What is DNS Spoofing?
DNS Spoofing also known as DNS Tampering or DNS Redirection, is a cyberattack where malicious actors alter DNS records to redirect users to fake websites without their knowledge. The aim is usually to steal sensitive data, such as login credentials, financial information, or other personal details. This attack can lead to phishing, malware distribution, or unauthorized access to user data.
How Does DNS Spoofing Work?
- When you enter a website address, such as www.example.com, into your browser, your device requests the DNS server to locate its IP address.
- The DNS server looks it up, finds the correct address, and sends it back.
- Your browser then uses this IP address to load the website.
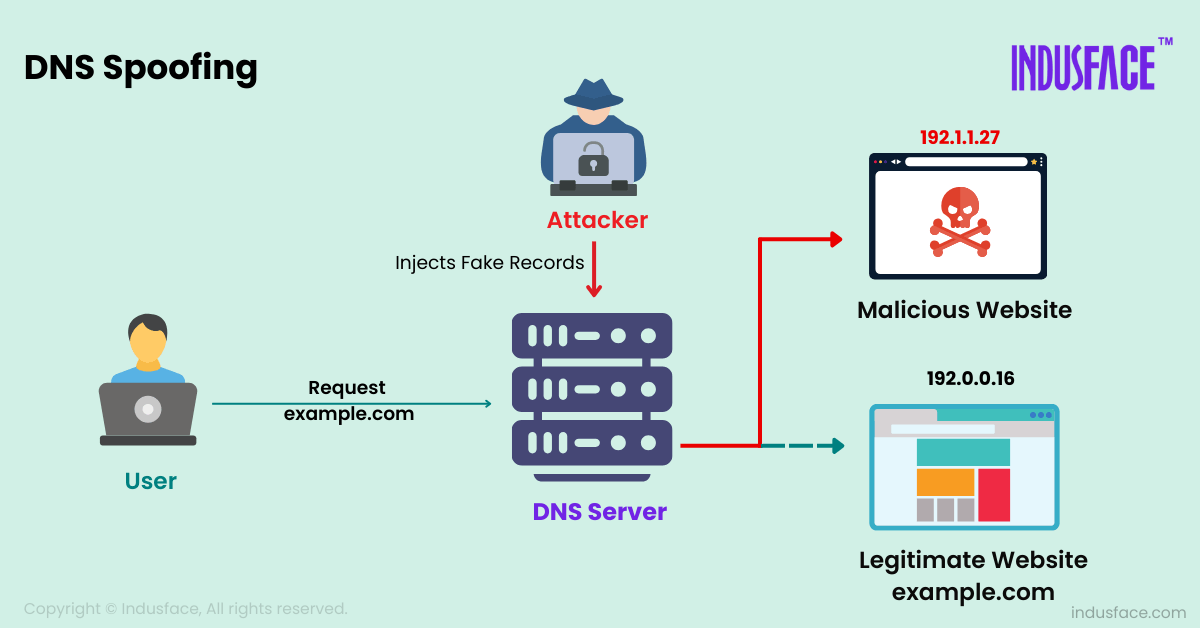
In DNS Spoofing, an attacker sends fake data to the DNS server, tricking it into saving the wrong IP address. So, the next time you try to visit that site, you are sent to a fake website without knowing it.
Attackers often use this trick to spread malware or steal sensitive data.
Types of DNS Spoofing Attack
There are several ways hackers can perform DNS Spoofing, including:
- DNS Cache Poisoning: This is the most common form. Hackers send fake responses to a DNS server so that it saves the wrong IP addresses for certain websites. When users request the same website, they are redirected to the malicious site instead of the real one.
- Man-in-the-Middle Attack: In this method, the hacker intercepts communication between the user and the DNS server. By doing so, the attacker can alter the DNS request and direct the user to a fake site.
- DNS Hijacking: In this attack, hackers take control of the DNS server itself. Once they have control, they can reroute users to any website they want, usually without the users even realizing something is wrong.
DNS Spoofing Example – TTL Exploitation
Time-To-Live (TTL) is a fundamental concept in DNS (Domain Name System) that determines how long a DNS resolver should cache a DNS record before it needs to retrieve fresh data from an authoritative DNS server.
While TTL is designed to enhance the efficiency and speed of DNS lookups, attackers can exploit it as part of a DNS Spoofing strategy.
