What is an Account Takeover Attack?
Account Takeover (ATO) is a form of identity theft where cybercriminals gain unauthorized access to a legitimate user’s online account. By exploiting the account, attackers can engage in fraudulent activities such as transferring funds, purchasing goods, stealing sensitive information, or launching additional attacks by impersonating the account owner.
ATO attacks target any type of online account, including financial services, e-commerce platforms, social media accounts, and enterprise systems, making them a significant threat to both individuals and organizations.
In this blog, we’ll explore what makes ATO attacks dangerous, how they work, and the best practices to prevent them.
How Do Account Takeover Attacks Work?
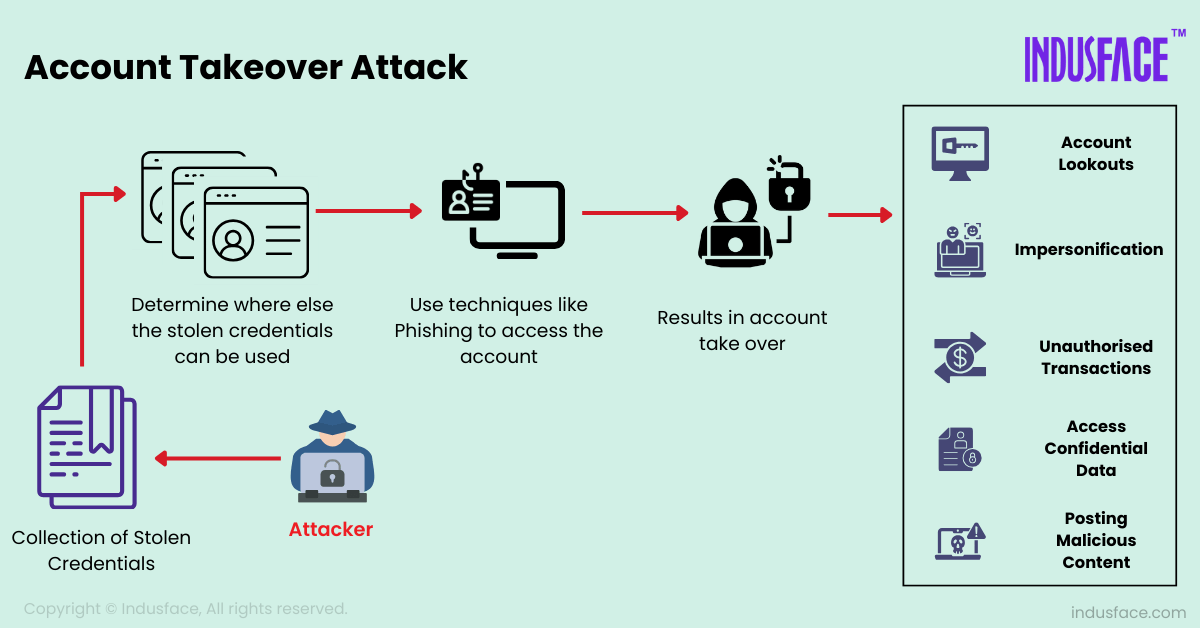
ATO attacks involve several steps, often employing sophisticated techniques to bypass traditional security measures.
1. Credential Theft
Attackers acquire account login credentials using various techniques, including:
- Phishing – Victims are tricked into sharing their credentials through fake emails, messages, or websites designed to mimic trusted entities.
- Data Breaches: Attackers use credentials leaked from large-scale data breaches, often buying them on the dark web.
- Credential Stuffing: Using automated tools, attackers try credentials stolen from one breach on multiple accounts, exploiting the common habit of password reuse. Botnets, or networks of compromised devices controlled by an attacker, can be used to carry out massive credential stuffing attacks. With thousands of bots at their disposal, attackers can automate login attempts on a large scale, increasing the chances of successfully breaching accounts.
- Malware: Keyloggers or other malicious software installed on the victim’s device capture usernames and passwords
- Cookie Theft – Attackers can steal session cookies, which are used to authenticate users on websites. With these cookies, attackers can bypass the login process entirely, gaining unauthorized access to accounts without needing credentials.
