What is Code Injection?
Code injection is a type of cyberattack where an attacker inserts malicious code into a vulnerable application, altering its execution. This can lead to data theft, unauthorized access, or system compromise. This attack targets websites, databases, and APIs, making it a major security risk.
How Code Injection Attacks Work
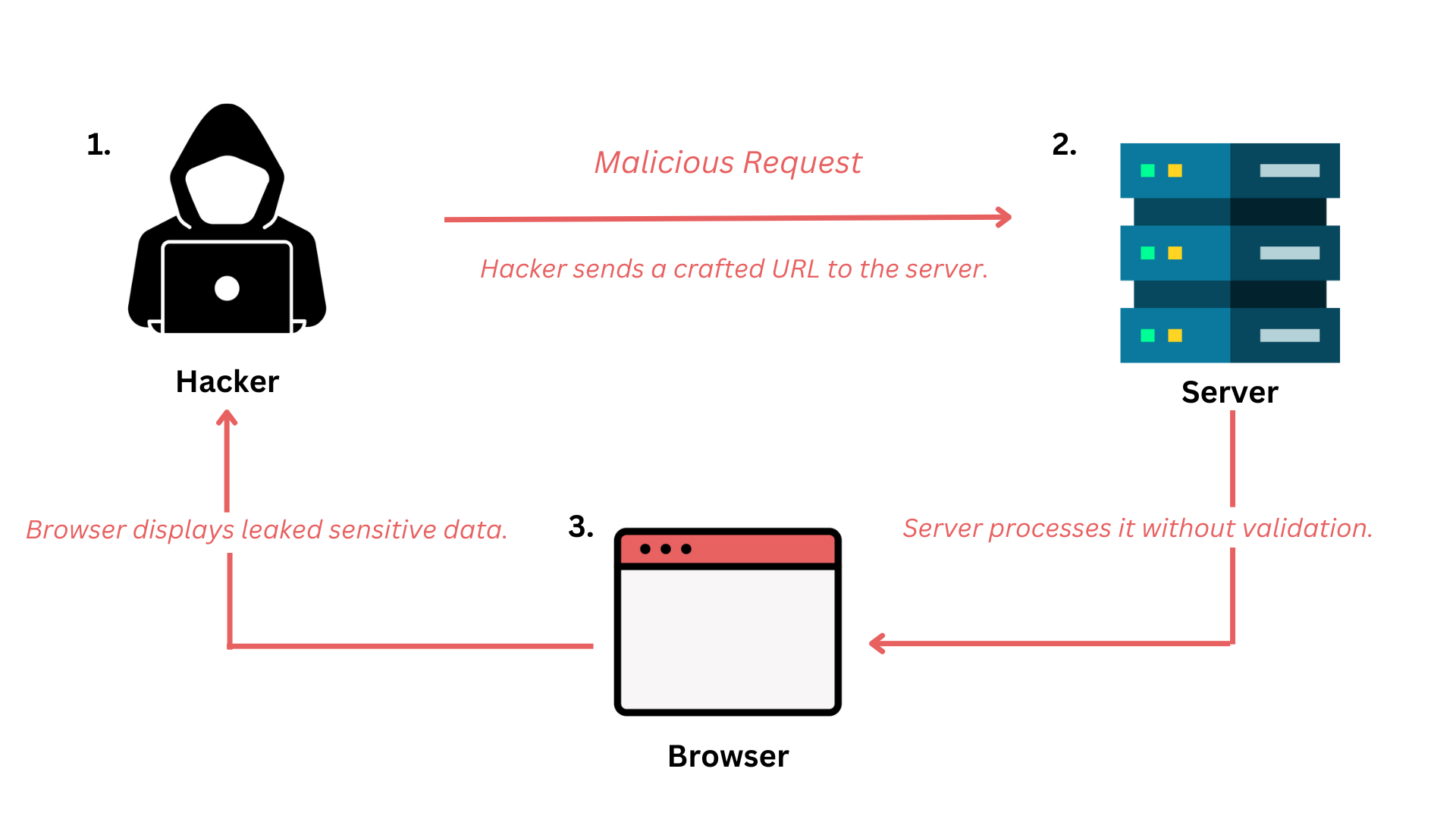
Attackers exploit vulnerabilities in how applications handle external inputs. By injecting malicious code, they can execute unauthorized commands, manipulate data, or gain unauthorized access to restricted areas.
Some of the most common types of code injection include:
SQL Injection (SQLi): Attackers insert harmful SQL queries into input fields to access, modify, or delete database information. This can expose sensitive data like usernames and passwords.
Cross-Site Scripting (XSS): Malicious scripts are injected into web pages, which then run in a user’s browser. This can steal login credentials, session cookies, or even redirect users to fake websites.
Command Injection: Hackers exploit system commands by injecting harmful input, allowing them to take control of a server, run unauthorized programs, or extract data.
LDAP Injection: Attackers manipulate directory service queries to bypass authentication, escalate privileges, or access restricted information in enterprise networks.
