Understanding Serialization Attacks: Risks, Examples, and Prevention
Serialization is the process of converting data structures or object states into a format that can be easily stored, transmitted, or reconstructed later.
While serialization facilitates data maintenance and communication between different systems, it also introduces security risks.
Serialization attacks exploit vulnerabilities in the serialization process to manipulate data, execute arbitrary code, or gain unauthorized access to systems.
This blog will explore serialization attacks, real-world examples, and effective prevention measures.
Serialization and Deserialization
Serialization involves converting complex data structures or objects into a stream of bytes that can be stored or transmitted across networks. This process enables data to be reconstructed later or on a different system. Common serialization formats include JSON, XML, and binary formats like Java’s Object Serialization.
Deserialization is the reverse process, where the serialized data is converted back into its original object or data structure.
While serialization and deserialization are powerful processes for storage and data transfer, they also introduce security risks if not implemented securely.
Serialization Vulnerabilities
Serialization vulnerabilities typically arise due to inadequate input validation and insufficient security controls during the deserialization process. Attackers exploit these weaknesses to manipulate serialized data and execute malicious actions. Key serialization vulnerabilities include:
Injection Attacks: Attackers inject malicious content into serialized data to trigger code execution or perform unauthorized actions. Learn about how to prevent SQL Injection in detail.
Remote Code Execution (RCE): By exploiting deserialization vulnerabilities, attackers can execute arbitrary code on the target system, leading to complete compromise.
Data Tampering: Attackers modify serialized data to tamper with application logic, access sensitive information, or bypass security controls.
Denial of Service (DoS): Serialization flaws may allow attackers to craft malicious payloads that cause excessive resource consumption, leading to service disruption or system crashes.
Real-World Examples of Serialization and Deserialization Attacks
1. Adobe ColdFusion Remote Code Execution (CVE-2023-29300)
Adobe ColdFusion server was found vulnerable to CVE-2023-29300 in June 2023. This vulnerability involved a JNDI injection flaw that allowed for the deserialization of untrusted data, potentially resulting in Remote Code Execution. The root cause of this issue lay in the inadequate sanitization of user-provided input within the wddxPacket object transmitted via a POST request. Consequently, attackers, without authentication, were able to remotely execute arbitrary commands on the server.
This CVE was actively exploited by various threat actors, including cybercriminals and state-sponsored groups. Learn more about CVE-2023-29300 and AppTrana WAAP Coverage.
2. Apache Struts Remote Code Execution (CVE-2017-5638)
One of the most notorious serialization vulnerabilities occurred in Apache Struts, a popular Java web application framework.
In 2017, a critical deserialization vulnerability (CVE-2017-5638) was discovered in the Jakarta Multipart parser of Apache Struts 2. This vulnerability allowed attackers to execute arbitrary code remotely by sending a crafted Content-Type header in an HTTP request.
Exploitation of this vulnerability led to widespread compromises, including high-profile data breaches such as the Equifax incident, where sensitive personal information of millions of individuals was exposed.
How Does Serialization Attack Work?
Consider a web application that allows users to upload profile pictures, which are then serialized and stored in a database. The application uses a serialization format such as JSON or binary serialization to convert the image data into a format suitable for storage.
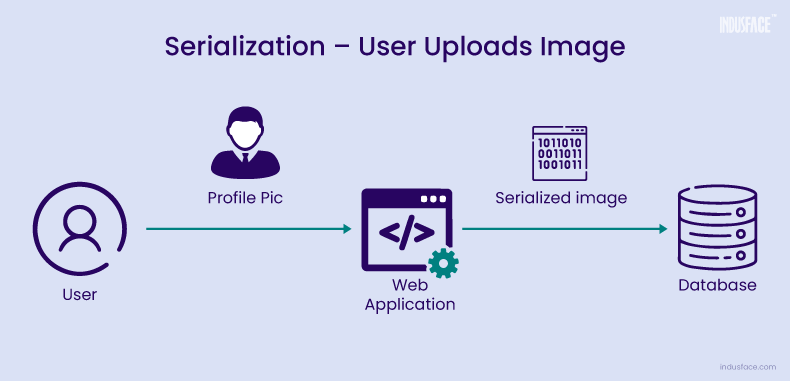
The attacker identifies a vulnerability in the web application that allows for the insecure deserialization of data.
