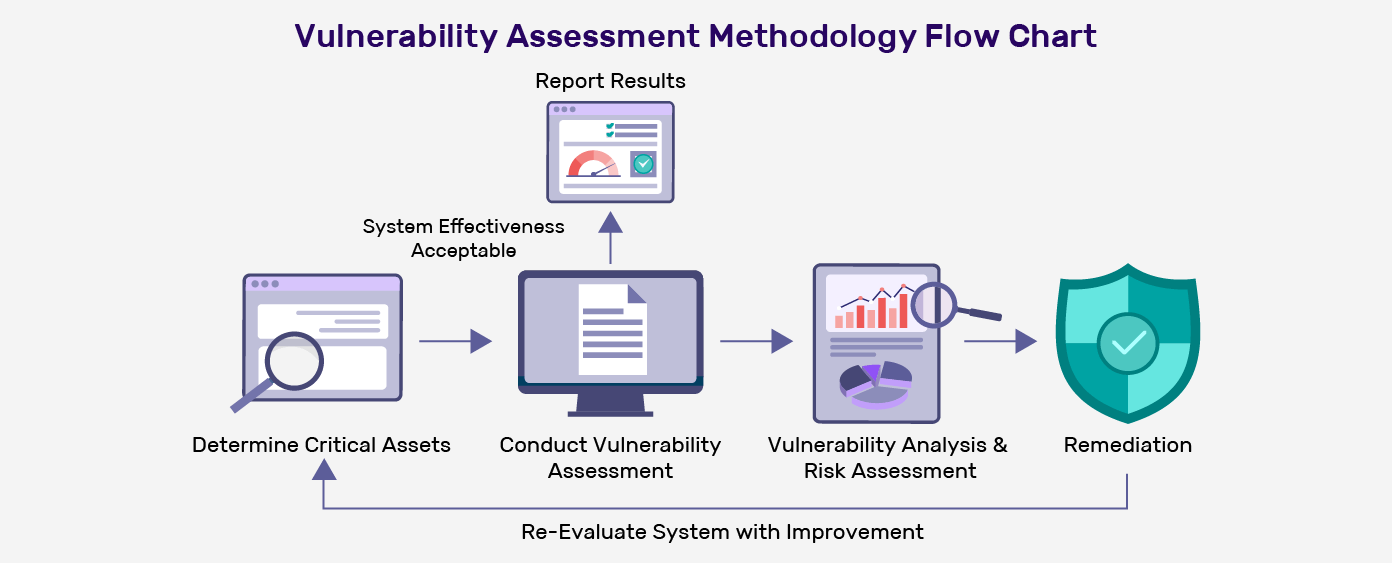
1. Determine Critical and Attractive Assets
The first step in vulnerability assessment is understanding your entire ecosystem and determining which networks and systems are more critical to your business operation.
The attacker’s objectives might vary from your perspective. Review each asset from an attacker’s perspective and rank them based on attractiveness.
2. Conduct Vulnerability Assessment
Actively scan your entire network or system through automated tools to identify security flaws and weaknesses. The critical and attractive assets should be termed “targets,” which requires further analysis, including testing with real-time scenarios to find and assess perceived security weaknesses. The assessments should rely on vendor vulnerability announcements, asset management systems, vulnerability databases, and threat intelligence feed.
The vulnerability assessment is complete if the overall network or system effectiveness meets the defined security requirements. If vulnerabilities are identified, you should proceed to the next phase.
3. Vulnerability Analysis and Risk Assessment
The next phase in the vulnerability assessment methodology is identifying the source and root cause of the security weakness identified in phase two. It offers a coherent view of remediation. It involves assigning the severity score or rank to each susceptibility based on factors like.
- What data are at risk?
- Which network or system is affected?
- The severity of the possible attacks
- Ease of compromise
- Potential damage if an attack happens
4. Remediation
The main objective of this phase is the closing of security gaps. For each identified vulnerability, determine the remediation actions. Certain remediation actions might include:
- Update all the configuration or operational changes
- Develop and implement vulnerability patches
- Implement new security measures, procedures, or tools
5. Mitigation
Not all vulnerabilities can be resolved completely; this is where mitigation comes into play. Mitigation focuses on lowering the chances of a vulnerability being exploited or minimizing the impact of its exploitation.
