What is DNS Hijacking?
DNS hijacking is a cyberattack where an attacker redirects or alters DNS queries to lead users to fraudulent websites instead of the intended destinations. This can happen through various methods, including compromising DNS servers to alter records, exploiting weak router security to change DNS settings, or using malware to modify device DNS configurations.
The risk of DNS hijacking attack is significant because it can target individual users, entire organizations, or even vast segments of the internet. Once hijacked, the user may unknowingly divulge sensitive information, such as login credentials, social security numbers, credit card details, or other personal data to the attacker.
How Does a DNS Hijacking Attack Work?
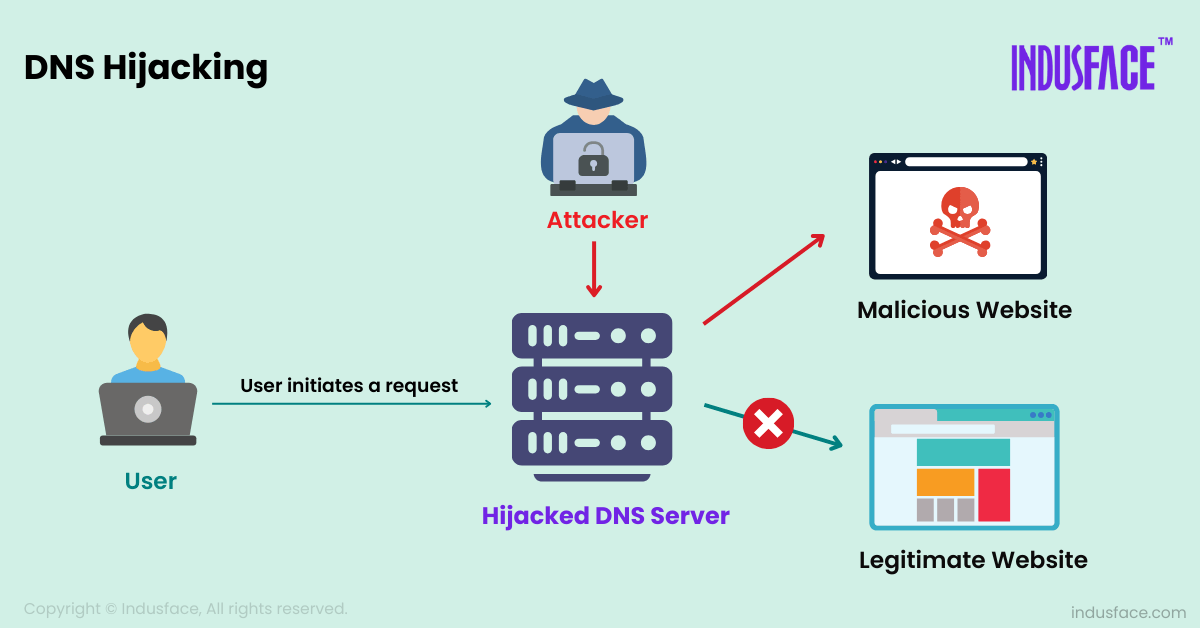
To understand how DNS hijacking works, it’s essential to grasp the DNS resolution process. When you type a URL into your browser, your device sends a DNS query to a DNS server, asking it to resolve the domain name to its corresponding IP address. This IP address allows your device to find the server hosting the website and establish a connection.
In a DNS hijacking attack, the attacker intercepts this process. They can either:
- Compromise the DNS server itself by gaining control of its settings.
- Infect the victim’s device with malware that changes the local DNS settings, forcing queries to malicious servers.
- Intercept the DNS request during its transmission, redirecting it to a malicious server.
Once in control of the DNS resolution process, the attacker can redirect users to malicious websites without altering the visible URL, making it difficult for users to detect the attack.
Types of DNS Hijacking
DNS hijacking can take several forms, each with its own method of exploitation. The following are the common types of DNS hijacking attacks:
Local DNS Hijacking
Attackers install malware on a user’s device to change local DNS settings, to manipulate its DNS settings, redirecting traffic from legitimate websites to fraudulent ones. This often occurs when users unknowingly download malicious software through phishing emails or untrustworthy sites.
