SYN Flood Attack: The What, Impact, and Prevention Methods
What is a SYN Flood Attack?
A SYN flood attack is a type of network-based denial-of-service (DoS) attack in which an attacker overwhelms a target system by sending a large number of SYN (synchronize) requests to the target’s server. The attack exploits the three-way handshake process of TCP communication.
Operating at Layer 4 of the OSI model, specifically impacting the TCP protocol, a SYN DDoS attack seeks to overwhelm various network components like devices, load balancers, session management systems, or servers.
The attack disrupts the server’s ability to handle legitimate traffic and connections, causing it to become unavailable.
How Does a SYN Flood Attack Work?
TCP SYN Flooding attack is often called a “half-open” attack because, in this attack, the attacker initiates the TCP handshake by sending the SYN packets but deliberately fails to complete the process by sending the final ACK.
This leaves the targeted system with many half-open connections, consuming resources and leading to a denial-of-service condition.
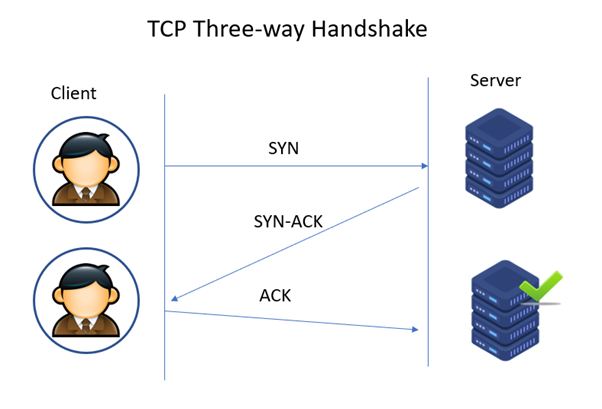
To understand the disruption caused by the SYN attack, let’s first explore the standard TCP handshake mechanism:
- When a client system intends to establish a TCP connection, it sends a SYN (synchronize) message to the server.
- The server responds to this request by transmitting the SYN-ACK back to the client.
- Subsequently, the client acknowledges the SYN-ACK with an ACK sent to the server.
- With this exchange of packets, the TCP connection is established and ready for communication.
However, in a SYN Flooding attack, the attacker deliberately disrupts this process, creating numerous unresolved half-open connections and initiating a denial-of-service scenario. Hackers can execute SYN flood attacks in three different ways:
- Direct SYN Flood Attack
- SYN Spoofed Attack
- DDoS SYN Attack
1. Direct SYN Flood Attack
In this approach, the hacker launches the attack using their own IP address, sending numerous SYN requests to the server. However, when the server responds with SYN-ACK to acknowledge the connection, the attacker deliberately refrains from responding with the required ACK. Instead, they persistently send new SYN requests to the victim server.
As the server anticipates the ACK that never arrives, the influx of SYN packets ties up server resources, creating multiple half-open connection sessions that persist for a specific duration.
This ties up the server’s resources, making it unable to function properly and rejecting requests from genuine users.
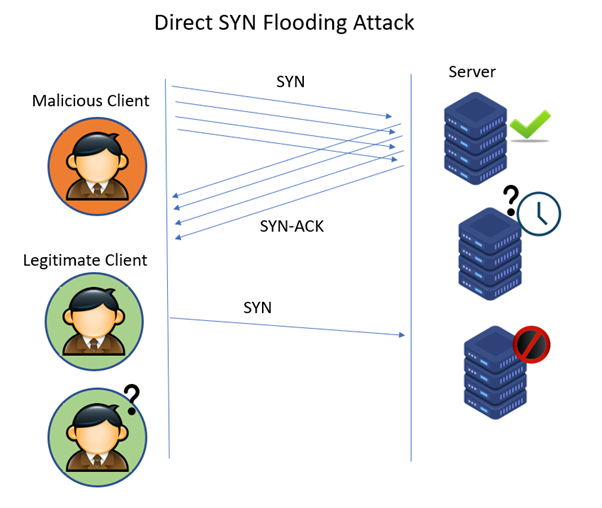
In this direct attack method, to ensure that the SYN/ACK packets are ignored, the hacker configures the firewall accordingly or restricts outgoing traffic to only SYN requests. Since the hackers use their own IP addresses, they are most vulnerable to detection. This attack is rarely employed.
2. SYN Spoofed Attack
As an alternative to avoid detection, the malicious attacker sends SYN packets from spoofed or forged IP addresses. When the server receives the SYN request, it sends a SYN-ACK to the forged IP address and awaits a response. However, there is no response since the spoofed source didn’t send the packets..
