What is a Reverse Proxy, How Does it Work, and What are its Benefits?
What is a Reverse Proxy?
A reverse proxy is a server that sits between client devices and a web server, forwarding requests from clients to the appropriate backend server.
Unlike a forward proxy, which hides the client’s identity, a reverse proxy hides the identity of the backend server. It acts as an intermediary, helping with load balancing, security, caching, and ensuring better performance by distributing traffic across multiple servers.
How Does Reverse Proxy Work?
Reverse proxies work by sitting in front of the origin server and acting as an intermediary between clients and the server.
- A client sends a request to the web application by entering a URL or clicking a link.
- The reverse proxy intercepts the request and examines it to determine which backend server should handle it.
- The reverse proxy forwards the request to the origin server, which processes it and generates a response.
- The reverse proxy receives the response, reviews it, and then forwards it to the client.
Reverse proxies can also perform other tasks in front of the origin server, such as load balancing, SSL termination, and caching. These features can improve performance, scalability, and security for web applications.
Furthermore, you can configure them to route traffic based on various criteria, including geographic location, user agent, or cookie value. This helps optimize traffic routing and improve the user experience for clients.
Reverse Proxy vs. Forward Proxy – What are the Differences?
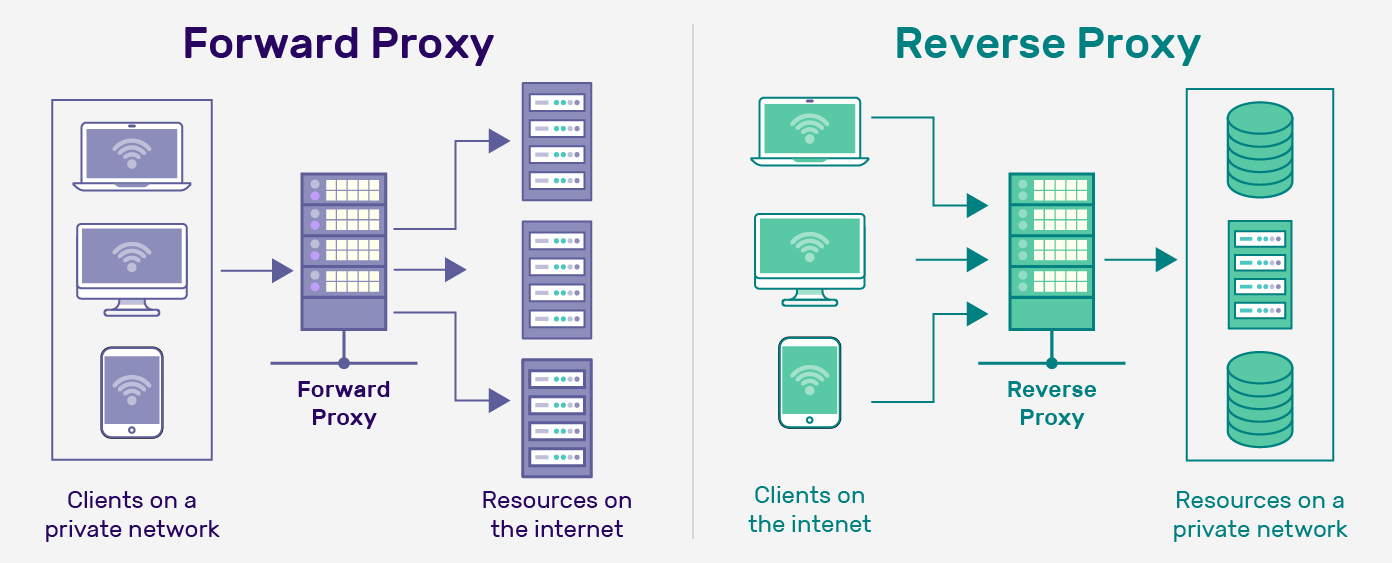
What is Proxy?
A proxy is an intermediary server that sits between a client and the internet. Its purpose is to forward client requests to a destination server and return the response to the client.
What is a Forward Proxy?
A forward proxy is a type of proxy server that operates on behalf of the client. It is the designated exit point for subnet users seeking to connect with resources outside their private network. In contrast, a reverse proxy server is the entry point for external systems to access resources within a private subnet.
Similarities Between Forward and Reverse Proxy
Both reverse and forward proxies serve as intermediaries in network communications, facilitating enhanced performance, security, and control. Acting as middlemen between clients and servers, they optimize traffic flow by intercepting and managing requests.
Regardless of their specific roles, both proxy servers contribute an additional layer of security by concealing internal network structures, making them invaluable tools in network architecture.
Differences Between Forward and Reverse Proxy
Forward proxies serve as intermediaries for clients, forwarding requests and masking their IP addresses for anonymity and content filtering. In contrast, reverse proxies manage incoming requests for servers, directing traffic to backend servers while hiding their IP addresses from clients.
A forward proxy sits between a client and the internet, while a reverse proxy sits between a client and a server.
Additionally, the authentication processes differ, with forward proxies often involving user authentication and reverse proxies focusing on server authentication.