Example: A user unknowingly installs malware by downloading software from an untrusted source. Once installed, the malware alters the DNS configuration on the affected device. This can involve changing the DNS server addresses to those controlled by the attacker or redirecting DNS queries to malicious IP addresses.
Router DNS Hijacking
Router DNS hijacking attack targets home or corporate routers. Attackers often exploit security weaknesses in routers, such as outdated firmware or default passwords to change DNS settings. By changing these configurations, they can reroute all devices connected to that router, making every user susceptible to phishing pages or malware-laden websites.
Example: If the attacker successfully hijacks a home router, every device on the home network, from computers to smart TVs, can be redirected to malicious sites.
Man-in-the-Middle DNS Hijacking
Attackers intercept communication between the user and the DNS server, injecting false DNS responses. This allows them to redirect users to malicious sites without their knowledge, often occurring on unsecured networks or through compromised connections. Learn more about man-in-the-middle attack.
Example: This often occurs in public Wi-Fi networks, where attackers can capture unsecured DNS requests and redirect users to phishing websites.
DNS Server Hijacking
This attack involves gaining unauthorized control over DNS servers. Once compromised, attackers can alter DNS records, causing all requests for specific domains to be redirected to malicious websites. This affects all users relying on the hacked DNS server, making it a widespread threat.
Example: An attacker gains access to a DNS provider’s servers and redirects traffic from a bank’s legitimate website to a phishing site that looks identical.
ISP DNS Hijacking
In ISP DNS hijacking, Internet Service Providers modify DNS settings intentionally or accidentally. Some ISPs redirect users to ad-filled pages when they mistype URLs. However, if an attacker compromises an ISP’s DNS infrastructure, they can reroute a significant number of users to fraudulent sites, impacting a large audience.
Famous DNS Hijacking Attacks
DNS hijacking has been employed in several high-profile attacks:
- The DNSChanger Malware (2011): The DNSChanger Trojan, developed by the Estonian cybercriminal organization Rove Digital, hijacks DNS settings on infected computers. By doing so, the malware redirects users to fraudulent websites. Worldwide, it compromised over 4 million computers in more than 100 countries. In the U.S., approximately 500,000 devices were infected, including systems used by individuals, businesses, and government agencies like NASA.
- Google.com.vn Hijack (2015):Google’s Vietnam domain (google.com.vn) was hijacked by hackers allegedly linked to the infamous Lizard Squad group. Visitors to the site were shown an image of a man taking a selfie, accompanied by a message stating that Lizard Squad had hacked the website. However, Google Vietnam itself was not compromised. Using DNS hijacking, the attackers altered Google’s nameservers to send users to a defacement page.
- MyEtherWallet Attack (2018): In this incident, attackers hijacked the DNS of the popular cryptocurrency wallet service, MyEtherWallet, directing users to a phishing website. The attackers stole over $150,000 worth of Ethereum from users who entered their credentials on the fake site.
Impact of DNS Hijacking
The impact of DNS hijacking can be severe, affecting both individuals and businesses alike:
- Data Theft: Users may unknowingly enter sensitive information on a fraudulent site controlled by the attacker.
- Financial Loss: In cases like MyEtherWallet, users lost cryptocurrency due to being redirected to phishing sites.
- Reputation Damage: Organizations that experience DNS hijacking, especially if the attack compromises customer data, may suffer long-term reputational damage.
- Malware Distribution: Users redirected to malicious websites may unknowingly download malware onto their devices.
How to Protect from DNS Hijacking Attacks?
Use Secure DNS Services
A simple yet highly effective way to defend against DNS hijacking is to use a trusted DNS service provider that provides security-enhanced DNS resolutions. Public DNS providers like AWS Route 53 are equipped with advanced security features, including threat detection, encrypted DNS queries, and DNS filtering to block malicious domains.
Configure Routers Securely
Routers are a common target for DNS hijacking, especially in home networks. Attackers frequently take advantage of poorly configured routers or default credentials to alter DNS settings. Securing your router is an important step in preventing DNS hijacking.
Steps to Secure Your Router
- Change Default Passwords: Many routers come with default credentials that are easily guessed or found online. Change both the admin username and password to something strong and unique.
