What is a False Positive?
A false positive occurs when a security tool incorrectly identifies a legitimate activity as a threat. For example, a fraud detection system could wrongly flag and block a legitimate online transaction, assuming it to be fraudulent. These false alarms can occur across various security solutions, including a Web Application and API Protection Solution (WAAP), a Web Application Firewall (WAF), intrusion detection systems (IDS/IPS), antivirus software and SIEM platforms.
Not surprisingly, false positives have many repercussions. The cost of fixing them is high, but the bigger impact comes from alert fatigue, strained collaboration between security and app teams, and wasted resources leading to business disruptions.
False Positives vs. False Negatives
False positives and false negatives are two sides of the same challenge. A false positive mistakenly flags a benign action as malicious, while a false negative fails to detect a genuine threat, allowing it to bypass security defences.
Both are problematic—false positives lead to wasted resources and inefficiencies, while false negatives expose organizations to potential breaches. Striking a balance between security sensitivity and accuracy is critical in preventing both types of errors.
Why Most WAF Providers Struggle with False Positives?
Web Application Firewalls (WAFs) are designed to protect applications from cyber threats, yet many providers struggle with false positives. Most studies show that, on average, only 53% of WAF tools are deployed in block mode due to concerns about false positives and misconfigurations that could disrupt applications.
A WAF operating in log mode is essentially a glorified log analysis tool rather than an effective security measure. Without blocking capabilities, it fails to stop critical attacks such as SQL injections, code injections, and bot-driven threats, leaving applications vulnerable.
The root causes of false positives vary, but they often stem from overly aggressive security settings and limitations in detection methods. Below are the primary causes of false positives:
1. Rigid Security Rules That Don’t Adapt to Business Needs
Most WAF providers implement predefined security rules to detect and block threats. However, these rules are often too rigid and fail to accommodate application-specific behaviours.
Why This Happens:
- One-size-fits-all approach: Many WAFs rely on generic rule sets that don’t consider unique business logic or user interactions.
- Strict filtering criteria: A form submission with special characters might be flagged as an XSS attempt, even if it’s a normal customer inquiry.
- Default configurations: Many WAFs deploy with aggressive default settings, which can lead to over-blocking if not properly tuned.
2. Reliance on Outdated Signature-Based Detection
Most traditional WAFs depend on signature-based detection, where traffic is compared against a database of known attack patterns. This method is effective against known threats but struggles with:
- False positives from benign traffic that resembles an attack pattern. E.g., a sudden surge in login attempts may be flagged as a brute-force attack when it’s just a marketing campaign driving high traffic.
- Zero-day vulnerabilities that don’t match existing signatures.
Why This Happens:
- Signature-based WAFs fail to adapt to new attack vectors or custom business logic.
- Legitimate API calls or complex queries might match known attack signatures and get blocked.
- The delay in updating attack signatures means organizations remain vulnerable until a new signature is added.
To reduce false positives, AppTrana WAAP supplements signature-based detection with behavioural analysis and AI-driven threat intelligence.
3. Integration Issues Between Security Solutions
Modern security environments use multiple tools, such as WAF, endpoint protection, SIEMs, and fraud detection systems. When these tools are not properly integrated, they may generate conflicting or redundant alerts. Common integration challenges include:
- Inconsistent threat intelligence: Different security tools may use separate databases for identifying threats, causing discrepancies in threat classification.
- Redundant alerts from multiple sources: The same security event may be flagged by different tools, leading to excessive alerts for a single incident.
- Mismatched policies: If security policies differ between tools (e.g., a firewall blocking traffic while a SIEM marks it as safe), false positives can increase.
To overcome these challenges, organizations should adopt unified security solutions that integrate scanning, monitoring, threat intelligence, and attack prevention into a single platform. This approach reduces redundant alerts, ensures consistent threat detection, and improves overall security efficiency.
4. Inability to Differentiate Between Good Bots and Malicious Bots
Many WAFs struggle with bot detection, often blocking good bots while failing to catch evasive bad bots.
Why This Happens:
- Traditional WAFs lack advanced bot management, leading to unnecessary blocking of search engine crawlers and partner APIs.