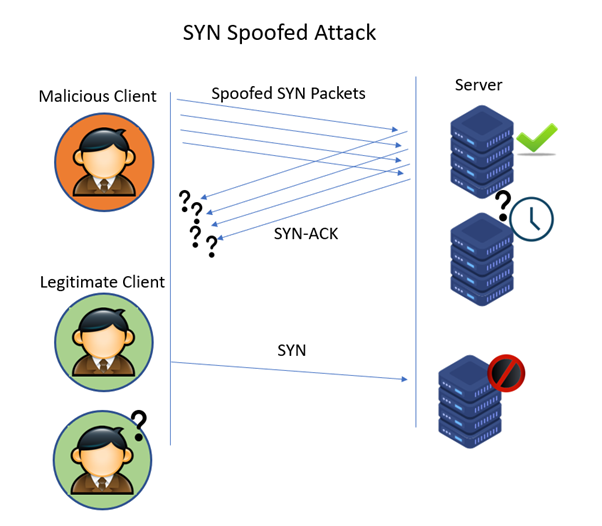
For this kind of SYN flood attack, the attackers choose the IP addresses, which are not in use, which ensures the system never responds back to the SYN-ACK response.
3. DDoS (Distributed Denial of Service) SYN attack
A DDoS SYN attack overwhelms a target’s system with a flood of SYN (synchronize) requests. In this attack, many compromised computers, often forming a botnet, coordinate to simultaneously send numerous SYN packets to the target.
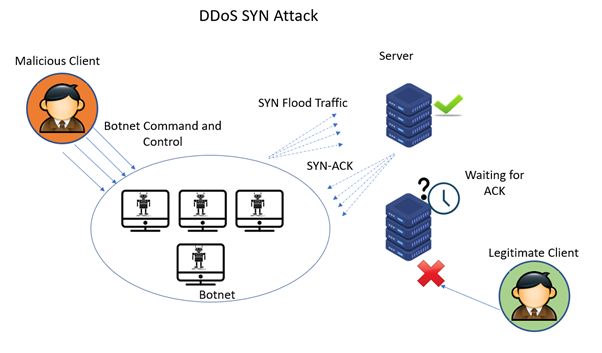
The goal is to exhaust the target’s resources, making it unable to respond to legitimate requests and causing a denial of service. The distributed nature of the attack, utilizing multiple sources, makes it more challenging to mitigate and defend against.
What is the Impact of a SYN Flood Attack on Networks?
The Mirai Botnet, famous for massive DDoS attacks, used SYN flood techniques to hack 600,000 IoT devices. Targets like KrebsOnSecurity, Lonestar cell, and Dyn.
The impact cascaded across key service providers that relied on Dyn’s services, affecting entities such as Sony Playstation servers, Amazon, GitHub, Netflix, PayPal, Reddit, and Twitter.
TCP SYN flood attack is a type of DDoS attack that presents significant risks to servers and websites, overwhelming them with fake traffic and blocking legitimate user access.
The impact of a SYN flood attack on networks can be severe and disruptive. Here are some key consequences:
- Resource Exhaustion – SYN flood attacks overwhelm a target server with a flood of SYN requests, leading to the exhaustion of resources such as CPU, memory, and network bandwidth.
- Service Disruption – As the server’s resources are depleted, it cannot handle legitimate connection requests. This results in a denial of service, causing service disruptions for legitimate users.
- Network Congestion – The excessive volume of SYN packets can lead to network congestion, affecting the overall performance and responsiveness of the network.
- Increased Latency – Legitimate users may experience increased latency as the network struggles to process the influx of SYN requests, impacting the responsiveness of services.
- Degraded User Experience – Users attempting to access services on the affected network may encounter slow response times or complete unavailability, leading to a degraded user experience.
- Operational Costs – Mitigating the effects of a SYN flood attack often requires significant resources and efforts, resulting in operational costs for organizations dealing with the aftermath.
- Reputation Damage – Prolonged service disruptions can harm the reputation of the targeted organization, leading to a loss of trust from users and customers.
- Difficulty in Detection – SYN flood attacks can be challenging to detect in real-time, allowing attackers to exploit vulnerabilities for an extended period before countermeasures are implemented.
To prevent and minimize the impact of DDoS attacks, check out the best practices for DDoS protection.
How to Detect SYN Flood Attacks?
Detecting SYN flood attacks requires careful monitoring of various indicators to distinguish malicious spikes from genuine ones.
Not all increases in server load signify attacks, making it crucial to analyze server logs, employ port scanners, and analyze network activities to identify and protect against SYN flood attacks.
Here are key factors to monitor:
- Elevated Inbound Network Traffic – SYN flood attacks generate a substantial surge in network traffic, causing a noticeable increase in incoming connections. Timely monitoring of this surge is crucial for early detection.
- Degraded Network Performance – The intensified traffic from a SYN flood attack can degrade overall network performance, leading to delayed response times for legitimate users. Investigating slow network behavior is imperative as it may signify an ongoing attack.
- Overloaded SYN Queues – Maintain a vigilant watch on the SYN queue, tracking the count of connections trapped there. A significant escalation in queued connections without proper acceptance can indicate a potential SYN flood attack.
- Non-responsive Servers – In cases where SYN requests flood backend servers and flood the SYN queue, servers may become unresponsive and incapable of handling legitimate requests. Ongoing monitoring of server responsiveness is crucial for gauging the impact of a SYN flood attack on the infrastructure.