- Application Vulnerabilities – Weaknesses in an application’s code or logic can be exploited by attackers to gain access to user accounts. Common vulnerabilities like SQL injection, Cross-Site Scripting (XSS), or improper authentication mechanisms allow attackers to bypass security controls, steal data, or hijack accounts. A critical flaw in Hotjar, which combines XSS with OAuth, put millions of websites at account take over risk, exposing user data and increasing the likelihood of account takeovers. Learn how this vulnerability was exploited, here.
2. Account Access
Once the credentials are obtained, attackers attempt to log in to the victim’s account. Advanced attackers use tools to bypass multi-factor authentication (MFA) or leverage social engineering to manipulate support teams into granting access.
3. Exploitation of the Account
After gaining access, attackers exploit the account in numerous ways, such as:
- Transferring funds or making purchases in financial accounts
- Changing account details to lock out the legitimate user
- Harvesting sensitive data like credit card numbers or personal information
- Sending phishing messages or malware links to the victim’s contacts
- Selling access to compromised accounts on underground marketplaces
Why Are Account Takeover Attacks Dangerous?
Financial Loss
ATO attacks often lead to unauthorized transactions, fund transfers, and the misuse of stored payment information. The financial impact on individuals and organizations can be devastating.
Data Theft
Personal information stored in the compromised account can be stolen and used for further attacks, including identity theft.
Reputation Damage
When attackers misuse accounts to send spam or phishing messages, it damages the trust others have in the account owner. This is particularly harmful for businesses.
Legal and Compliance Challenges
To meet data protection regulations, businesses must prioritize ATO prevention. Failure to safeguard user accounts can lead to regulatory penalties, particularly under laws such as GDPR, PCI DSS, or CCPA. Many jurisdictions impose strict requirements for robust security measures to protect against such attacks.
How to Detect and Protect Against Account Takeover (ATO) Attacks
Detecting and preventing Account Takeover (ATO) attacks requires a multi-layered approach that combines advanced technology, proactive monitoring, and robust user education.
Detecting Account Takeover (ATO) Attacks
The ability to identify an ATO attack early can minimize damage and prevent unauthorized access from escalating. Below are detailed methods to detect ATO attempts effectively:
Behavioral Anomaly Detection
Behavioral monitoring uses machine learning (ML) and artificial intelligence (AI) to create a baseline of typical user behavior, then flags deviations.
What to Monitor:
- Unusual login times, such as a user logging in at midnight when they typically use the account during business hours.
- Logins from new or unexpected geographic locations.
- Rapid switching between multiple accounts on the same device, suggesting automated attacks.
Failed Login Monitoring
Attackers often attempt multiple login attempts to guess passwords or test credentials.
Indicators to Watch
- A high volume of failed login attempts over a short period, signaling brute force or credential stuffing.
- Login attempts with usernames that don’t exist in the system, a sign of reconnaissance efforts.
Response Mechanisms
- Implement temporary account locking after a defined number of failed attempts.
- Use alerting systems to notify administrators about suspicious patterns.
Device Fingerprinting
Device fingerprinting analyzes and records attributes like browser version, operating system, and IP address to identify familiar devices.
Detection Benefits
- New devices or altered device attributes prompt additional verification, like multi-factor authentication (MFA).
- Cross-referencing device fingerprints across multiple users can detect bot-driven attacks using the same infrastructure.
IP Reputation Analysis
Analyzing IP addresses of login attempts can identify high-risk traffic.
Steps to Detect:
- Flag login attempts originating from IPs with poor reputations, such as those used in known attack campaigns or suspicious regions.
- Compare IP addresses against threat intelligence feeds and blocklisted sources.
Unusual Transaction Detection
In accounts handling sensitive transactions, abnormal activity can signal an ATO attack.
Key Indicators
- Sudden large transactions that deviate from normal spending habits.
- Changing account settings, such as updating billing information or email addresses, without prior notice.
Protecting Against Account Takeover (ATO) Attacks
Prevention involves layered security strategies to address vulnerabilities in systems, processes, and user behavior. Below are detailed steps to mitigate the risk of ATO attacks:
Implement Strong Authentication Mechanisms
Authentication is the first line of defence against ATO attacks.
