DNS reflection and amplification attacks are among the most powerful and disruptive types of Distributed Denial of Service (DDoS) attacks. These attacks exploit vulnerabilities in the Domain Name System (DNS), using it to amplify traffic and overwhelm a target, often leading to significant outages and disruptions for websites, applications, and online services.
What is DNS Reflection Attack?
In a DNS reflection attack, the attacker sends DNS queries to publicly accessible DNS servers, but with a key twist: they spoof the source IP address so that it appears the query is coming from the target’s IP address. This way, when the DNS server sends its response, it delivers it to the victim instead of the attacker.
The DNS server acts as an unwitting accomplice, reflecting traffic onto the target.
What is DNS Amplification Attack?
DNS amplification attacks take DNS reflection a step further. In addition to spoofing the source IP, attackers send small DNS queries that request large responses. The attacker takes advantage of the DNS protocol’s design, where small requests can lead to much larger responses. As a result, the attack amplifies the amount of traffic sent to the victim, sometimes by factors of 30 to 50 times or more.
The combination of reflection and amplification allows attackers to generate vast amounts of traffic while using minimal resources on their end.
How Does a DNS Reflection Attack Work?
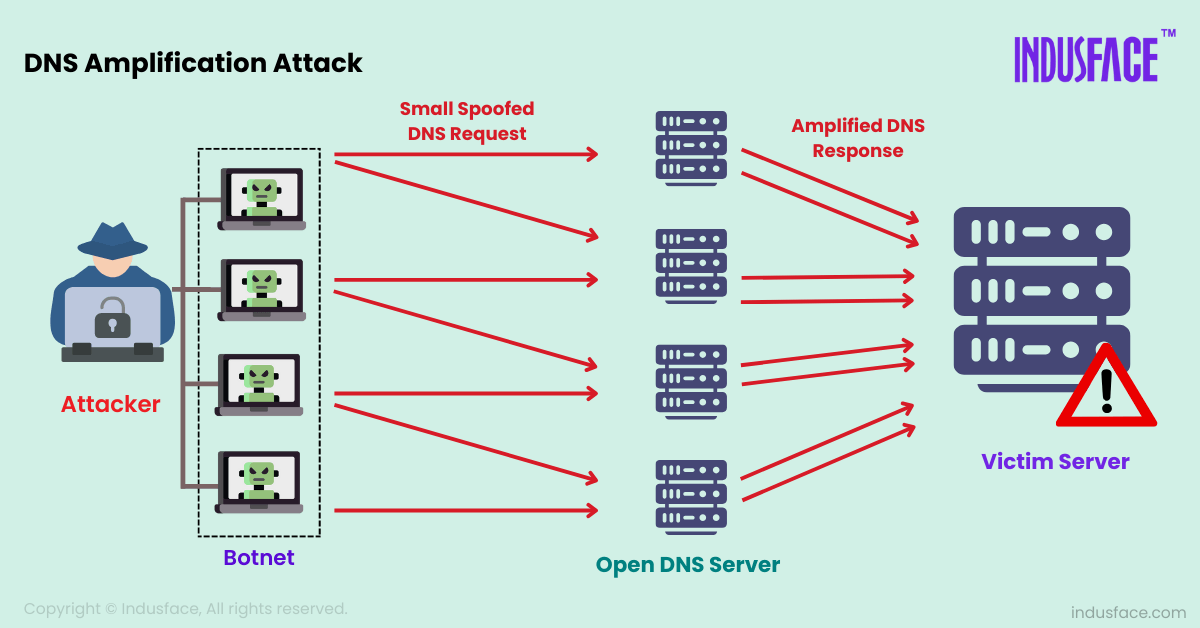
Here is a step-by-step breakdown of how DNS reflection attacks work:
- The Attacker Spoofs the Target’s IP: The attacker crafts a DNS query but spoofs the source IP address, making it appear as though the query came from the victim’s IP address.
- The Attacker Sends Queries to DNS Servers: The attacker sends multiple DNS queries using botnets to open DNS resolvers or authoritative DNS servers. These queries request large responses, often querying for the “ANY” record type, which returns all available DNS records for a domain.
