What is DNS Exfiltration?
DNS exfiltration is a method of data theft where attackers use DNS queries to send sensitive information from a compromised system to an external server they control. DNS, by design, is intended to be a fast, reliable service that most security tools allow through firewalls.
Attackers exploit this openness by embedding small chunks of stolen data within DNS queries. These queries reach an external DNS server controlled by the attacker, where the exfiltrated data can be reconstructed.
How DNS Exfiltration Works
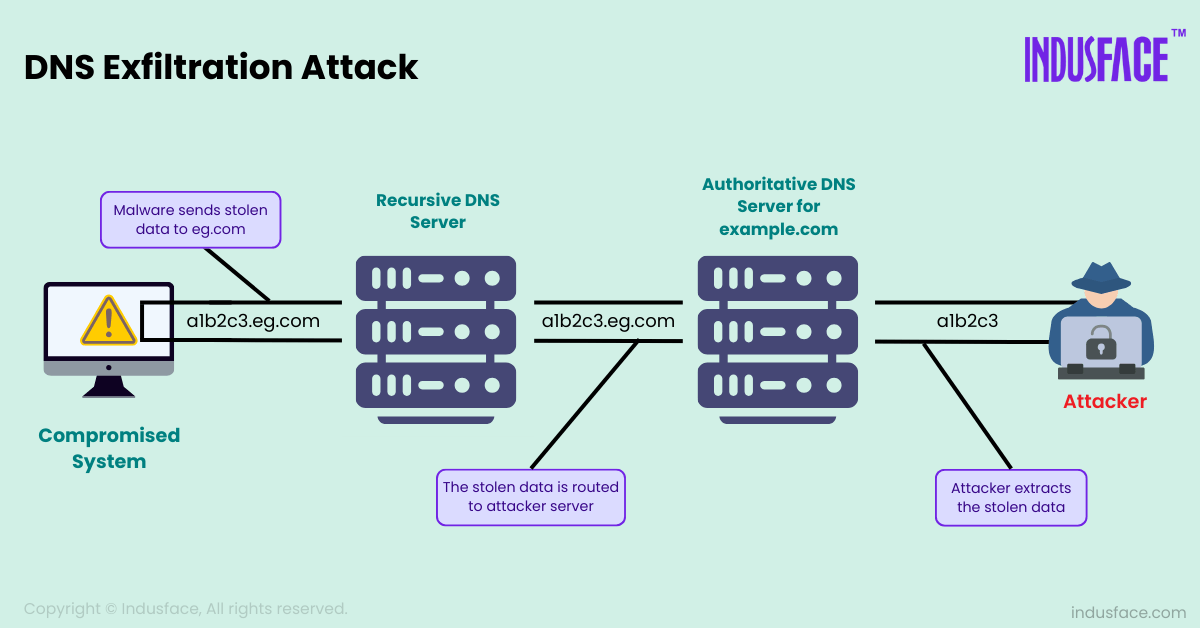
Compromising a System: First, an attacker gains access to a network, typically through phishing attacks, malware, or by exploiting vulnerabilities. Once inside, they collect sensitive information like login credentials, proprietary data, or personal information.
Encoding Data into DNS Queries: The attacker breaks down the stolen data into small chunks that can fit within the character limit of a DNS query. These chunks are then encoded into the subdomain field of a DNS request. For example, an exfiltration query might look like:
a1b2c3.example.com
Here, the string a1b2c3 is a small piece of the stolen data, and example.com is the attacker’s domain.
Sending DNS Queries: These encoded DNS queries are sent from the compromised machine to a DNS resolver. Since DNS traffic is usually allowed through firewalls, the queries are typically not blocked or scrutinized by standard security tools.
Receiving the Data: The resolver forwards the request to the authoritative DNS server, which belongs to the attacker. The attacker’s server collects the exfiltrated data from each query and then reconstructs it.
Reconstructing Data: Over time, the attacker can extract large amounts of sensitive information, piece by piece, from the compromised system without triggering traditional security alerts.
What is Low-Throughput Data Exfiltration?
Low-throughput data exfiltration refers to the slow and steady extraction of sensitive information from a compromised system over an extended period, often in small amounts at a time. This method allows attackers to evade detection by operating under the radar of traditional security systems, which are more likely to flag large and rapid data transfers.
Key Characteristics of Low-Throughput Data Exfiltration
- Small Data Packets: Data is broken down into tiny fragments and transmitted discreetly over time, often mixed with normal network traffic.