A practical approach, known as virtual patching, involves promptly applying a patch to the identified vulnerability without making any changes to the actual source code or components.
This virtual patch creates a protective barrier that prevents malicious actors from exploiting the vulnerability, effectively buying time until a permanent patch or code fix can be implemented.
6. Re-Evaluate System with Improvements
During this phase, the system’s security posture is reassessed using similar methods as the initial assessment, which may include vulnerability testing, penetration testing, code reviews, and other relevant techniques. The focus, however, is shifted toward determining whether the previously identified vulnerabilities have been successfully mitigated or reduced to an acceptable level.
The assessment also aims to identify any new vulnerabilities that have emerged due to the applied changes or configurations.
7. Report Results
The final phase in the security vulnerability assessment methodology is reporting the assessment result understandably.
The main goal of reporting is to clearly defining the system’s effectiveness and recommending potential solutions if the current security measure seems ineffective.
A comprehensive vulnerability assessment report will include additional factors like:
- Which system is impacted?
- The level of simplicity in attacking or compromising the system
- The potential business consequences resulting from a successful breach
- Whether the vulnerability can be accessed via the Internet or demands physical proximity
- The age of the identified vulnerability
- Any regulatory obligations your organization adheres to
- The expense associated with a data breach in your specific industry
Upgrade your vulnerability assessment process with our 15 key point vulnerability assessment checklist.
The Benefits of Ongoing Vulnerability Assessments
1. Spotting Vulnerabilities Ahead
This is one of the biggest benefits of vulnerability assessment when done routinely. When you regularly conduct vulnerability scanning using automated tools, you can find all known vulnerabilities (SQLi, XSS, CSRF, malware, etc.), security misconfigurations, and weaknesses (weak passwords, un-updated parts, etc.) in your network, applications, third-party components, codes, perimeter systems and so on. You have the first-mover advantage in closing the vulnerability window before the attackers see it.
2. Syncing Security and Change
Say you conduct vulnerability assessment on a half-yearly basis and vulnerability scanning on a weekly basis. Or you conduct vulnerability assessment once, including remediation, and leave it there.
What happens?
The business processes, applications, devices, networks, etc., change in the current dynamic IT architecture. There are lots of moving parts. The various third-party components used in applications, such as chatbots and software, etc., keep evolving, and updates keep getting released.
Many vulnerabilities may have arisen in your IT architecture, the severity of vulnerabilities may have changed, and risks may have evolved.
The larger the gaps between vulnerability assessments, the more vulnerable you are.
When we say regular vulnerability assessment, we mean
- Vulnerability scanning on a daily basis and after significant changes in the systems or business processes
- Ongoing risk assessments and remediation
- Continuous documentation
- Quarterly or half-yearly security audits and pen tests to evaluate and analyze vulnerabilities and their exploitability
3. Eliminating Mistakes Early
To ensure vulnerability assessment best practices, it’s essential to conduct assessments early in the Software Development Lifecycle (SDLC). This helps businesses ensure that misconfigurations and vulnerabilities are identified and remediated as soon as possible. For instance, it allows you to detect any vulnerable sections of code, frameworks, plug-ins, and so on, even before the application is launched for public use.
The information gathered from vulnerability assessments can serve as valuable training material for developers. This includes emphasizing the importance of adopting secure coding practices, conducting thorough reviews of source code, and ensuring a robust security architecture during the development process. Businesses that do so are likely to encounter fewer vulnerabilities when the application is launched
4. Shifting Employee Mindsets
Regular vulnerability assessments and communication of results show your employees how serious you are about cybersecurity. Thus, helping you to transform their mindset about security.
5. Offering Insights into the Risks
To build a solid security posture, organizations need to know where they stand regarding risks. Regular vulnerability assessments offer real-time insights into the organization’s risks, enabling them to act quickly.
