What is DNS Filtering?
DNS filtering is the process of blocking or allowing DNS queries based on predefined rules. When a user attempts to visit a website, their device sends a DNS query to resolve the domain name (e.g., example.com) to an IP address. With DNS filtering, organizations can inspect these requests and enforce policies to allow, block, or redirect them based on specific criteria.
At its core, DNS filtering enables organizations to:
- Block access to known malicious or high-risk domains, preventing malware infections and phishing attacks.
- Restrict access to inappropriate or non-work-related content, improving productivity and enforcing usage policies.
- Prevent data exfiltration by stopping DNS requests that attempt to send data outside the organization.
How DNS Filtering Works
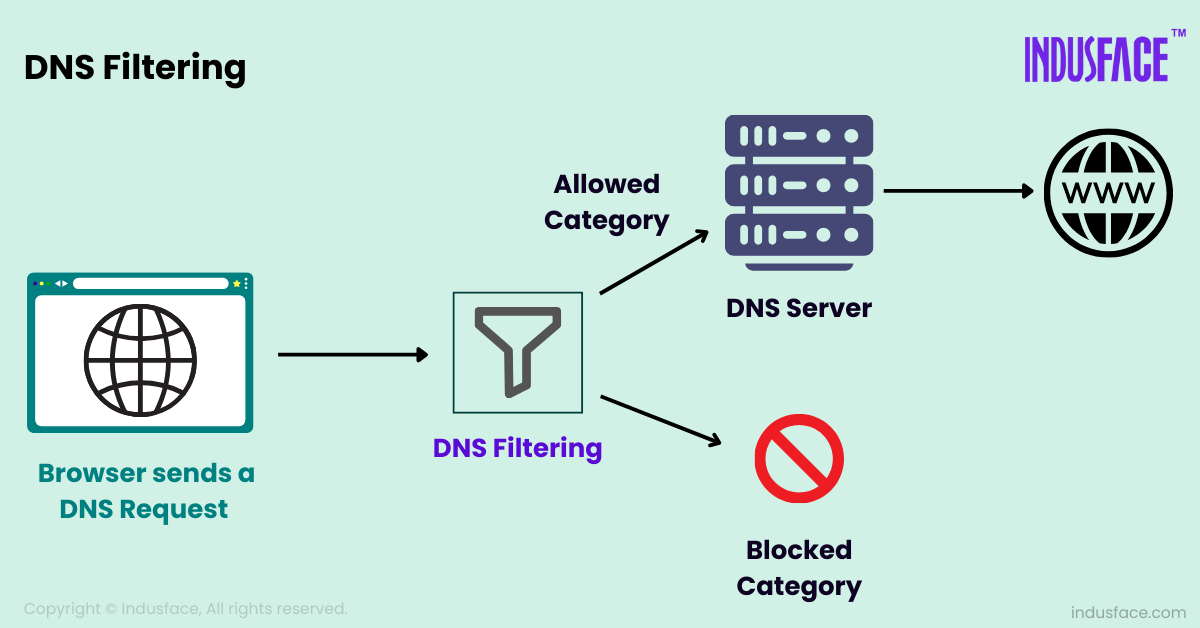
DNS filtering typically involves the following components:
- DNS Filter: This is the system that enforces filtering rules. It can be an on-premises appliance, a software-based solution, or a cloud service that filters DNS requests based on a set of policies.
- Policy Configuration: Administrators define policies to block or allow specific categories of websites (e.g., “Malware,” “Social Media,” “Adult Content”) or specific domains based on threat intelligence.
- Enforcement: When a DNS request is made, the DNS filter checks if the requested domain matches any policy rules. If the domain is blocked, the request is denied or redirected to a warning page.
By intercepting and evaluating DNS queries before they reach their destination, DNS filtering acts as a security layer that can prevent malicious activity and enforce browsing policies.
Key Benefits of DNS Filtering
DNS filtering offers several benefits, making it an essential component of a layered security strategy:
- Malware and Phishing Protection: DNS filtering can block access to known malicious domains associated with phishing, ransomware, or command-and-control (C2) servers. This reduces the risk of users accidentally accessing harmful websites.
- Data Exfiltration Prevention: Many attackers use DNS tunneling to exfiltrate data from networks. DNS filtering can detect and block suspicious DNS activity, limiting an attacker’s ability to send data outside the organization.
- Content Control: DNS filtering allows organizations to block access to certain types of content, like social media, adult sites, and streaming services, enhancing productivity and ensuring policy compliance.
- Low Maintenance and Lightweight: Since DNS filtering doesn’t involve inspecting the full content of network traffic, it’s less resource-intensive than other solutions like deep packet inspection, making it suitable even for smaller networks.
- Visibility and Control: DNS filtering provides IT administrators with visibility into users’ browsing habits and insight into potential threats targeting the network, allowing for proactive security measures.
- Compliance Enforcement: DNS filtering can be used to restrict access to specific categories of websites, helping organizations enforce internet usage policies and comply with regulatory requirements.
- Supporting Remote Work Security: With the rise of remote work, DNS filtering helps secure remote users by filtering DNS requests from off-network locations. This is particularly effective when combined with VPNs or Secure Access Service Edge (SASE) architectures.
- Improving Network Performance: DNS filtering can reduce bandwidth usage by blocking unwanted domains and preventing access to high-bandwidth sites like video streaming services during work hours.
Best Practices for Implementing DNS Filtering
Implementing DNS filtering effectively requires thoughtful planning and configuration to meet an organization’s security needs. Here are some best practices:
- Define Clear Policies Based on Needs: Before implementing DNS filtering, define policies that align with your organization’s security and compliance requirements. For instance, categorize which types of content to block, set restrictions for specific user groups, and determine acceptable usage policies.
- Use Threat Intelligence Feeds: Choose a DNS filtering solution that integrates real-time threat intelligence to block newly identified malicious domains. Regular updates ensure that your DNS filter remains effective against emerging threats.
- Monitor and Analyze DNS Logs: Regularly review DNS logs to identify potential anomalies, such as repeated requests to untrusted domains or unusual traffic patterns. Many DNS filtering solutions provide analytics and reporting features that can help identify early signs of compromise.
- Enable DNSSEC: DNS Security Extensions (DNSSEC) add an extra layer of authentication, helping to prevent DNS spoofing attacks. DNSSEC works well alongside DNS filtering by ensuring that DNS responses come from legitimate sources.
- Configure Alerts for Suspicious Activity: Set up alerts for high-risk DNS events, such as attempts to access blocked sites or requests to domains with unusually long or encoded subdomains (a possible indicator of DNS tunneling).
- Test and Fine-Tune Policies: Test your DNS filtering rules to avoid over-blocking, which can hinder productivity. Start with a basic set of rules, monitor the results, and adjust as needed to strike a balance between security and user experience.