How to Protect Against SYN Flood Attacks?
Protecting against SYN Flood attacks involves a combination of proactive network configurations, traffic monitoring, and defence technologies. Here are key strategies to mitigate SYN Flood attacks:
1. Implement SYN Cookies
SYN Cookies are a technique used to handle SYN requests without allocating resources until the handshake is completed. This method prevents the server from being overwhelmed by half-open connections during a SYN Flood attack.
2. Rate Limiting
Rate-limiting incoming connection requests is a crucial strategy to prevent SYN flood attacks. This approach entails establishing a predefined threshold for the maximum number of connection requests a server can accept within a specific time period. Any connection requests that surpass this threshold are either dropped or intentionally delayed.
3. Increasing Backlog
Increasing the backlog queue allows servers to handle a larger number of incoming SYN requests, providing a buffer against flooding attempts. Expanding the queue enables the server to accommodate more simultaneous connections during a SYN Flood attack, preventing resource exhaustion.
4. Filtering
Filtering involves setting up rules in network devices to identify and block malicious SYN requests based on specific patterns or known malicious IP addresses. This provides an early defense against SYN Flood attacks by preventing malicious traffic from reaching the server.
5. Reducing SYN-RECEIVED Timer
Reducing the time, the server waits for an ACK response after sending a SYN-ACK frees up resources allocated to half-open connections more quickly. A shorter timer allows the server to efficiently manage resources during a SYN Flood attack by minimizing the time allocated to incomplete connections.
6. SYN Cache
Instead of allocating significant resources for each incoming SYN request, the server uses a cache to store less information about each request. This approach minimizes resource consumption by handling only valid connection requests and efficiently managing incoming traffic.
7. Load Balancers
Load balancers are crucial in mitigating SYN flood attacks, especially to handle the entire TCP SYN/SYN-ACK/ACK handshake. They distribute incoming network traffic across multiple servers, ensuring that no single server bears the full brunt of the attack.
Load balancers intelligently manage the connection requests, analyze the handshake process, and shed SYN flooding before it reaches backend servers. While the impact of a SYN flood attack may still be felt, having load balancers helps distribute the load and prevents overwhelming individual servers.
They act as a frontline defense, minimizing the impact on backend infrastructure and maintaining overall system availability during SYN flood attacks.
8. Firewalls and Proxies
Deploying firewalls and proxies provides an additional layer of defense by filtering out malicious traffic before it reaches the target server. Acting as gateways, firewalls, and proxies inspect incoming traffic, blocking or allowing connections based on predefined rules. This approach adds an extra layer of protection, reducing the likelihood of successful SYN Flood attacks.
9. Honeypots & Honeynets
Honeypots and honeynets are proactive measures designed to divert and study malicious activity, including SYN flood attacks.
Honeypots
A honeypot is a decoy system or service strategically placed within a network to attract and trap attackers.
When a SYN flood attack is detected, the honeypot absorbs the malicious traffic, diverting the attack from the production servers.
Honeypots act as a sacrificial element, absorbing and diverting attacks, providing a valuable distraction for attackers, and protecting critical infrastructure.
Honeynets
A honeynet expands on the honeypot concept by deploying a network of interconnected honeypots. This allows for a more comprehensive study of attackers’ behavior across multiple simulated systems.
Honeynets provide a broader view of attack patterns, enabling security teams to analyze and understand potential attackers’ tactics, techniques, and procedures (TTPs).
Honeynets contribute to threat intelligence by gathering data on attackers’ strategies and can aid in the development of more effective DDoS protection.
10. Hybrid Approaches
Combining multiple techniques creates a layered defense against TCP SYN Flood attacks, ensuring that others can still protect if one method fails. Organizations can create a more resilient defense strategy by combining filtering, backlog adjustment, SYN-RECEIVED timer optimization, SYN caching, and SYN Cookies.
11. Cloud-based DDoS Protection Solutions
Leveraging cloud-based DDoS protection solutions can offload traffic and filter to specialized platforms capable of handling large-scale attacks.
These solutions can often absorb and filter malicious traffic before it reaches the target infrastructure.
Traditional mitigation responds to DDoS threats only upon acknowledgment, often leading to late detection and disruption. Some solutions may block only a portion of SYN flood attacks, rendering them ineffective against increasing packet volumes.
Though crucial, network-based firewalls and IPS devices fall short against sophisticated attacks.
Comprehensive DDoS protection requires a proactive, multifaceted approach. This involves offering inline and out-of-band traffic visibility, precise threat detection through various intelligence sources, a comprehensive threat database, customizable alerts, and scalability for diverse attack intensities.
Explore the features, advantages and limitations of top DDoS protection software in the market, here.
Stay tuned for more relevant and interesting security updates. Follow Indusface on Facebook, Twitter, and LinkedIn

 January 25, 2024
January 25, 2024



