Yahoo Data Breach: Can It Affect Your Business?
In this recent massive breach, hackers managed to steal email ids, passwords, birthdates and telephone numbers of half a billion users. Just a week before Yahoo confirmed the data breach, we published a detailed article on automated attacks explaining how hackers no longer only look for bugs or misconfigurations but also the ability to misuse valid functionality of the application to breach your network. Verizon DBIR of 2015 states “Pulling back from a single industry view, we find that most of the attacks make use of stolen credentials, which is a story we’ve been telling since 1 A.D. Over 95% of these incidents (web app attacks) involve harvesting credentials from customer devices, then logging into web applications with them.”
Credential stuffing is one of the simplest ways of exploiting application functionality. Hackers can easily purchase stolen credential lists and use them for automated attacks like credential stuffing.
What Is Credential Stuffing?
According to OWASP, credential stuffing is the automated injection of breached username/password pairs in order to fraudulently gain access to user accounts.
This is a subset of the brute force attack category where large numbers of credentials are automatically entered into websites until they are potentially matched to an existing account, which the attacker can use to hijack the account.
With tools such as Sentry MBA readily available to hackers, credential stuffing is one of the most popular attack vectors used by hackers given its simplicity. It automates the process of testing millions of username/password combinations to see which ones work.
Source- 1 OWASP ‘Automated Threat Handbook’ Web Applications
How can Yahoo’s Data Breach affect your web applications?
People often reuse credentials for their email, banking, social media, and online shopping accounts. In fact, according to a survey conducted on 2,000 consumers in the U.S. and the U.K by mobile identity company TeleSign, nearly 3 out of 4 consumers use duplicate passwords, many of which have not been changed for five years or more.
If a hacker has access to 500 million Yahoo credentials, that individual can configure an automated tool like Sentry MBA to run this set of credentials on your web applications. With every successful attempt, he puts your brand in jeopardy and your customers’ personally identifiable information at risk. Even if the match rate is only 1- 2%, the data breach could affect thousands of your customers.
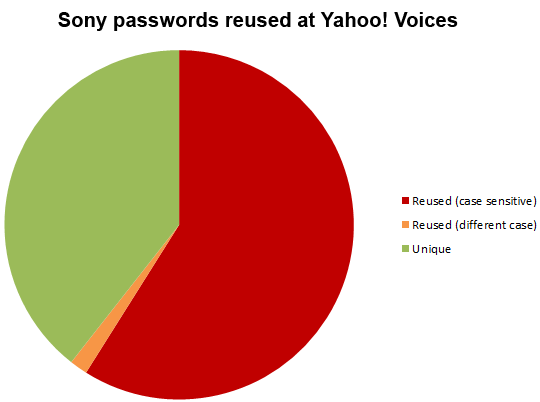
For example, in 2012, Yahoo Voices was the target of a similar data breach that exposed email addresses and passwords of 453,491 users. Surprisingly, just one year prior, Sony user accounts were also breached. The data breach analysis (conducted by Microsoft MVP Troy Hunt) showed that 59% of Yahoo users were using the identical password in their Sony accounts.
While hackers can target any business with such automated attacks, they tend to gravitate towards small and mid-sized enterprises (as reported in the Verizon report) for lower resistance due to the following weaknesses:
- Lack of time, budget, and expertise to implement comprehensive security defenses
- No dedicated IT security specialist on the payroll
- Lack of risk awareness
- Lack of employee training
- Failure to keep security defenses updated
- Failure to secure endpoints
How to protect your web applications against such attacks?
According to the OWASP ‘Automated Threat Handbook’, application owners can identify such attacks with the following symptoms.
- High number of failed login attempts
- Increased customer complaints of account hijacking through help center or social media outlets.
Organizations looking for a holistic approach to application security need to consider identifying vulnerabilities in web applications as well as the risks associated with the most sought after attack vector– automated attacks.
Indusface AppTrana helps businesses detect, protect and monitor such application-layer threats including automated attacks. Offered as a service, it provides full management of the operation using subject matter experts at a fraction of the cost of hiring an in house team. It includes:
- Latest security notification to protect your applications from known vulnerabilities
- Periodic penetration testing
- Business logic tests on all applications to find vulnerabilities, zero-day threats, and automated application risks
- Custom WAF rules to block attacks (via virtual patching). Keep in mind that Verizon’s DBIR stated that 70-90% of all malware samples are unique to an organization.
- Tracking the malicious behavior of an attacker initially versus simply blocking the attack.
- 24*7 monitoring to gather information such as IP address, User ID if authenticated, GEO location, navigation/user behavior and machine fingerprint that can help gain intel about the attacker’s methodologies to use that information in creating more aggressive blocking rules from these attackers.


 September 28, 2016
September 28, 2016