Individuals typically use forward proxies to access restricted content, while organizations use reverse proxies to optimize their web applications.
What are Some Use Cases for Reverse Proxies and Forward Proxies?
Forward Proxy Use Cases:
Content Filtering
Forward proxies are commonly used for content filtering to control and monitor the type of content that users can access on the internet.
For example, in a corporate environment, a forward proxy can block access to certain websites deemed inappropriate for the workplace, enhancing productivity and maintaining a secure network.
Access Control
Forward proxies are instrumental in enforcing access control policies. By intercepting and evaluating outbound requests, they can restrict user access to specific websites or resources.
For instance, a forward proxy can limit students’ access to non-educational websites during class hours in educational institutions.
Bandwidth Optimization
Caching is a key feature of forward proxies that optimizes bandwidth usage by storing frequently accessed content locally. This can significantly reduce the load on the internet connection and improve the overall user experience.
In scenarios like public Wi-Fi networks or shared office spaces, a forward proxy caching mechanism helps speed up access to commonly visited websites.
Reverse Proxy Use Cases
Compression
Reverse proxy solution can compress outgoing content before delivering it to clients, reducing bandwidth usage and speeding up data transfer. This is particularly beneficial for websites with large amounts of textual content, such as news sites or blogs.
Application Acceleration
Reverse proxies can optimize application performance by offloading resource-intensive tasks like image optimization or minifying JavaScript and CSS files. This helps deliver a more responsive user experience, especially for complex web applications.
Authentication and Single Sign-On (SSO)
Reverse proxies can handle user authentication and enable Single Sign-On for multiple applications. This simplifies user access management, providing a seamless and secure experience across various services without needing separate logins.
Comparison Chart: Forward Proxy vs. Reverse Proxy
| Criteria | Forward Proxy | Reverse Proxy |
| Direction of Traffic | Outbound (client to server) | Inbound (internet to server) |
| Authentication | User authentication for clients | Server authentication for clients |
| Caching | Caches frequently accessed content | Caches static content for load balancing |
| SSL/TLS Handling | Initiates SSL/TLS connections on behalf of clients | Terminates SSL/TLS connections for servers |
| Application Firewall | Limited or none | Often includes application-level firewall capabilities |
| Scalability | Scales with the number of clients | Scales with the number of servers |
| Typical Protocols | HTTP, HTTPS, FTP | HTTP, HTTPS, TCP, SSL/TLS |
What are the Benefits of Reverse Proxy?
1. Load Balancing
Load balancing refers to distributing incoming client requests across multiple backend servers. When a client sends a request to a reverse proxy, the reverse proxy can decide which backend server should handle the request based on various factors, such as server availability, server load, or geographic location.
Load balancing helps improve performance and scalability by allowing multiple servers to handle incoming traffic. This helps distribute the load evenly among the servers, preventing any server from overloading, slowing down, or failing.
For instance, an e-commerce site handling a surge in online shoppers during a sale can employ a reverse proxy to balance the load and maintain responsive service.
2. Caching
Reverse proxies can cache frequently accessed content and serve it directly to clients, reducing the load on backend servers and improving response times.
3. SSL Termination
Reverse proxy solution can handle SSL encryption and decryption, allowing clients to connect securely to the backend server without the server having to take the overhead of SSL.
A reverse proxy managing SSL termination is critical for secure communication in online banking applications or e-commerce platforms.
For example, a reverse proxy can cache images on an e-commerce site, ensuring faster load times for product pages.
4. Threat Prevention
Reverse proxies can help protect backend servers from malicious traffic by filtering requests and blocking suspicious traffic. Reverse proxies prevent server overload and maintain smooth application operation by blocking or rate-limiting suspicious requests. It can also mask the server’s IP address, making it harder for attackers to launch a DDoS attack.
5. Scalability
A reverse proxy can add or remove servers dynamically, making it easy to scale web applications. This feature allows administrators to handle traffic spikes or increase capacity without downtime.
6. Compression
Reverse proxies can compress and optimize content before sending it to clients, reducing bandwidth usage and improving performance.
7. Routing
Reverse proxies can route requests to specific backend servers based on various criteria, such as URL path, HTTP headers, or geographic location.
8. Monitoring and Logging
Reverse proxies can monitor traffic and log activity, providing insights into usage patterns and potential security threats.
9. Flexibility
A reverse proxy can modify requests and responses in real-time. This feature allows administrators to implement complex routing rules, rewrite URLs, and add or remove headers.
Is WAF a Reverse Proxy?
Web Application Firewalls (WAFs) can be considered a type of reverse proxy. By intercepting traffic before it reaches the server, the WAF can help prevent malicious requests from reaching the origin server.
WAF can help safeguard a company’s web applications by mitigating application layer cyber-attacks such as SQL-Injection, Cross-Site Scripting (XSS), Session Hijacking, and OWASP top 10 vulnerability threats.
Indusface AppTrana uses a set of policies to filter malicious traffic without slowing down the web service.
While ensuring zero false positives, the WAF can protect web servers against all known vulnerabilities and zero-day attacks. It also serves as a load balancer to distribute traffic and ensure application and API stability.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 October 21, 2024
October 21, 2024