Here’s how attackers exploit TTL in DNS Spoofing:
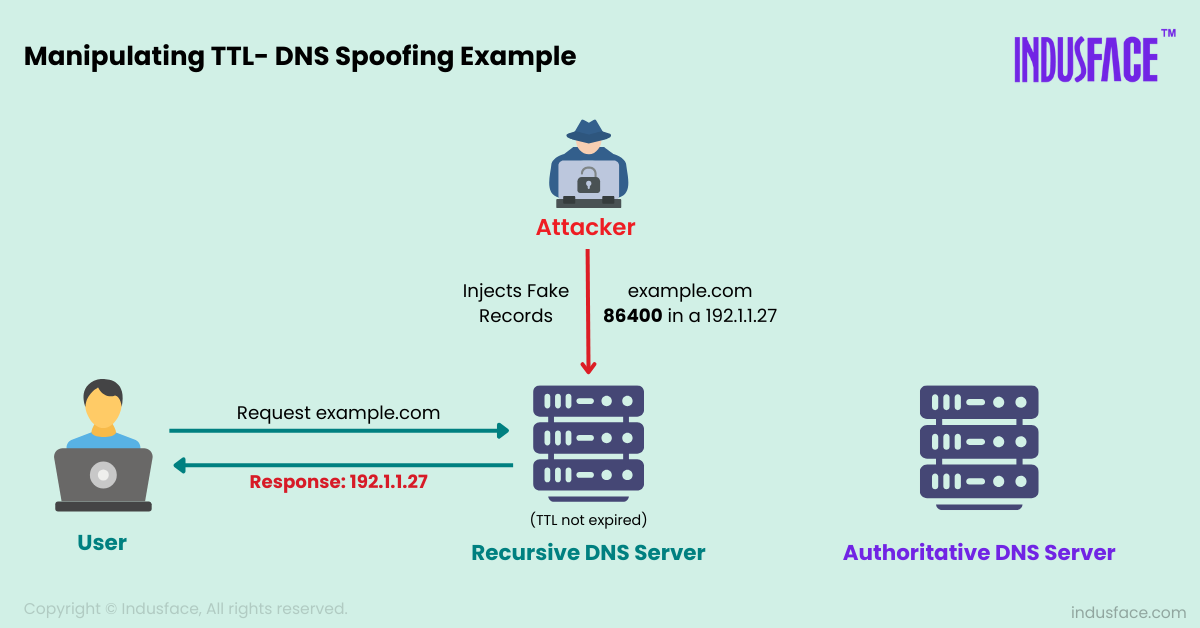
- Injecting Malicious DNS Records: In a typical DNS Spoofing attack, the attacker injects a forged DNS response that redirects users to a malicious IP address. This is usually done through methods like DNS Cache Poisoning.
- Modifying TTL Values: The attacker then manipulates the TTL value in the forged DNS response, setting it to an extended duration. By setting an artificially long TTL (e.g., 86,400 seconds or 24 hours), the attacker ensures that the poisoned DNS record remains in the cache for an extended period before it expires.
- Prolonging the Attack’s Impact: With an extended TTL, the DNS resolver will continue to provide the malicious IP address to users attempting to visit the targeted domain for the duration of the TTL.
The longer the malicious DNS record remains cached, the more difficult it becomes for network administrators to quickly detect and respond to the attack. Even after detection, clearing the cache across all resolvers may take time, further prolonging the impact.
How to Defend Against DNS Spoofing?
While DNS Spoofing is a significant threat, there are several measures individuals and organizations can take to defend against it:
Use DNSSEC (DNS Security Extensions) – DNSSEC adds cryptographic signatures to DNS data, ensuring the authenticity of the information. This prevents attackers from tampering with DNS responses and helps protect against DNS Spoofing and Cache Poisoning.
AppTrana WAAP’s DNS Management, supported by a managed service team, takes care of all aspects of configuration, maintenance, and security for an organization’s DNS servers. It also provides advantages like DNSSEC support, reporting, and more.
Enable HTTPS – Websites that use HTTPS provide encrypted communication between the user’s browser and the web server. Always check for the padlock symbol in the browser’s address bar when visiting websites, particularly when entering sensitive information.
Use Secure DNS Services – Some DNS providers offer enhanced security features to detect and block suspicious DNS traffic. Services like Google Public DNS and OpenDNS can provide an additional layer of protection against DNS Spoofing.
Keep Software and Systems Updated – Regularly update your operating systems, browsers, and security software to ensure that they include the latest security patches. Many vulnerabilities that attackers exploit for DNS Spoofing are addressed in security updates.
Monitor Network Traffic – Organizations should continuously monitor DNS traffic for signs of tampering. Unusual DNS responses or traffic patterns may indicate that a DNS Spoofing attack is underway.