- Update Firmware Regularly: Vendors release firmware updates to fix vulnerabilities. Regularly check for updates and apply them to ensure your router is protected from known exploits.
- Disable Remote Access: If remote administration is not necessary, disable it to prevent attackers from gaining access to your router over the internet.
- Use WPA3 or WPA2 Encryption: Secure your Wi-Fi network with strong encryption like WPA3 / WPA. This ensures unauthorized users can’t access your network and tamper with your router’s DNS settings.
- Lock Down DNS Settings: Some routers allow you to configure your DNS settings manually. Set them to use a trusted DNS provider like Google and lock the settings to prevent unauthorized changes.
Enable DNS Over HTTPS (DoH) / DNS Over TLS (DoT)
DNS Over HTTPS (DoH) and DNS Over TLS (DoT) are two modern security protocols that encrypt DNS queries, preventing attackers from intercepting or altering DNS requests. By encrypting the DNS traffic, these protocols ensure that no one—whether hackers or internet service providers (ISPs)—can see or tamper with the websites you’re trying to visit.
Install Anti-Malware and Anti-Virus Software
Malware frequently manipulates DNS configurations on compromised devices, resulting in DNS hijacking. Installing reliable anti-malware and anti-virus software helps protect your devices from such threats by detecting and blocking malicious attempts to change DNS configurations.
- Real-Time Scanning: Ensure your security software includes real-time scanning, which continuously monitors your device for suspicious activity, including attempts to alter DNS settings.
- Scheduled Scans: Run regular scans to detect and remove any malware that could potentially lead to DNS attack.
Use a Virtual Private Network (VPN)
A Virtual Private Network (VPN) secures your internet traffic, including DNS queries, by encrypting it and routing it through a protected server. This adds an extra layer of protection, especially when using public Wi-Fi networks, which are vulnerable to man-in-the-middle attacks and DNS hijacking.
VPNs are particularly useful when connecting to public Wi-Fi, where DNS hijacking and other forms of attacks are more prevalent.
Regular DNS Auditing and Monitoring
Organizations should conduct regular DNS audits to ensure that DNS records and settings have not been altered by unauthorized actors. Monitoring DNS traffic for unusual activity can aid in detecting DNS hijacking attempts at an early stage.
- DNS Traffic Monitoring: Use tools to monitor DNS queries and responses. A sudden increase in traffic to unknown IP addresses may signal a DNS hijacking attack.
- Regular DNS Record Checks: Periodically verify your DNS records and nameserver configurations to ensure they haven’t been tampered with.
Implement DNS Firewall
If a DNS query is directed to a known malicious or suspicious domain, the DNS firewall blocks the request before it reaches the attacker-controlled DNS server. This prevents users from being redirected to fake websites that could lead to phishing attacks or malware downloads.
DNS firewalls are equipped with real-time threat intelligence databases that contain lists of known malicious domains, IP addresses, and URLs. When a user attempts to visit a website, the DNS firewall cross-references the request with this database and blocks access to harmful sites.
Enable DNSSEC (Domain Name System Security Extensions)
DNSSEC is a security protocol designed to protect the DNS resolution process by ensuring that responses to DNS queries are authenticated and haven’t been tampered with. Adding cryptographic validation to DNS records blocks attackers from tampering with or faking DNS responses.
While DNSSEC is not widely enabled by default, organizations and website owners can enable it to secure their domain’s DNS records. Here’s why DNSSEC is crucial:
- Authenticated Responses: DNSSEC ensures that the DNS query response comes from a legitimate source, protecting against man-in-the-middle and DNS hijacking attacks.
- Data Integrity: It prevents attackers from altering DNS records by verifying the data’s integrity before delivering it to users.
To implement DNSSEC, you need to work with your domain registrar and DNS hosting provider to ensure your DNS zone is signed and verified.
While DNSSEC is a proven defense against DNS hijacking, many organizations have yet to implement it. Organizations often lack the expertise needed for proper implementation. Effective DNSSEC deployment depends on efficient DNS management.
AppTrana WAAP simplifies the DNSSEC implementation process, making it user-friendly and significantly lowering associated risks. The managed service team assist in DNS management to streamline the process and enhance your overall security.


 AppTrana WAAP Platform
AppTrana WAAP Platform

