The Domain Name System (DNS) is an essential component of the internet, functioning as a decentralized naming system that translates human-readable domain names into machine-readable IP addresses. This key function ensures smooth access to websites and services for users.
However, DNS is also a prime target for various cyberattacks, making DNS security a top priority for organizations. This blog will explore the common DNS risks, the importance of DNS security, and best practices for enhancing DNS protection.
What is DNS Security?
DNS security refers to the measures taken to protect the DNS infrastructure from various threats and vulnerabilities. This includes protecting DNS servers, records, and queries from unauthorized access, tampering, and attacks.
Effective DNS protection ensures the integrity, availability, and confidentiality of DNS services, helping to maintain a secure online environment.
To value DNS security, it’s crucial to understand how DNS operates:
- Translation of Domain Names: When a user types a domain name into their web browser, the DNS resolver queries the DNS system to obtain the corresponding IP address. This process involves multiple steps, including querying recursive and authoritative DNS servers.
- Caching Mechanism: DNS resolvers cache responses to reduce the time taken for subsequent queries to the same domain. This caching mechanism improves performance but can also lead to vulnerabilities if not managed properly.
Given its central role in internet functionality, any disruption or compromise in DNS can have significant consequences.
What Are the Common Threats Involving DNS?
Vulnerabilities in the DNS infrastructure can expose organizations to various cyber threats. The following are some of the most common DNS threats:
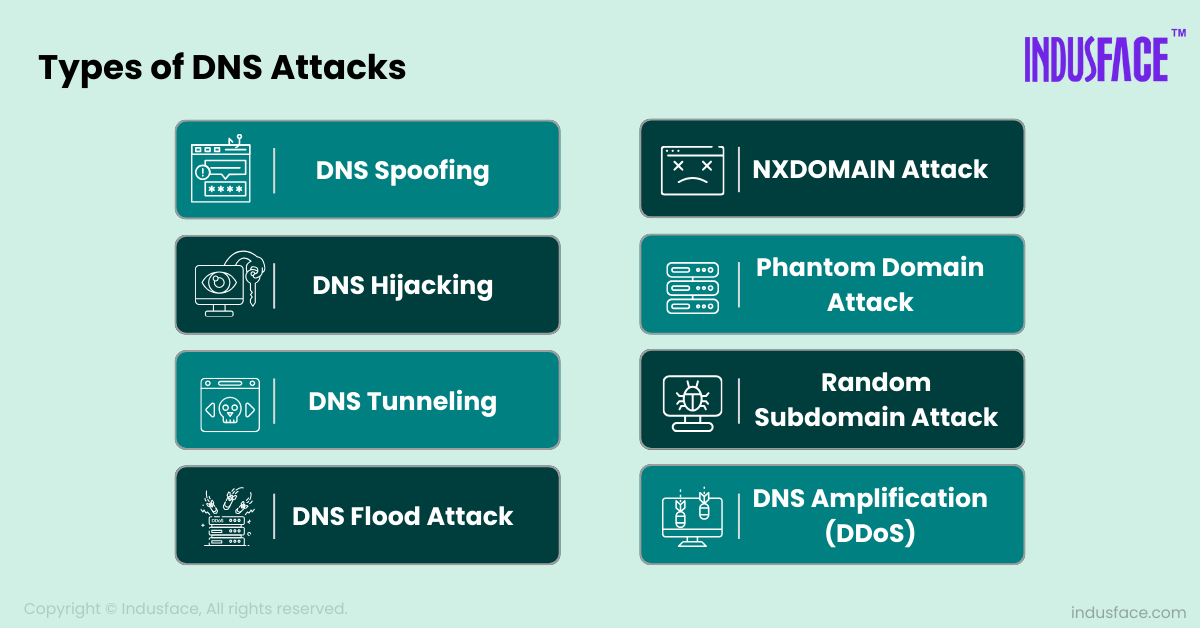
DNS Spoofing
In DNS Spoofing attackers inject false information into a DNS resolver’s cache, causing users to be redirected to fraudulent or malicious websites. This attack can result in phishing, malware installation, or credential theft.