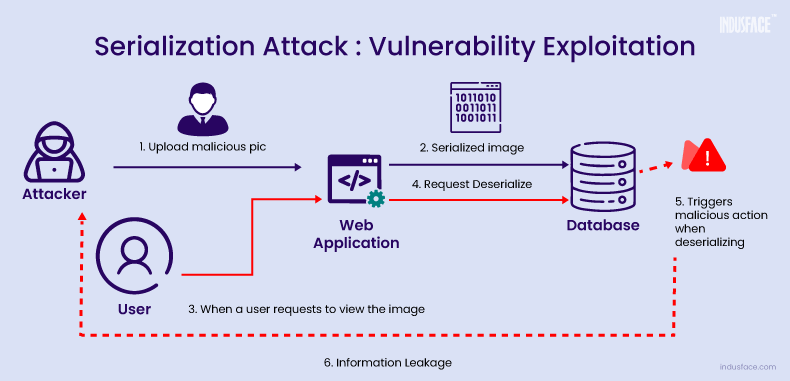
- The attacker crafts a malicious image file containing embedded executable code or instructions. This payload could exploit the vulnerability to execute arbitrary commands or gain unauthorized access to the server.
- Taking advantage of the profile picture upload functionality, the attacker uploads the malicious image file to the web application. Since the application fails to properly validate or sanitize the uploaded image data, the malicious payload remains intact.
- Upon receiving the malicious image, the web application serializes the image data using the chosen serialization format (e.g., JSON, binary serialization) and stores it in the database along with other user profile information.
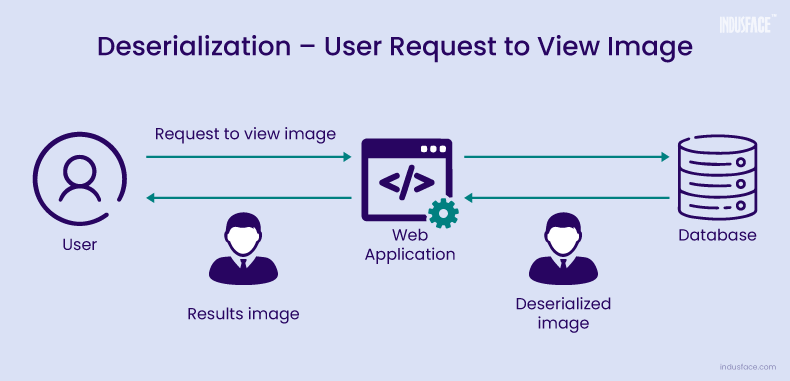
- When a user views their profile, the app deserializes the image, executing the attacker’s code. This grants unauthorized access, risking the app’s security and data integrity.
6 Preventive Measures to Mitigate Serialization Attacks
Here are some effective strategies that help to strengthen your defenses against serialization attacks and minimize the risk of security breaches.
1. Input Validation
- Validate and sanitize all user-supplied input before serialization and deserialization.
- Implement strict input validation routines to ensure that only expected data formats and content are accepted.
- Reject input data that does not adhere to the expected schema or data structure.
2. Secure Deserialization
- Ensure secure deserialization by implementing strict controls to detect and reject tampered or malicious data.
- Utilize whitelisting techniques to define permitted data types, preventing unexpected object instantiation.
- Employ integrity checks like cryptographic signatures or checksums to validate the authenticity and integrity of serialized data.
- Exercise caution when deserializing input data, limiting it to essential application functionality.
- Leverage robust security measures, including advanced Web Application Firewalls (WAFs) and digital signatures, to authenticate serialized objects and thwart tampering attempts.
- Execute deserialized objects and code within secure, low-privilege environments to minimize potential exploitation impacts.
3. Serialization Format Considerations
- Choose secure serialization formats that are resistant to common attacks, such as JSON or XML with strict schema validation.
- Avoid using insecure serialization formats or mechanisms that lack built-in security controls, such as Java’s Object Serialization.
4. Security Testing
- Conduct regular security assessments, including penetration testing and code reviews, to identify and remediate serialization vulnerabilities.
- Use automated tools and scanners to detect common serialization vulnerabilities and weaknesses in the application code.
5. Avoid Serialization of Sensitive Data
- Serialization of sensitive data, such as passwords, tokens, or personally identifiable information (PII), can expose critical information to potential attackers.
- By writing class-specific serialization methods, developers can control which fields are serialized, ensuring that sensitive data is not inadvertently exposed to the serialization stream.
- This helps minimize the risk of data exposure and unauthorized access.
6. Maintain a Log of Deserialization Failures and Exceptions
- Maintaining a log of deserialization failures and exceptions allows developers to monitor and track potential security incidents effectively.
- By recording instances of deserialization errors, developers can identify patterns of suspicious activity and investigate potential security threats promptly.
These proactive approaches enable you to detect and respond to serialization attacks on time, enhancing overall security posture.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 March 21, 2024
March 21, 2024