- Evasive bots, such as those used for credential stuffing, can bypass simple WAF defences.
Instead of relying on static rules, AppTrana enables user-defined bot policies, where bot scores dynamically adjust based on anomalies—such as excessive product views in an e-commerce site. With granular control, businesses can apply different bot score thresholds for various sections of their application, ensuring a smooth user experience in areas like product browsing while enforcing stricter security on sensitive pages like checkout.
Additionally, AppTrana’s behavior-based detection leverages IP reputation, user agents, and past WAF interactions to refine bot identification, reducing false positives without compromising security.
5. Challenges in Virtual Patching for Zero-Day Vulnerabilities
Most WAF providers promote virtual patching as a solution for zero-day vulnerabilities. However, if not implemented correctly, virtual patches can generate false positives.
Why This Happens:
- Overly broad virtual patches can block legitimate application functions.
- Poor rule optimization leads to disruptions in critical services.
- Delayed or inaccurate patch deployment results in either false positives or missed attacks.
To avoid these issues, businesses should choose a WAF with built-in false positive monitoring. Real-time monitoring and expert-driven adjustments help minimize disruptions, allowing organizations to maintain security without compromising functionality.
If you want to understand WAF fundamentals and why they matter, read our blog How Does a WAF Work?
What are the Impacts of False Positives in WAF?
1. Business Disruptions and Revenue Loss
When a WAF blocks legitimate transactions, businesses can face financial losses, especially in industries like e-commerce, banking, and SaaS.
- Blocked Transactions – Customers may abandon purchases if payment requests or login attempts are blocked.
- Service Downtime – If API calls between integrated platforms are flagged, critical services may fail, leading to business downtime.
- Increased Cart Abandonment Rates – E-commerce users facing access issues may switch to competitors.
2. Poor User Experience and Customer Frustration
False positives can create unnecessary friction for users, leading to complaints and loss of trust.
- Login Issues – Users may be blocked from accessing accounts due to strict authentication rules.
- Frequent CAPTCHA Challenges – Excessive security challenges frustrate users and deter engagement.
- Blocked API Access – Developers and business partners may face disruptions when APIs are flagged incorrectly.
3. Increased Security Team Workload
High false positive rates lead to alert fatigue, where security teams waste time reviewing and resolving unnecessary alerts.
- Higher Manual Review Efforts – Security teams must analyse false alerts instead of focusing on real threats.
- Delayed Incident Response – Increased workload slows down response time for genuine security incidents.
- Risk of Ignoring Critical Alerts – Repeated false positives can desensitize teams, leading to missed real attacks.
4. Operational Inefficiencies and Productivity Loss
False positives can block internal applications, APIs, or workflows, impacting employee productivity.
- Restricted Internal Access – Employees may be blocked from internal dashboards, CRM tools, or collaboration platforms.
- Delayed Development & Testing – Developers may struggle to test APIs and features due to excessive security restrictions.
- Increased IT Support Requests – Teams spend time troubleshooting WAF-related access issues.
5. Reputation Damage and Customer Churn
Customers expect smooth digital experiences. Persistent access issues can drive them to competitors.
- Loss of Trust – Users may perceive the business as unreliable or difficult to use.
- Negative Reviews & Complaints – Frustrated customers may leave bad reviews, affecting brand reputation.
- Competitor Advantage – Businesses with smoother digital experiences can attract dissatisfied users.
How to Reduce False Positives in WAF?
1. Fine-Tune Security Rules Based on Application Behaviour
Instead of using a one-size-fits-all approach, fine-tune security policies based on:
- Application-specific traffic patterns – Understand normal API calls, form submissions, and user interactions.
- Custom allowlists – Permit legitimate queries that trigger false positives, such as certain SQL or JavaScript inputs used in application features.
- Exclusion lists – Exempt known safe URLs, parameters, or IPs from specific security rules.
2. Implement Context-Aware Security Policies
Many false positives occur because WAFs analyse individual requests without considering the broader user session. Improve detection accuracy by:
- Tracking user behaviour over time – Identify patterns that distinguish normal activity from attacks.
- Using machine learning-based threat detection – Adaptive security models can dynamically adjust rules based on real-time traffic.
