As modern applications shift towards flexibility and scalability, NoSQL databases like MongoDB have gained immense popularity. While their schema-less architecture offers unmatched adaptability, it also introduces unique security risks.
One of these is NoSQL injection—a vulnerability that allows malicious actors to manipulate database queries.
What is NoSQL Injection?
NoSQL injection is a security vulnerability that allows attackers to manipulate NoSQL database queries by injecting malicious input. Unlike traditional SQL injections targeting structured query language (SQL) databases, NoSQL injection exploits the flexibility of NoSQL query structures. These attacks can lead to unauthorized access, data theft, or application disruption.
How Does NoSQL Injection Work?
NoSQL databases often use JSON-like syntax for queries. In insecure implementations, user input directly incorporated into these queries can manipulate the database behavior. Since NoSQL databases lack a fixed query structure, validating inputs becomes challenging, increasing the likelihood of injection vulnerabilities.
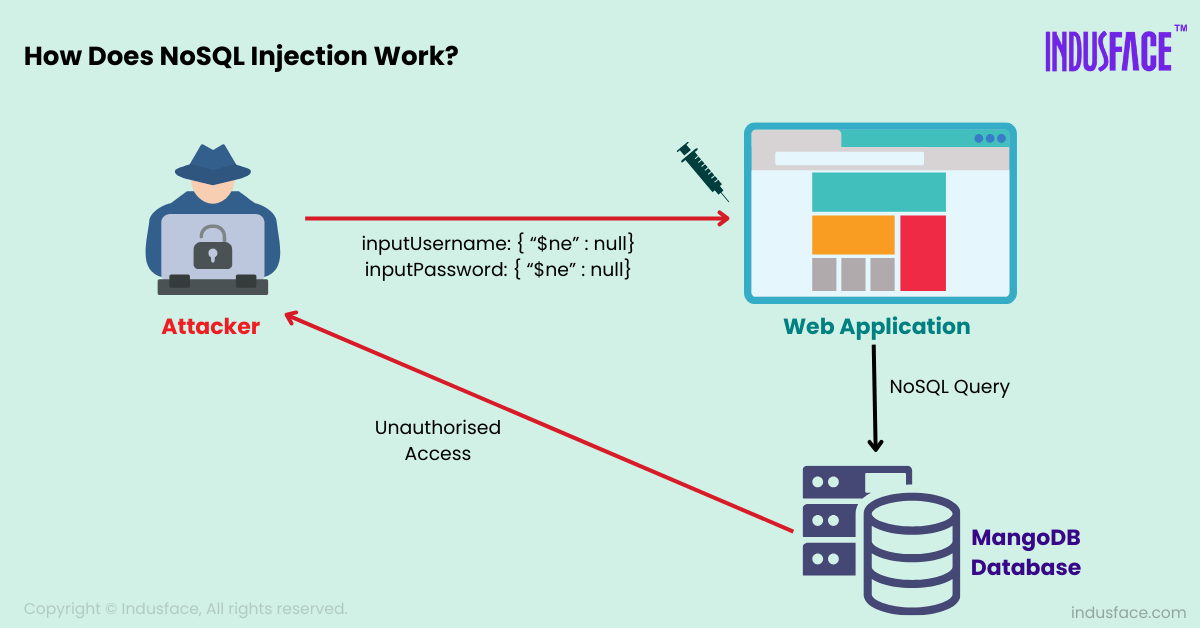
For example, consider a MongoDB query that authenticates users:
let user = db.users.findOne({ username: inputUsername, password: inputPassword });
If inputUsername and inputPassword are directly taken from user input without validation, an attacker could supply a malicious payload like:
inputUsername: { "$ne": null },
inputPassword: { "$ne": null }
The resulting query:
let user = db.users.findOne({ username: { "$ne": null }, password: { "$ne": null } });
This query would return the first user in the database, effectively bypassing authentication.