- Extended Time Period: Exfiltration occurs over days, weeks, or even months to avoid triggering alerts based on abnormal network behavior.
- Stealth and Evasion: By maintaining a low data transfer rate, attackers aim to bypass detection tools that monitor for large spikes in data traffic.
- Utilization of Common Channels: Attackers typically use trusted communication channels like DNS queries or HTTP requests, which are rarely scrutinized as thoroughly as other forms of data transfer.
The Risks of DNS Exfiltration
DNS exfiltration can have severe consequences for organizations, including:
- Data Breach: Attackers can steal sensitive information, including intellectual property, financial data, customer records, or authentication credentials.
- Financial Loss: Beyond the immediate breach, the loss of data may lead to legal fees, regulatory fines, and the cost of repairing damage to brand reputation.
- Advanced Persistent Threat (APT): DNS exfiltration is often used by nation-state actors and sophisticated cybercriminal groups. This technique is a hallmark of APT attacks, which are often long-term and go unnoticed for extended periods, allowing attackers to continually siphon off data.
Out-of-Band SQL Injection Using DNS
Attackers may also exploit out-of-band (OOB) SQL injection to steal data via DNS. In this technique, SQL queries are crafted to interact with DNS, allowing attackers to extract information from a database without a direct response. The compromised application unknowingly initiates DNS queries containing sensitive data, which the attacker collects from their controlled DNS server.
By employing OOB techniques, attackers bypass traditional defences, making it critical to monitor both DNS traffic and potential SQL injection vectors. Implementing web application firewalls (WAFs) and database security measures helps reduce the risk of such attacks.
Check out the effective ways to prevent SQL Injection attacks in detail.
How to Detect DNS Exfiltration?
Detecting DNS exfiltration can be challenging because DNS traffic is typically considered trustworthy and rarely inspected as thoroughly as other forms of communication.
However, here are some signs that can indicate an ongoing DNS exfiltration attempt:
- Unusual DNS Traffic Patterns: Monitoring DNS traffic for unusual patterns, such as an unusually high volume of DNS requests to specific domains, can indicate exfiltration attempts. Pay particular attention to large numbers of DNS queries with uncommon domain names or those containing long, unusual subdomain strings.
- Anomalous Query Lengths: DNS exfiltration queries often contain encoded data, which can result in unusually long domain names or subdomains. Look for queries that exceed typical length limits.
- Frequent Requests to Unrecognized Domains: Attackers often register obscure or misspelled domains for exfiltration. DNS requests to unknown or newly registered domains should raise red flags.
- Out-of-Hours Activity: Unusual DNS activity outside of normal business hours, especially from devices that are typically inactive, may indicate that data is being exfiltrated during off-hours to avoid detection.
- Unusual Query Volume: If a single device or small group of devices is generating significantly more DNS queries than expected, this could be a sign of data being exfiltrated in small, encoded packets.
How to Prevent DNS Exfiltration?
Implement DNS Security Solutions: Use DNS security tools that provide deeper inspection of DNS queries, block malicious domains, and identify suspicious DNS traffic.
Leverage AppTrana’s DNSSEC capabilities to block DNS-based attacks.With AppTrana’s DNS management, you can manage DNS records effortlessly, providing robust security for your DNS environment and allowing you to focus on your core business activities.
Encrypt DNS Traffic with DNS-over-HTTPS (DoH) or DNS-over-TLS (DoT): Encrypting DNS traffic helps ensure that malicious actors cannot intercept or manipulate DNS queries. While encryption alone won’t stop exfiltration, it adds a layer of security to the DNS process. Check out DoH and DoT in detail.
Monitor DNS Traffic Regularly: Continuously monitor DNS traffic for unusual behavior, focusing on query volume, unusual domain patterns, and query length. Monitoring tools can flag anomalous patterns and help identify potential exfiltration activities.
Implement DNS Logging: Enable logging of all DNS requests so that anomalies can be traced back to their origin. Detailed DNS logs can provide a forensic trail to identify the source of an exfiltration attempt.
Block Unnecessary DNS Requests: Use firewalls and network controls to block DNS requests to known malicious domains and unapproved external DNS servers. Ensure that all DNS queries go through authorized DNS servers to limit the risk of rogue queries being sent to an attacker’s server.
Use Data Loss Prevention (DLP) Solutions: Implement DLP tools that monitor for sensitive data leaving the network, even when hidden within DNS queries. DLP solutions can detect and block suspicious activity that involves critical or confidential data.