- Correlating with threat intelligence feeds – Identify legitimate security events versus known attack behaviours.
3. Adopt a Risk-Based Approach to Blocking
Instead of outright blocking all suspicious traffic, WAFs should use risk-based policies to evaluate the severity of each request. Key techniques include:
- Integrate Scanner with WAF – Combining DAST with WAF enables real-time detection and mitigation of application-specific vulnerabilities.
- Challenge-response mechanisms – Use CAPTCHAs or JavaScript challenges for borderline cases rather than blocking outright.
- Risk scoring – Assign risk scores based on IP reputation, geolocation, and behavioural analysis.
- Soft blocking (monitoring mode) – Test new WAF rules in logging mode before enforcing strict blocking policies.
A WAAP platform that combines both DAST scanning and WAF provides IT teams with visibility into open vulnerabilities and how many are already protected by the WAF. This risk-based approach, pioneered by AppTrana WAAP, ensures proactive security while minimizing false positives.
4. Optimize Virtual Patching for Zero-Day Threats
As mentioned virtual patching helps prevent exploits before official fixes are available, but overly broad patches can block legitimate users. Best practices include:
- Granular patching – Focus on specific exploit patterns rather than generic rules that affect normal functionality.
- Monitoring before enforcement – Test patches in alert-only mode before enabling full blocking.
- Risk-based patching – Prioritize patches based on the likelihood of exploitation in your environment.
Additionally, choose a WAF with real-time analytics and dashboards to gain visibility into blocked traffic, false positives, and emerging attack trends, enabling proactive security adjustments.
5. Improve Bot Detection Mechanisms
WAFs often misclassify good bots (e.g., Googlebot, API calls) as malicious traffic. Prevent this by:
- Maintaining an updated bot allowlist – Ensure search engine crawlers and partner integrations are not mistakenly blocked.
- Using behavioural analysis – Detect bot-like patterns such as high request rates, headless browsers, and automated interactions.
- Differentiating between good and bad bots – Implement bot fingerprinting and user behaviour analytics.
6. Leverage Content Security Policy (CSP) for XSS Protection
To avoid blocking legitimate user inputs, use CSP instead of solely relying on WAF-based XSS filters. CSP helps:
- Prevent unauthorized script execution – Blocks inline scripts and content injections without blocking valid inputs.
- Reduce false positives in input validation – Ensures legitimate HTML and JavaScript inputs are not mistakenly flagged.
- Improve client-side security without affecting backend traffic.
7. Enable Adaptive Learning and Automated Tuning
Manually adjusting WAF rules can be time-consuming. Automate tuning with:
- AI-powered anomaly detection – Automatically refines security policies based on user behavior.
- Feedback loops – Allow security teams to mark false positives and adjust rules dynamically.
- Adaptive rate-limiting – Prevents excessive false positives by adjusting thresholds based on normal user activity.
8. Integrate WAF with SIEM and Threat Intelligence
Standalone WAF logs can be misleading. Improve detection accuracy by:
- Correlating WAF logs with SIEM data – Gain deeper insights by analysing traffic patterns alongside broader security telemetry.
- Using real-time threat intelligence – Identify whether flagged activity aligns with known attack campaigns.
- Automating incident response – Reduce alert fatigue by prioritizing high-confidence threats.
9. Conduct Regular False Positive Analysis and Testing
Continuous testing is essential for reducing false positives. Best practices include:
- Red teaming and penetration testing – Simulate real-world attacks to ensure only malicious activity is blocked.
- False positive audits – Regularly review blocked requests and adjust security policies accordingly.
- User feedback mechanisms – Allow internal teams to report legitimate transactions being blocked.
How AppTrana WAAP Eliminates False Positives
AppTrana WAAP ensures zero false positives while maintaining 100% block mode deployment through risk-based assessment, continuous learning, and expert-driven tuning. Unlike traditional WAFs, it blocks only real threats without disrupting legitimate traffic.
