What is DNS Cache Poisoning?
DNS cache poisoning is a type of attack where a malicious actor corrupts the DNS cache of a server or client, allowing the attacker to redirect traffic intended for legitimate websites to fraudulent or malicious websites. When a user attempts to access a website, the compromised DNS resolver provides a fake IP address, directing the user to a malicious server.
The attacker’s goal is typically to trick users into providing sensitive information (like login credentials or financial details), download malware, or enable other types of cyberattacks, such as man-in-the-middle attacks.
How DNS Cache Poisoning Works?
To understand DNS cache poisoning, let’s break down the basic process of DNS resolution and where vulnerabilities arise:
DNS Resolution Process
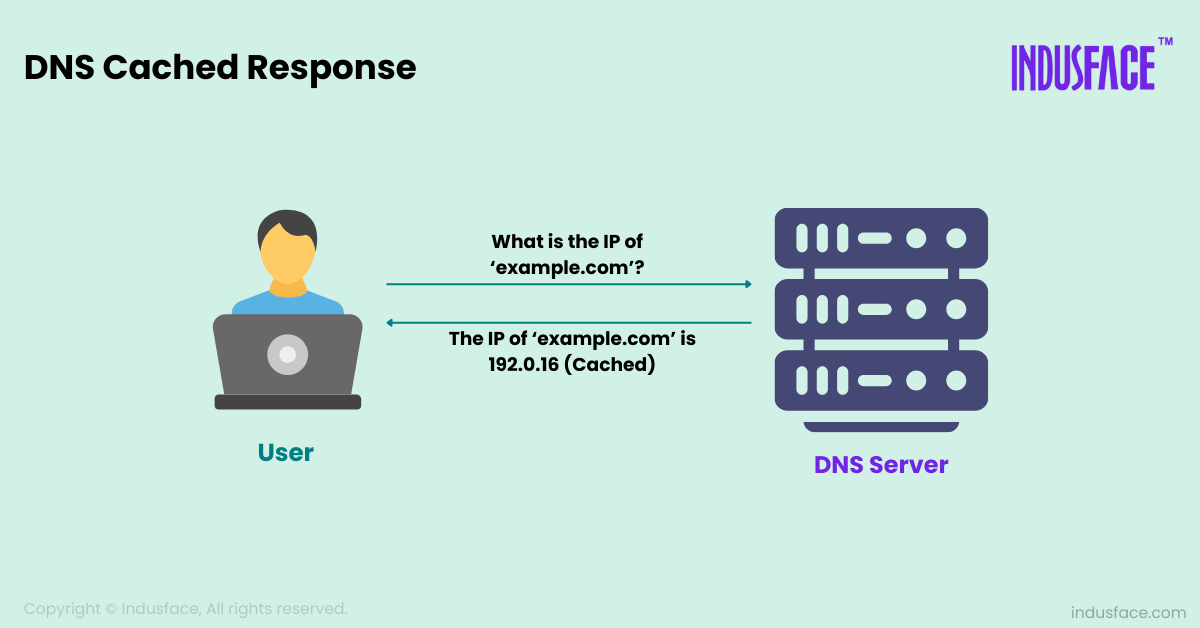
- Client Request: When you type a domain name into your browser, your device queries a DNS resolver (usually provided by your ISP).
- DNS Resolver Query: The DNS resolver checks its cache to see if it has a recent record of the IP address corresponding to the domain name. If it doesn’t, it queries other DNS servers.
- Response: The authoritative DNS server sends the correct IP address to the DNS resolver, which then caches the response and sends it back to your device. Your device now knows which IP address to connect to.
How the Attack Happens
During a DNS cache poisoning attack, a hacker intercepts the DNS queries and responds with fake information. Here’s how:
Injecting Malicious Data
The attacker injects the DNS resolver with forged DNS responses containing the IP address of a malicious server instead of the legitimate one. If the forged response reaches the resolver before the legitimate one, the resolver will cache the malicious data.
Catching the Cache
Once the poisoned entry is cached, any user querying that domain name will be redirected to the malicious IP address until the cache expires or is manually flushed.
Impacts of DNS Cache Poisoning
The consequences of a successful DNS cache poisoning attack can be severe. Here are some of the most significant impacts on DNS security:
- Phishing and Data Theft: Attackers can redirect users to fake websites that look identical to legitimate sites. Unsuspecting users may enter sensitive information like usernames, passwords, or credit card details, which the attacker can steal.