Further, the practice allows to evaluate the strength of the security defenses and promptly detect cracks in the Armor – on the human, network, application, and systems fronts.
This way, an organization can instantly strengthen its defenses and protect its data, mission-critical assets, and infrastructure. It helps organizations maximize the efficiency of their security systems.
6. Keeping Track of Assets
The attack surface is ever-expanding with several moving parts, shared services, third-party components, and software. Organizations must be aware of their assets. With an ongoing vulnerability assessment process, organizations can create and keep updating their asset inventory.
The automated vulnerability assessment tools particularly those equipped with asset discovery capability, make this process quick, accurate, and efficient. So they can gain real-time visibility into their attack surface and identify the areas of exposure before attacks can locate and gain access to them.
7. Prioritizing Business-Critical Assets
Ongoing vulnerability assessments also tell organizations about the position and condition of each asset/system/device connected to the network, its purpose, and related systems. Based on this, assets can be prioritized, and greater efforts can be directed toward business-critical assets.
8. Making Informed Decisions
From real-time, actionable insights to thorough reporting and documentation, an ongoing vulnerability assessment equips organizations to make the right decisions at the right time, prepare solid incident response plans, and formulate robust strategies and strong security controls.
Organizations are not basing their strategy and decisions on dated information and reports but on the latest insights. This helps strengthen their security posture.
9. Building Trust with Customers
Routine vulnerability assessments reassure customers and foster trust in your business. It shows customers that you care about data security and privacy. Businesses that are victims of data breaches face large-scale customer attrition. This loss of customer confidence and trust is an uphill task for businesses.
Vulnerability Assessment Best Practices
The extensive vulnerability assessment and management task can be time-intensive, particularly when handling a broad spectrum of assets. Consider these approaches to manage the process effectively:
- Know Your Assets – Identify and categorize all assets in your environment. Understanding what you need to protect is crucial for an effective assessment.
- Automation – Leverage automated tools for scanning and identifying vulnerabilities. Automation speeds up the assessment process and ensures consistent results.
- Formulate KPIs – Define Key Performance Indicators (KPIs) to measure the success and effectiveness of your vulnerability assessment program. KPIs provide valuable insights into the program’s impact.
- Build a Vulnerability Management Database – Maintain a centralized database to track and manage identified vulnerabilities. This database aids in tracking remediation efforts and monitoring progress.
- Prioritization – Rank vulnerabilities based on severity, potential impact, and exploitability to focus on the most critical issues.
- False Positive Verification – Verify identified vulnerabilities to eliminate false positives and ensure accuracy.
- Documentation – Thoroughly document assessment findings, including vulnerabilities, evidence, and potential risks.
- Remediation Recommendations – Provide clear and actionable recommendations for addressing identified vulnerabilities.
- Collaboration – Involve different teams, such as IT, security, and development, to ensure a holistic assessment.
- Integration with Other Security Protocols –Integrate vulnerability assessment into your broader security strategy. Coordinate with intrusion detection, incident response, and other security practices for a cohesive defense.
- Share Executive Reports – Prepare summarized reports for organizational leadership, providing an overview of assessment findings, risks, and recommended actions. This promotes informed decision-making.
How Can Indusface WAS Help?
Indusface WAS leverages the power of intelligent automation to lead agility, speed, accuracy, and flexibility in the vulnerability assessment process. It performs deep, intelligent scans across the IT infrastructure while automatically discovering and adding new areas to crawl. The vulnerability assessment tool can test for existing and emerging threats that target your IT infrastructure.
In addition to automated scanning, security experts manually identify and exploit vulnerabilities that automated tools may miss.
The platform facilitates tracking the entire vulnerability assessment process, from inception to remediation. Whether you aim to achieve regulatory compliance, launch a new product, or prove your security capabilities, Indusface WAS can help you identify and patch any weaknesses before they become a liability.
Stay tuned for more relevant and interesting security updates. Follow Indusface on Facebook, Twitter, and LinkedIn


 August 18, 2023
August 18, 2023