DNS Amplification (DDoS)
In this DDoS attack, the attacker exploits DNS to overwhelm the target with excessive traffic. It works by sending small requests to open DNS resolvers, which are servers that respond to DNS queries. These requests are crafted in such a way that the responses are significantly larger than the original requests, often by a factor of 50 or more.
You can also check out DNS amplification attacks in detail.
DNS Tunneling
DNS tunneling leverages DNS as a covert channel to tunnel unauthorized data, such as commands to compromised systems or exfiltration of sensitive data, bypassing network security controls that may not inspect DNS traffic closely.
DNS Hijacking
Attackers manipulate DNS queries to redirect users from legitimate websites to malicious sites. They achieve this by compromising DNS settings on routers or user devices, allowing them to steal credentials or inject malware. Learn more about how to mitigate DNS hijacking attacks here.
NXDOMAIN Attack
In this attack, attackers send numerous requests for non-existent domain names, overwhelming the DNS server. The server spends resources looking up these fake domains, potentially slowing down or crashing due to the volume of requests. Learn more about NXDomain Attack.
DNS Flood Attack
Attackers overwhelm a DNS server with a high volume of requests, consuming its resources and causing it to become slow or unresponsive. This can be part of a larger DDoS attack. Check out how to prevent a DNS flood attack.
Phantom Domain Attack
Malicious domains respond slowly or not at all to DNS queries, forcing the recursive resolver to wait, which ties up resources and slows down the performance for legitimate queries. Learn more about Phantom Domain Attack.
Why is DNS Security Important?
Compromised DNS servers can lead to significant service outages, preventing customers from accessing websites and online services, resulting in lost revenue and diminished customer trust. Ensuring DNS security helps minimize downtime and allows for faster recovery from attacks.
Moreover, DNS protection safeguards sensitive information. As mentioned, attackers can manipulate DNS responses, redirecting users to malicious sites that steal personal and financial data. By implementing strong DNS layer security, organizations can ensure users reach legitimate websites, protecting their information from theft.
Various regulations, such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS), mandate robust security measures, including those related to DNS. Insufficient Domain name system security can lead to compliance violations, legal penalties, and reputational harm.
A single security incident can have lasting repercussions on an organization’s reputation. By investing in DNS security, organizations can mitigate breach risks and safeguard their brand image.
What are Common Mistakes to Avoid in DNS Security?
- Neglecting Regular Updates and Patching: Failing to keep DNS software and hardware updated can leave systems exposed to known vulnerabilities. Regular updates and patches are essential to protect against exploits targeting outdated systems.
- Insecure DNS Configuration: Poorly configured DNS settings can lead to vulnerabilities. For instance, allowing zone transfers from unauthorized IP addresses or using default settings can create risks. Properly configuring DNS servers is essential for security.
- Not Using Redundancy: Relying on a single DNS server can create a single point of failure. Implementing redundant DNS servers ensures continued service availability in case of an attack or server failure.
- Neglecting High Availability Architecture : Depending on a single DNS provider exposes your domain to potential outages, attacks, or configuration errors. To enhance redundancy and resilience, it’s advisable to utilize multiple DNS providers, ensuring that if one fails, the others can continue to provide service.
Best Practices for DNS Security
Regularly Update DNS Records
Maintaining updated DNS records is crucial in preventing unauthorized access and guaranteeing users reach the correct services. Regular audits of DNS configurations help identify and rectify any vulnerabilities.
Monitor DNS Traffic
Implementing DNS traffic monitoring can help detect anomalies that may indicate an ongoing attack. Using security information and event management (SIEM) tools can provide valuable insights into DNS activity and enable organizations to respond promptly to threats.
