Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks are the most common threats that can significantly disrupt online services.
To effectively fight against these attacks, it’s essential to understand their types, key differences, and appropriate defense strategies.
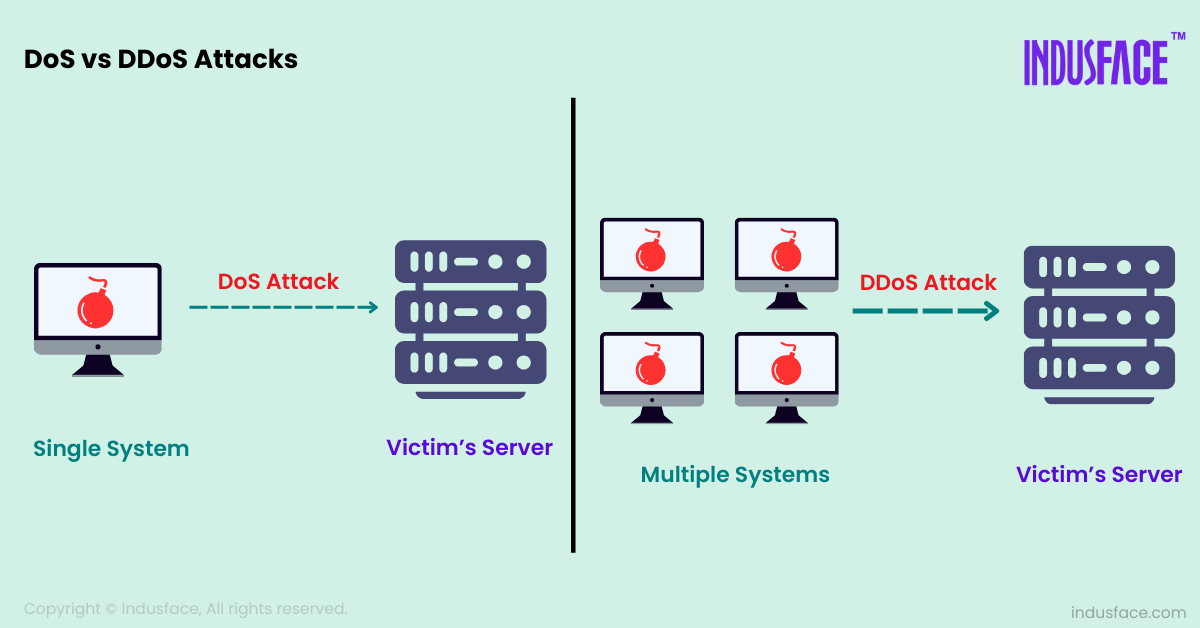
What is a Denial of Service (DoS) Attack?
A DoS attack aims to make a network, service, or website unavailable by overwhelming it with a flood of illegitimate requests.
This flood of traffic typically originates from a single source and aims to exhaust critical resources such as bandwidth, memory, or CPU.
Common Types of DoS Attacks:
- Ping of Death: Sending malformed or oversized packets via ping commands, causing the target system to crash. The packet size exceeds the maximum allowed size, causing buffer overflows.
- SYN Flood: Exploiting the TCP handshake process, attackers send a flood of SYN requests to a target server, causing it to allocate resources for connections that never complete.
- HTTP Flood: Sending seemingly legitimate HTTP GET or POST requests to a web server, overwhelming its resources. This type targets the application layer, making it difficult to distinguish from normal traffic.
What is a DDoS Attack?
A DDoS attack is an advanced version of a DoS attack. Here the malicious traffic comes from multiple sources, often thousands of compromised devices known as a botnet.
This distributed nature makes the attack more difficult to block because it originates from numerous IP addresses across various locations.
Read more about the most notorious DDoS attacks in history here
Common Types of DDoS Attacks:
- Volumetric Attacks: Consume the target’s bandwidth with massive amounts of data (e.g., UDP floods). They overwhelm the network infrastructure by flooding it with traffic.
- Protocol Attacks: Exploit weaknesses in network protocols (e.g., Ping of Death) to consume server resources or intermediate communication equipment.
- Application Layer Attacks: Target specific applications with requests that consume resources (e.g., HTTP GET/POST floods). These attacks focus on the application layer, making them harder to detect as they mimic legitimate user behavior.
For more on DDoS attack types, check out our blog covering types of DDoS attacks
DoS Vs. DDoS – Key Differences
| Key Characteristics | DoS Attacks | DDoS Attacks |
| Scale of Attack | Involves a single attacker or a single attacking system. The scale is limited to the capabilities of the individual attacker’s system. | Involves multiple attackers or systems such as a botnet. Therefore, DDoS attacks are significantly larger because of the collective power of many compromised devices. |
| Traceability | Easier to trace back to the source since it originates from a single location. | Much harder to trace because of its distributed nature. The attack traffic comes from numerous IP addresses, making it difficult to pinpoint the source. |
| Attack Complexity | Generally simpler to execute. Often involves basic tools and techniques that can be deployed with minimal technical knowledge. | More complex to orchestrate. Requires coordination of a botnet, which involves compromising multiple systems across different locations. |
| Mitigation Strategies | Can often be mitigated using basic security measures like firewalls, IP blacklisting, and rate limiting. | Requires more sophisticated defense mechanisms such as distributed network architecture, AI/ML driven behavioural analysis of traffic, and specialized DDoS protection services to filter out malicious traffic from legitimate traffic. |
| Impact and Recovery | Generally, causes a temporary disruption that can be resolved relatively quickly once the source is blocked. | Can cause prolonged disruption because of the sheer volume of traffic and the difficulty in distinguishing malicious traffic from legitimate traffic. Recovery often requires significant resources and time. |
How to Protect Against DoS and DDoS Attacks?
When defending against DoS and DDoS attacks, it is essential to have multi-layer protection in place. By dispersing network resources across multiple locations and balancing the load, you can protect against overwhelming any single server. Web Application Firewalls, Web Application and API Protection (WAAP) Platforms, and Intrusion Detection Systems (IDS) stand guard, inspecting incoming data and swiftly blocking any suspicious activity before it can cause harm.
With rate limiting in place, you can maintain control over the request flow, preventing any user from flooding your system.
Blacklisting IP addresses associated with malicious activity helps thwart further infiltration and recurrence of attacks. In times of heightened demand or targeted attacks, leverage scalable resources and cloud-based infrastructure to maintain service availability.
And if an attack does happen, there should be an incident response plan to detect, contain, and recover from it.
In addition to internal measures, you often need the support of DDoS protection services.
DDoS mitigation platforms like AppTrana WAAP offer specialized features to combat sophisticated DDoS attacks. These tools employ advanced AI and machine learning to analyse traffic and identify and block malicious traffic before it reaches the target network.
By leveraging the scale and expertise of these providers, organizations can augment their defenses and mitigate the impact of DDoS attacks more effectively.
Explore our comprehensive guide on the 15 best practices for protecting against DDoS attacks to gain further insights and best practices.


 AppTrana WAAP Platform
AppTrana WAAP Platform

