The DNS (Domain Name System), a fundamental protocol of the internet, was designed to resolve domain names to IP addresses. However, DNS tunneling exploits this system, turning it into a channel for data transfer, which poses significant security challenges for businesses and individuals alike.
What is DNS Tunneling?
DNS tunneling is a method of encoding the data of other protocols or malicious traffic within DNS queries and responses, effectively bypassing firewalls and other security defences that often overlook DNS traffic. In a typical DNS query, a user sends a request to resolve a domain name, and a DNS server responds with the IP address. DNS tunneling manipulates this process, embedding data into these seemingly normal DNS requests and responses.
How DNS Tunneling Works
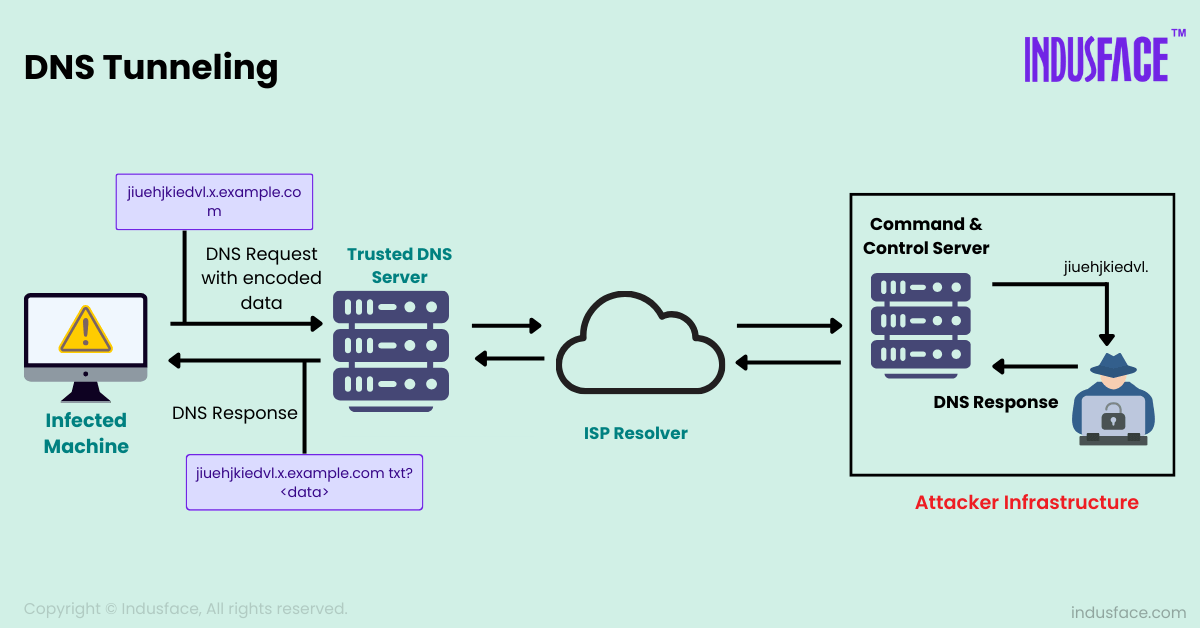
DNS tunneling typically involves these steps:
Establishing a Rogue Server: Attackers set up a rogue DNS server that can interpret DNS requests containing tunneled data.
Encoding Data: The attacker encodes data as part of DNS queries. Instead of sending a standard domain name, these requests carry the encoded data.
Tunneling Data: The rogue server decodes these DNS queries, processes the information, and sends back responses, thereby creating a tunnel.
Data Transfer: This two-way communication facilitates data transfer through DNS, allowing attackers to exfiltrate data or infiltrate malware undetected.
This DNS tunneling technique is particularly effective as many network security systems consider DNS traffic as benign and may not inspect it as rigorously as other types of traffic.
Use Cases of DNS Tunneling
DNS tunneling is often associated with malicious use cases, but it also has legitimate applications in cybersecurity and network administration. Here are examples of both:
Malicious Use Cases
Data Exfiltration
Data exfiltration occurs when attackers use DNS tunneling to transfer data from a compromised network. Sensitive information such as login credentials, intellectual property, or personal data can be encoded in DNS queries and sent to a rogue server, effectively bypassing network firewalls and intrusion detection systems. Check this article on DNS exfiltration.
Command and Control (C2) Communications
Many malware families use DNS tunneling to maintain C2 communication between compromised systems and attacker-controlled servers. Since DNS is typically a trusted protocol, attackers can use DNS queries and responses to send commands or receive updates without detection.
Bypassing Network Restrictions
DNS tunneling can help cybercriminals bypass network restrictions on a compromised system. For example, if a corporate firewall blocks certain ports or IP addresses, DNS tunneling allows attackers to establish covert channels for communication or data transfer.
Distributing Malware
Attackers can leverage DNS tunneling to infiltrate malware into a targeted network by encoding malware packets within DNS traffic. This method bypasses common security measures, especially in networks that do not inspect DNS requests.