Limit Zone Transfers
Restricting zone transfers to authorized IP addresses only can minimize the risk of attackers obtaining sensitive DNS information. This control helps ensure that only trusted servers can access complete zone files.
Enable Rate Limiting
Rate limiting helps control the number of requests sent to DNS servers, reducing the risk of DDoS attacks and ensuring service availability during traffic spikes. Configuring limits on DNS queries per user or IP address can enhance resilience.
DNS Firewalls
DNS firewalls act as a protective barrier, filtering DNS requests and blocking access to known malicious domains. They help reduce the risk of phishing and malware infections by preventing users from reaching harmful sites.
Threat Intelligence Services
Utilizing threat intelligence services provides organizations with up-to-date information about known threats and vulnerabilities. This proactive approach enables organizations to defend against emerging DNS threats effectively.
Implement Redundancy
Creating a redundant DNS infrastructure by deploying multiple DNS servers across different geographic locations enhances resilience. In the event of a compromise or downtime on one server, the remaining servers can continue to serve DNS queries, guaranteeing uninterrupted service.
Use DNS over HTTPS (DoH) or DNS over TLS (DoT)
Both DoH and DoT encrypt DNS queries, preventing eavesdropping and man-in-the-middle attacks. By protecting DNS queries from interception, the implementation of these protocols enhances user privacy and security.
Implement DNSSEC (Domain Name System Security Extensions)
DNSSEC verifies the authenticity of responses from name servers to clients using digital signatures. By adding cryptographic signatures to DNS records, DNSSEC secures data in the DNS. It ensures that the DNS resolver checks the signature of each record for authenticity before delivering responses to clients, with all records needing to match those on the authoritative DNS server. However, DNSSEC introduces complexity and management overhead, requiring continuous maintenance.
How AppTrana DNS Management help with DNS Security?
With AppTrana DNS management, users can easily manage DNS records and hosted zones while benefiting from improved security through DNSSEC protocols that protect against vulnerabilities.
As a result, users’ DNS requests will contain digital signatures and encryption, guaranteeing the legitimacy and immutability of the responses they receive.
The dedicated managed service team assists with implementing DNSSEC, allowing you to focus on your core business while ensuring strong DNS security.
Further, its reporting feature makes it easier to monitor and maintain the DNS records for ongoing security benefits. It offers a visual summary of the requests processed for a domain, along with any errors that occurred. Customers can:
- View the total number of requests handled
- Track the overall count of detected errors
- Identify NX domain errors (when the DNS fails to resolve the domain name to an IP address)
- See the total number of server failures (when the domain name can’t connect to an IP address)
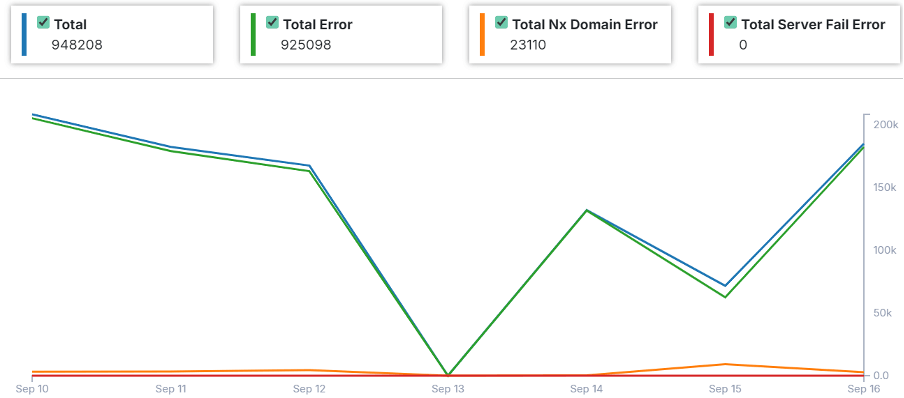
This data helps customers monitor domain activity and take immediate action to enhance performance.