- Use at least two forms of verification, such as passwords combined with OTPs, biometrics, or hardware tokens.
- Implement adaptive MFA, which applies stricter checks for high-risk logins, such as those from unfamiliar locations.
- Leverage methods like WebAuthn or FIDO2 for secure, password-free logins.
- Reduce reliance on credentials that can be stolen or reused across platforms.
Strengthen Password Policies
Weak or reused passwords are a leading cause of ATO attacks. Here are some recommendations:
- Require passwords with a minimum length of 12 characters, including upper/lowercase letters, numbers, and symbols.
- Enforce regular password updates but balance it with usability—forcing too frequent changes can lead to insecure practices.
- Encourage users to adopt password managers to generate and store strong, unique passwords securely.
Monitor and Block Automated Threats
Automated attacks like credential stuffing and brute force attempts are common precursors to ATO. Implement the following measures:
- CAPTCHA Challenges: Thwart bots attempting repeated login attempts by requiring human verification.
- Rate Limiting: Restrict the number of login attempts from a single IP or account to slow down attackers.
- Bot Management Systems: Use AI to distinguish between human users and bots, blocking malicious activity while preserving the user experience.
Encrypt Sensitive Data
Encryption ensures that even if attackers gain access to account data, they cannot use it.
- Encrypt credentials and sensitive data both at rest (stored) and in transit (during communication).
- Use hashing algorithms like bcrypt or Argon2 for password storage, along with salting to resist brute force attempts.
Educate Users on Cyber Hygiene
User awareness plays a critical role in preventing ATO attacks.
- Conduct regular sessions on identifying phishing attempts, securing devices, and creating strong passwords.
- Simulate phishing campaigns to test user vigilance and improve awareness.
- Encourage enabling MFA on all accounts.
- Warn against sharing credentials over email or chat.
Adopt Real-Time Threat Intelligence
Leverage threat intelligence to proactively block known threats. Here’s how it helps:
- Stops attacks originating from malicious IP addresses or domains flagged in global intelligence databases.
- Provides insights into evolving attack tactics, enabling faster updates to security systems.
Enable Account Activity Alerts
Proactive notification systems can warn users about potential breaches.
Examples:
- Notify users of logins from unrecognized devices or locations.
- Send real-time alerts for suspicious activities like password resets or email changes.
Conduct Regular Security Audits
Ongoing assessments help identify vulnerabilities that attackers might exploit.
Types of Audits
- Penetration testing to simulate ATO attempts and evaluate the robustness of existing defenses.
- Vulnerability assessments to ensure systems are updated and configured securely.
Secure Customer Support Systems
Attackers often use social engineering to exploit support teams and gain access to accounts.
- Train support staff to authenticate users rigorously before making account changes.
- Limit access to sensitive data or account recovery tools to authorized personnel only.
Adopt Risk-Based Authentication
Risk-based authentication dynamically adjusts security requirements based on the perceived risk level of login attempts.
- Use factors like geolocation, device type, and login time to calculate a risk score.
- Prompt additional verifications for high-risk logins while streamlining low-risk ones to improve user experience.
How AppTrana WAAP Prevents Account Takeover (ATO) Attacks
AppTrana WAAP provides comprehensive protection against Account Takeover (ATO) attacks through a multi-layered defence strategy. It starts with rate-limiting to block brute force and credential stuffing attempts, followed by behavioral policy enforcement to detect anomalies based on user, IP, and geographic patterns.
Advanced bot mitigation identifies and neutralizes automated bots, distinguishing between malicious and legitimate ones, while client-side protection leverages Content Security Policies (CSPs) to prevent attacks like man-in-the-browser and script injections.
Vulnerabilities within applications are frequently exploited to carry out Account Takeover (ATO) attacks. AppTrana excels in proactively identifying and mitigating these vulnerabilities. It continuously scans applications to detect potential weaknesses that could be targeted by attackers. Additionally, AppTrana provides real-time virtual patching, effectively protecting vulnerabilities until permanent fixes can be implemented.
For complex attacks, its managed services team develops customized defences, making AppTrana a robust solution for safeguarding against all ATO attack vectors.