- Spread of Malware: Users might be directed to sites that automatically download malware or spyware to their devices.
- Widespread Misinformation: If an attacker poisons a widely-used DNS resolver, it can result in large numbers of users being misdirected, spreading disinformation, or causing service disruptions.
- Man-in-the-Middle Attacks: The attacker can intercept and manipulate communications between the user and the intended website, furthering the scope of the attack.
DNS Cache Poisoning vs. DNS Spoofing: Are They the Same?
Although the terms DNS cache poisoning and DNS spoofing are often used interchangeably, they have slightly different meanings. DNS cache poisoning refers to a specific attack method where false DNS information is injected into a resolver’s cache. As long as the poisoned cache remains active, users who query that resolver will be directed to fraudulent websites.
On the other hand, DNS spoofing is a broader term encompassing any attack that delivers incorrect DNS responses to mislead users or systems. DNS spoofing can occur with or without modifying a resolver’s cache and may involve providing fake DNS responses directly to a user or system.
In essence, DNS cache poisoning is one type of DNS spoofing attack, but not all DNS spoofing involves poisoning the DNS cache. Despite these nuances, both attacks share the same goal: misdirecting users to malicious websites by tampering with DNS response.
DNS Cache Poisoning vs. DNS Hijacking: Understanding the Differences
While both DNS cache poisoning and DNS hijacking are attacks on the Domain Name System (DNS), they differ in their methods and impacts. The main objective of DNS cache poisoning is often phishing, malware distribution, or man-in-the-middle attacks, where unsuspecting users are lured into interacting with harmful sites.
In contrast, DNS hijacking is a more invasive attack that involves taking over a DNS server or changing the DNS settings of devices, typically by hacking a DNS server or altering DNS configurations on a network or router. Once DNS hijacking occurs, users are redirected to malicious sites at a broader scale, affecting entire networks or organizations. Unlike DNS cache poisoning, which targets the cached records of a resolver, DNS hijacking compromises the actual DNS settings, allowing attackers to control which websites users can access.
Protecting Against DNS Cache Poisoning
While DNS cache poisoning can be highly damaging, there are several steps organizations and users can take to mitigate the risk. Here’s how to protect against DNS poisoning attacks:
1. Implement DNSSEC
DNSSEC is a suite of security protocols that applies cryptographic validations to DNS records. These signatures ensure the authenticity and integrity of the data, preventing attacks like cache poisoning and spoofing. By verifying the legitimacy of DNS responses, DNSSEC protects users from malicious redirection and enhances overall internet security.
Organizations can leverage AppTrana WAAP’s specialized DNSSEC features to safeguard against DNS attacks. These services offer real-time traffic analysis, filtering, and targeted mitigation to effectively counter DNS-based DDoS attacks.
2. Use Secure DNS Resolvers
Encourage the use of trusted DNS resolvers that are equipped with security features. Services like AWS Route 53 employ enhanced security practices to reduce the risk of DNS cache poisoning.
3. Regularly Flush DNS Cache
Organizations should regularly flush DNS caches to minimize the risk of poisoned entries being used. DNS caches are temporary storage systems, and clearing them frequently ensures that the resolver is always fetching up-to-date and legitimate data.
4. Randomize Source Ports and Transaction IDs
Attackers rely on predicting transaction IDs and source ports to carry out DNS spoofing. By randomizing these elements in DNS queries, organizations make it much harder for attackers to successfully inject forged DNS responses.
5. Keep Software and Systems Updated
Ensure that DNS servers and any network infrastructure handling DNS queries are always up-to-date with the latest security patches. Vendors regularly release updates that address vulnerabilities exploited in DNS cache poisoning attacks.
6. Implement DNS Firewall
DNS Firewall filters and monitors DNS queries, blocking suspicious or unauthorized requests that attempt to exploit vulnerabilities in the DNS infrastructure. By intercepting potentially harmful traffic, a DNS firewall ensures that only legitimate DNS queries and responses are processed.
7. Use DNS over HTTPS (DoH)
DoH encrypts DNS queries, making it more difficult for attackers to intercept or modify DNS traffic. This added layer of encryption helps protect against attacks that rely on eavesdropping or manipulating DNS responses.