Blind NoSQL Injection
Blind NoSQL injection is a variant where attackers do not receive direct feedback from the database but infer information through carefully crafted queries and observing the application’s behavior. This technique is particularly challenging to detect because it relies on indirect clues rather than explicit error messages.
Example: Extracting Data with Blind MangoDB NoSQL Injection
Consider a login form with the following query:
let user = db.users.findOne({ username: inputUsername, password: inputPassword });
An attacker might test the application’s behavior by injecting:
inputUsername: "admin",
inputPassword: { "$regex": "^a" }
If the password starts with “a,” the application might behave differently (e.g., proceed to the next step). By iterating over different characters and observing responses, the attacker can reconstruct the password character by character.
Timing-Based Blind MangoDB NoSQL Injection
Attackers may also use timing-based methods to extract information. For instance, a query like this:
inputUsername: "admin",
inputPassword: { "$where": "sleep(5000) || this.password == 'knownPassword'" }
If the query introduces a delay, the attacker can deduce whether their injected logic was successful.
Other Common Exploitation Techniques of NoSQL Injection
Boolean-Based Injection
Attackers manipulate query conditions to extract sensitive data by observing application behavior. For example, injecting queries like {“$ne”: null} can bypass authentication checks.
Union-Like Queries
Attackers exploit query operators like $or to combine malicious inputs with legitimate queries. For example, injecting {“$or”: [{“username”: “admin”}, {“password”: “any”}]} to bypass authentication.
Query Parameter Tampering
Attackers manipulate query parameters directly, injecting payloads that modify the intended query logic. For example, altering a query expecting a username to include { “username”: {“$gt”: “”} }.
Exploitation of Query Language Features
NoSQL databases like MongoDB and CouchDB support dynamic query structures. Attackers can inject scripts or use operators like $regex to extract sensitive information or bypass filters.
Exploiting Poor Input Validation
Applications that fail to validate and sanitize user inputs may allow malicious query injection. For instance, inserting { “key”: {“$eq”: “malicious_payload”} } into an unsanitized field can manipulate database operations.
MongoDB NoSQL Injection: Examples
Authentication Bypass
Assume an application login form processes user credentials as follows:
let user = db.users.findOne({ username: inputUsername, password: inputPassword });
An attacker enters the following payload in the inputUsername field:
{ "$or": [ { "username": "admin" }, { "password": "12345" } ] }
This transforms the query into:
let user = db.users.findOne({ username: { "$or": [ { "username": "admin" }, { "password": "12345" } ] }, password: inputPassword });
This query would likely return an unintended user, bypassing authentication.
Data Extraction
Consider a search feature using the following query:
let results = db.products.find({ name: inputName });
An attacker could inject:
{ "$regex": "" }
This creates a query:
let results = db.products.find({ name: { "$regex": "" } });
The $regex operator matches any string, potentially exposing all documents in the products collection.
How to Test for NoSQL Injection Vulnerability?
Testing for NoSQL Injection involves several steps to identify whether an application is vulnerable to malicious queries in NoSQL databases (e.g., MongoDB, CouchDB, Cassandra). Here’s a guide on how to test for NoSQL injection vulnerabilities:
Injection Points: Identify where user input is improperly passed into NoSQL queries, such as login forms, search fields, or URL parameters.
Input Validation: Test for insufficient input validation that allows attackers to inject malicious queries, including $gt, $lt, $regex, or other operators in MongoDB or similar NoSQL systems.
Authentication Bypass: Attempt to bypass authentication mechanisms by injecting payloads that manipulate user credentials or circumvent checks.
Data Exfiltration: Test whether attackers can use injection techniques to extract sensitive data from the database, such as user information or API keys.
Error-Based Feedback: Check whether the application leaks error messages from the NoSQL database, which may reveal insights into the database structure and vulnerabilities.
Privilege Escalation: Attempt to escalate privileges by injecting queries that manipulate database permissions or user roles.
Injection via APIs: Evaluate API endpoints interacting with the NoSQL database to identify potential injection flaws in requests and responses.