Legitimate Use Cases
Remote Network Access
Organizations may use DNS tunneling for legitimate remote access purposes when other channels are restricted. For instance, DNS tunneling can create a connection to remote systems even in cases of strict network limitations, which can be useful for secure network access under controlled conditions.
Testing Security Defenses
Security teams often simulate DNS tunneling attacks to evaluate the effectiveness of their defensive controls. By understanding how an attacker might exploit DNS tunneling, they can better identify and mitigate vulnerabilities, strengthening the overall security posture.
Threat Intelligence and Research
Researchers use DNS tunneling to analyze malware communication methods and behavior patterns. By studying DNS-tunneled traffic, they can gain insights into attacker tactics, techniques, and procedures (TTPs), which aid in improving detection and prevention mechanisms.
DNS Tunneling Attacks in the Real-World
Several notable examples illustrate how DNS tunneling has been exploited in real attacks:
APT34 (OilRig)
In 2018, APT34, a hacking group allegedly linked to Iranian intelligence, used DNS tunneling as part of their cyber-espionage operations. They employed a tool called “DNSpionage,” which allowed them to exfiltrate data from compromised systems via DNS requests. By encoding sensitive information within DNS traffic, they evaded traditional detection methods and maintained long-term access to targeted networks.
SUNBURST (SolarWinds)
SUNBURST is a backdoor associated with the SolarWinds supply chain attack, which targeted thousands of organizations, including U.S. government agencies and private companies, by compromising the SolarWinds Orion software update.
SUNBURST used DNS tunneling as part of its reconnaissance and command-and-control (C2) process. Once the backdoor was installed on a compromised system, it sent encoded DNS queries to specific subdomains under attacker-controlled domains, enabling attackers to retrieve system information and determine if the infected system was of interest.
xHunt
xHunt is a malware campaign known for deploying various tools, such as “Hisoka” and “Kuwa,” which rely on DNS tunneling for data exfiltration and C2 communication. The use of DNS as a communication method allowed xHunt’s operators to stealthily control infected machines and siphon off data in environments with tight security.
Signs of DNS Tunneling and Key Indicators to Watch For
Detecting DNS tunneling requires close monitoring of DNS traffic to spot unusual patterns and behaviours. Here are the primary signs that may indicate DNS tunneling activity:
High Volume of DNS Queries to a Single Domain
When DNS tunneling is in use, the compromised system often makes frequent DNS queries to an attacker-controlled domain. This high query volume, especially to uncommon or unknown domains, is a strong indicator.
Unusually Long or Complex DNS Query Names
DNS tunneling often involves encoding data within the DNS query string, resulting in excessively long, random-looking, or complex domain names. This can include many characters, numbers, or patterns that are not typical for regular domain requests.
Frequent TXT Record Requests
TXT records are sometimes used to transfer encoded data in DNS tunneling attacks. An unusual increase in TXT record requests (versus the typical DNS records – A, MX, or AAAA) can be a red flag.
Regular Patterns of DNS Requests
DNS tunneling tools may generate requests at consistent intervals as they transmit data in small chunks. Regular, repetitive DNS queries, especially at unusual times or in large bursts, can indicate tunneling.
Unusual Query-to-Response Ratios
In DNS tunneling, the number of queries is often disproportionate to the volume of legitimate DNS traffic. For instance, seeing many queries to specific domains without corresponding, legitimate responses can indicate suspicious activity.
Uncommon or Unknown DNS Domains
Attackers often register new or obscure domains for tunneling purposes. Queries to domains with no business or common purpose can be worth investigating, especially if they persist over time.
High Data Volume in DNS Responses
If DNS response sizes are unusually large, especially in comparison to standard DNS responses, it may indicate data is being exfiltrated in those responses. DNS tunneling often encodes data within responses, increasing the packet size.
Increased Use of Non-Standard Ports for DNS Traffic
DNS traffic typically operates over port 53, but tunneling may sometimes occur over non-standard ports to avoid detection. Monitoring for DNS traffic on unusual ports can uncover suspicious activity.
Effective Ways to Prevent DNS Tunneling Attacks
Machine Learning and Behavioural Analytics: Machine learning algorithms can detect deviations in normal DNS behaviour and flag potentially malicious DNS tunneling. By establishing a baseline for DNS traffic patterns, any unusual deviations can trigger alerts.
Deep Packet Inspection (DPI): DPI tools can analyse DNS payloads for encoded data. While resource-intensive, this approach helps identify unusual or obfuscated content within DNS queries and responses, which is often characteristic of DNS tunneling.
DNS Response Policy Zones (RPZ): Organizations can implement RPZ to control DNS queries and prevent access to malicious domains. By configuring custom DNS response policies, security teams can block known malicious domains or redirect suspicious DNS requests.
DNS Firewalls: DNS firewalls filter DNS requests and responses based on blacklists and whitelists of domains. These firewalls can block DNS requests to known malicious servers or restrict access to only trusted DNS servers.


 AppTrana WAAP Platform
AppTrana WAAP Platform