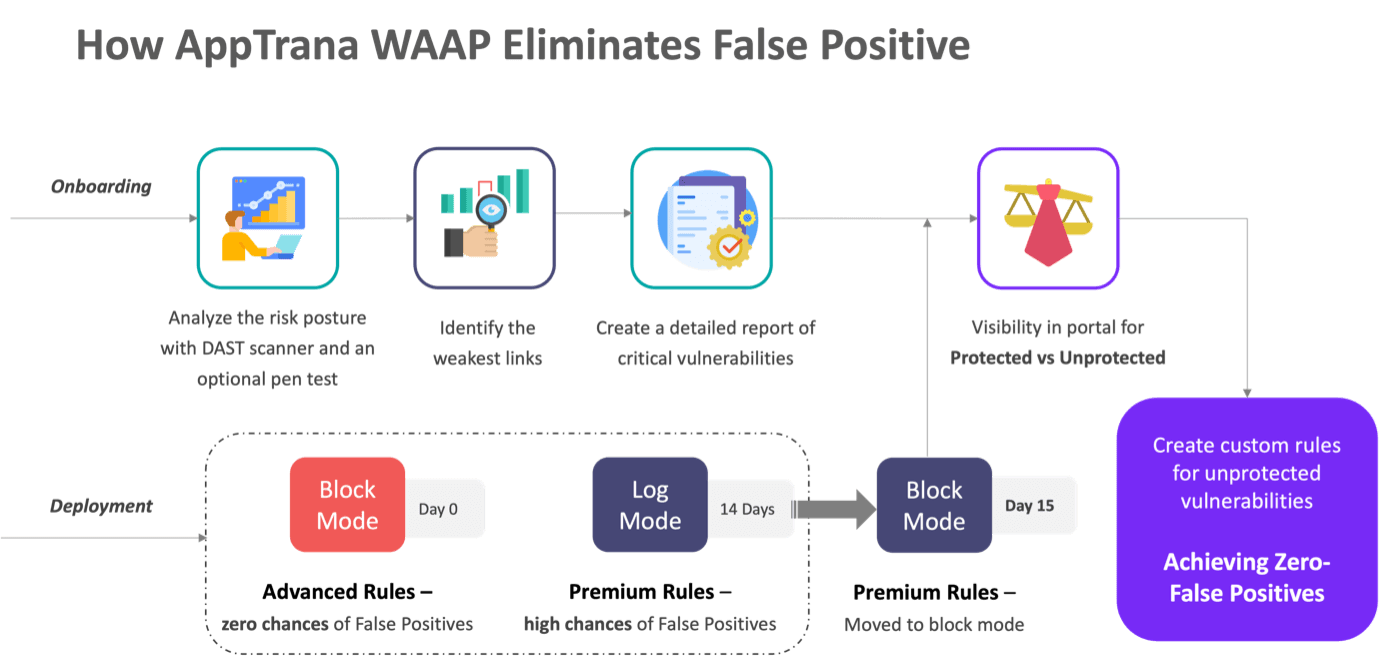
The process begins with a comprehensive security assessment, combining automated vulnerability scanning and manual penetration testing. Instead of relying on generic signatures, AppTrana builds a risk-based protection model, ensuring that only confirmed attack patterns are blocked from day one.
To eliminate false positives, every application onboarded undergoes a 14-day observation period, during which AppTrana’s solution engineering team fine-tunes security policies based on real-world traffic.
Even after deployment, false positive monitoring is provided as a managed service. The security researchers act as an extended SOC team, continuously monitoring traffic and refining rules to maintain a zero false positive guarantee. This eliminates the common challenge of WAFs being kept in log mode due to fear of breaking applications, ensuring robust security without operational friction.
AppTrana also incorporates behavioural traffic analysis and anomaly detection to distinguish between malicious requests and legitimate variations of user behaviour. If a rule triggers unexpectedly, security analysts work closely with customers to validate the request patterns. Instead of disabling broad protections, custom rules are implemented to accommodate application-specific needs while keeping attack vectors blocked.
For API security, AppTrana WAAP leverages a positive security model by using OpenAPI specifications and Swagger documentation to ensure that only well-defined, expected request structures are allowed. This eliminates common API-related false positives and ensures accurate request validation.
With this expert-managed, intelligence-driven approach, AppTrana eliminates the trade-off between security and usability, delivering seamless protection without blocking legitimate users.


 AppTrana WAAP Platform
AppTrana WAAP Platform