Code Injection Example
Imagine an online shopping website with a SQL database storing customer accounts. The website features a login form where users enter their email and password. The backend code handling the login might look like this:
$email = $_POST [ 'email' ] ;
$password = $_POST [ 'password' ] ;
$sql = "SELECT * FROM users WHERE email= ' $email ' AND password=' $password ' “;
$result = mysqli_query($conn, $sql);
if (mysqli_num_rows ($result) > 0) {
// User has successfully logged in
} else {
// Invalid email or password
}
In this code, the user input is directly inserted into the SQL query. If an attacker enters an email like this:
admin’ —
The SQL query becomes:
SELECT * FROM users WHERE email='admin' -- ' AND password=''
The double dash (– ) turns the rest of the query into a comment, causing the password check to be ignored. This lets the attacker log in as an administrator without knowing the actual password.
Attackers often experiment with different code injection techniques to extract sensitive information or gain unauthorized access. Without proper security measures, they can manipulate the database, steal user data, or even take full control of the system.
Real-World Examples of Code Injection Attack
1. Chrome Extensions Code Injection Attack
In December 2024, a major code injection attack targeted multiple Chrome browser extensions, compromising user authentication data, cookies, and active sessions. This supply chain attack primarily affected social media advertising and AI platforms, allowing attackers to hijack accounts and conduct unauthorized transactions. The attack began with phishing emails, tricking developers or users into installing malicious updates that injected harmful scripts into browser extensions. Once executed, these scripts could steal session tokens, impersonate users, and manipulate web interactions.
2. ViewState Code Injection Attack
ViewState Code Injection attack, discovered in December 2024, exploits misconfigurations in ASP.NET applications, where attackers inject malicious serialized objects into ViewState when MAC validation is disabled, leading to RCE.
This allows attackers to execute arbitrary commands, upload files, and establish persistence. Once compromised, they often deploy the Godzilla web shell, a post-exploitation framework with AES-encrypted communication, making it difficult to detect and remove.
3. Zyxel DSL CPE OS Command Injection Vulnerabilities (CVE-2024-40890 and CVE-2024-40891)
In 2024, multiple Zyxel DSL Customer Premises Equipment (CPE) devices were found to have post-authentication command injection vulnerabilities. Authenticated attackers could execute operating system commands via crafted HTTP requests or through Telnet. These vulnerabilities were significant enough to be listed in the CISA Known Exploited Vulnerabilities Catalogue.
4. XZ Utils Backdoor (CVE-2024-3094)
In early 2024, a malicious backdoor was introduced into the XZ Utils software package, specifically affecting versions 5.6.0 and 5.6.1. This backdoor allowed attacker to execute arbitrary code on affected Linux systems. The issue was promptly addressed upon discovery, but it highlighted the risks of code injection in widely used utilities.
5. Balada Injector Attacks on WordPress Sites
In October 2023, over 17,000 WordPress sites were compromised by Balada Injector campaigns. Attackers exploited known vulnerabilities in premium theme plugins to inject malicious code, leading to widespread infections.
6 Effective Techniques to Prevent Code Injection Attacks
1. Implement Input Validation and Sanitization
Restrict input to expected data formats and types only. Validating input prevents attackers from injecting malicious code, while sanitization removes harmful elements before processing. Input validation should be enforced on both client and server sides to minimize risks. Regularly updating validation rules helps address evolving attack patterns.
2. Use Parameterized Queries
Avoid dynamic queries and instead use parameterized statements or prepared statements to separate user inputs from SQL queries. This ensures that user inputs are treated strictly as data, eliminating SQL Injection risks. Many modern database management systems support this approach, making it a standard security practice. Developers should implement this as a default measure in all database interactions.
3. Restrict Privileges and Access Controls
Adopt the least privilege principle by limiting database and application permissions to the bare minimum required for operations. Restrict execution rights to sensitive commands and regularly review user access controls. This minimizes potential damage if an attack is successful. Frequent audits help detect misconfigurations that attackers could exploit.
4. Adopt the Least Privilege Principle
Restrict application and database permissions to the minimum necessary level, reducing the impact of a successful attack. Periodically audit user roles and remove unnecessary privileges to prevent attackers from exploiting excessive permissions. This practice is crucial for limiting the scope of potential security breaches.
5. Continuous Security Scanning and Penetration Testing
Regular security testing helps uncover vulnerabilities before attackers exploit them. Indusface WAS continuously scans web applications for injection vulnerabilities, including SQL injection, and command injection. It identifies security flaws in real-time and provides actionable insights to fix them. Manual Penetration Testing complements automated scanning by replicating real-world attack techniques that automated tools might miss. Security experts detect injection vulnerabilities, analyzing logic flaws, chained exploits, and misconfigurations while providing real-time insights for fixes.
6. Deploy Web Application Firewalls (WAF)
A Web Application Firewall (WAF) like AppTrana provides an essential layer of defence by blocking malicious inputs in real time. It detects and mitigates injection attacks by identifying suspicious patterns, such as unauthorized command execution attempts or unusual input behavior.
AppTrana comes with a built-in DAST scanner that detects vulnerabilities in real time, providing actionable insights for remediation. Additionally, its virtual patching feature ensures immediate protection—sealing security gaps before an official patch is deployed. This proactive approach prevents attackers from exploiting newly identified flaws, reducing the risk of breaches.
With continuous monitoring, adaptive security rules, and AI-driven threat detection, AppTrana dynamically evolves to counter emerging injection techniques, ensuring application integrity and data security.


 AppTrana WAAP Platform
AppTrana WAAP Platform