- DNS Servers Respond to the Spoofed IP: The DNS servers send their responses back to the IP address listed in the query—the victim’s IP address, not the attacker’s. Since the responses are much larger than the original queries, the victim is bombarded with massive amounts of data.
- Amplification Overwhelms the Target: Due to the amplification effect of the DNS responses, the target is overwhelmed with excessive traffic, consuming its bandwidth and resources, potentially causing the server or network to crash or become inaccessible to legitimate users.
Why Are DNS Reflection Attacks Effective?
DNS reflection attacks are particularly effective due to several factors:
- Amplification: DNS responses are often much larger than the initial DNS queries. In some cases, the amplification factor can be 30 to 50 times the size of the query, multiplying the attack’s impact on the victim’s bandwidth and network resources.
- Exploiting Open DNS Resolvers: Many DNS servers are publicly accessible, which attackers can exploit to carry out their reflection attacks. These open DNS resolvers allow anyone to send DNS queries and receive responses, providing attackers with numerous amplification points.
- Anonymity: Since the attack traffic is reflected through legitimate DNS servers, it becomes difficult to trace the attacker’s true origin. The victim only sees the IP addresses of the DNS servers, not the attacker.
- Low-Cost, High-Impact: DNS reflection attacks require minimal resources from the attacker but can have devastating effects on the target. By using DNS amplification, an attacker can cause significant disruption with only a small amount of bandwidth.
High-Profile DNS Reflection and Amplification Attacks
Over the years, DNS reflection attacks have been used in many high-profile DDoS attacks. Some notable examples include:
- GitHub Attack (2018): GitHub, one of the world’s largest code repositories, was targeted by a massive DDoS attack that reached 1.35 Tbps. While the attack primarily used a Memcached amplification technique, DNS reflection played a role in the distributed nature of the attack.
- Spamhaus Attack (2013): One of the largest reported DDoS attacks at the time, the Spamhaus attack peaked at 300 Gbps. Attackers used DNS reflection and amplification techniques, overwhelming Spamhaus’s servers and causing widespread internet slowdowns across Europe.
- Dyn Attack (2016): The DDoS attack on Dyn, a major DNS provider, affected many popular websites, including Twitter, Netflix, and Reddit. While the attack primarily used IoT devices to generate traffic, DNS reflection attacks are often part of larger DDoS campaigns, highlighting the vulnerability of DNS infrastructure.
How to Prevent DNS Reflection Attacks?
Preventing and mitigating DNS reflection attacks requires a multi-layered approach that targets both DNS administrators and network security teams. Here are some strategies for defending against these attacks:
Disable Open DNS Resolvers
An effective method to prevent DNS reflection attacks is by closing open DNS resolvers. Public DNS resolvers should be configured to accept queries only from trusted IP addresses and reject queries from external sources. By disabling open resolvers, DNS servers are less likely to be exploited in a reflection attack.
Source IP Validation (Spoofing Prevention)
Attackers rely on spoofing the victim’s IP address to redirect DNS responses in a reflection attack. By enabling source IP validation through techniques like ingress filtering (BCP 38), network administrators can ensure that DNS queries with spoofed IP addresses are blocked before reaching DNS servers.
DNSSEC and Response Rate Limiting (RRL)
Domain Name System Security Extensions (DNSSEC) provides authentication for DNS responses, reducing the risk of DNS amplification attacks. Additionally, implementing DNS response rate limiting (RRL) can help prevent servers from generating a large number of responses to a single IP address, reducing the risk of abuse.
With specialized DNSSEC feature, AppTrana WAAP ensures that your applications are continually protected from DNS attacks. By authenticating DNS responses with DNSSEC, its DNS management safeguards users from being misdirected to malicious websites. Additionally, AppTrana WAAP provides visibility into network and service performance through detailed analytics and reports on DNS queries and responses
Utilize DNS Firewalls
DNS firewalls can provide an extra layer of protection by blocking malicious queries and responses before they reach the network. By analyzing DNS traffic for anomalies, a DNS firewall can help mitigate the effects of DNS reflection attacks and other DNS-based threats.