NoSQL-Specific Payloads: Test with specific NoSQL injection payloads that exploit NoSQL query syntax, such as JSON objects, regular expressions, or NoSQL operators.
How To Prevent NoSQL Injection?
NoSQL injection vulnerabilities arise from failing to properly handle untrusted inputs. To mitigate this risk, you can implement the following security best practices:
1. Input Validation and Sanitization
Ensure that all user inputs are validated and sanitized before being processed by the database.
Use Whitelisting: Allow only specific, expected inputs (e.g., numeric values, alphanumeric strings).
Reject Malicious Characters: Filter out special characters like $, {, }, [], and ;, which attackers use to craft injection payloads.
Restrict Query Syntax: Do not accept raw or unstructured user inputs for query construction.
2. Use Parameterized Queries
Implement parameterized queries or prepared statements to separate query logic from input data. Parameterized queries treat input data as literals, preventing it from being interpreted as part of the query logic.
Supported Drivers: Most NoSQL databases, such as MongoDB, provide query frameworks that support parameterized queries.
3. Escape Special Characters
Escape characters like $ and { to prevent them from being interpreted as operators.
Example:
Use a library like mongo-sanitize to clean inputs:
const sanitize = require('mongo-sanitize');
let sanitizedInput = sanitize(userInput);
4. Apply Strong Authentication and Authorization
Prevent unauthorized access to sensitive operations by enforcing strict user authentication and role-based access controls.
Use Unique Accounts: Assign specific database users for each application function with minimum required privileges.
Implement Multi-Factor Authentication (MFA): Add an extra layer of security for database access.
5. Enforce Input Encoding
Encode all inputs before processing them within NoSQL queries to neutralize special characters.
Context-Specific Encoding: For example, use JSON encoding to ensure special characters are safely interpreted as data and not query logic.
6. Avoid Direct User Input in Queries
Never use raw or dynamic user input directly in database queries.
Safe Alternative: Use a framework or middleware that enforces secure query construction.
7. Enable Logging and Monitoring
Track and monitor database activity to detect and respond to suspicious behavior.
Log Queries: Record all incoming queries to identify potential injection attempts.
Set Alerts: Configure alerts for unusual query patterns or high volumes of failed authentication attempts.
8. Limit Query Capabilities
Restrict the scope of queries that an application can execute.
Disable Dangerous Operators: Prevent the use of operators like $where, $regex, or $gt in queries, unless absolutely necessary.
Restrict Query Depth: Limit the complexity of queries to avoid maliciously crafted, resource-intensive operations.
9. Regularly Update Dependencies
Ensure that your NoSQL database, drivers, and associated libraries are always up-to-date.
Patch Known Vulnerabilities: Apply security patches as soon as they become available.
Monitor Advisories: Stay informed about new vulnerabilities in NoSQL platforms and related tools.
10. Implement a Web Application Firewall (WAF)
A WAF can provide an additional layer of defence to prevent MangoDB injection by inspecting and blocking malicious payloads before they reach the database.
Use Security Rules: Configure the WAF to detect and block NoSQL injection patterns.
Integrate with Your Database: Ensure that the WAF is aligned with your database structure and query syntax.
How AppTrana WAAP Prevents NoSQL Injection
AppTrana WAAP protects against injection attacks by analyzing incoming traffic to your web application and detecting any malicious queries. It then blocks the malicious requests before they reach your application, preventing the attack from being executed.
Using a combination of machine learning and behavioral-based detection techniques, AppTrana effectively identifies and mitigates NoSQL injection threats. Additionally, the managed service team continuously fine-tunes custom rules to identify and block specific threats, providing tailored protection against evolving attack vectors.
In addition, AppTrana provides real-time visibility and comprehensive reporting on all incoming traffic, enabling you to monitor activity on your application and quickly respond to potential security threats.


 AppTrana WAAP Platform
AppTrana WAAP Platform

