What is a Fraggle Attack?
A Fraggle attack is a type of DoS attack that targets a victim by flooding their network with a massive amount of spoofed User Datagram Protocol (UDP) traffic. The objective behind this attack is to overwhelm the network and cause genuine requests to time out, leading to service disruption.
While Fraggle attacks are less commonly heard about compared to other attacks like ICMP Attacks or Smurf Attacks, they can still wreak havoc on a network’s infrastructure & lead to disruption of services.
Fraggle Attack vs. Smurf Attack: What is the Difference?
Although the Fraggle attack and Smurf attack share many similarities, they differ in the type of traffic used to flood the network.
Fraggle Attack: In a Fraggle attack, the attacker uses UDP traffic, specifically targeting ports like 7 (Echo) and 19 (Chargen). The attacker sends a spoofed UDP packet to the broadcast address of a network, making it appear as legitimate though the victim is requesting responses from multiple devices, which then respond back to the victim, causing an overload of traffic.
Smurf Attack: Like the Fraggle attack, Smurf attacks involve sending spoofed packets to the broadcast address of a network, causing multiple devices to send replies to the victim, leading to a network overload. A Smurf attack, on the other hand, uses Internet Control Message Protocol (ICMP) traffic instead of UDP packets.
How Does a Fraggle Attack Work?
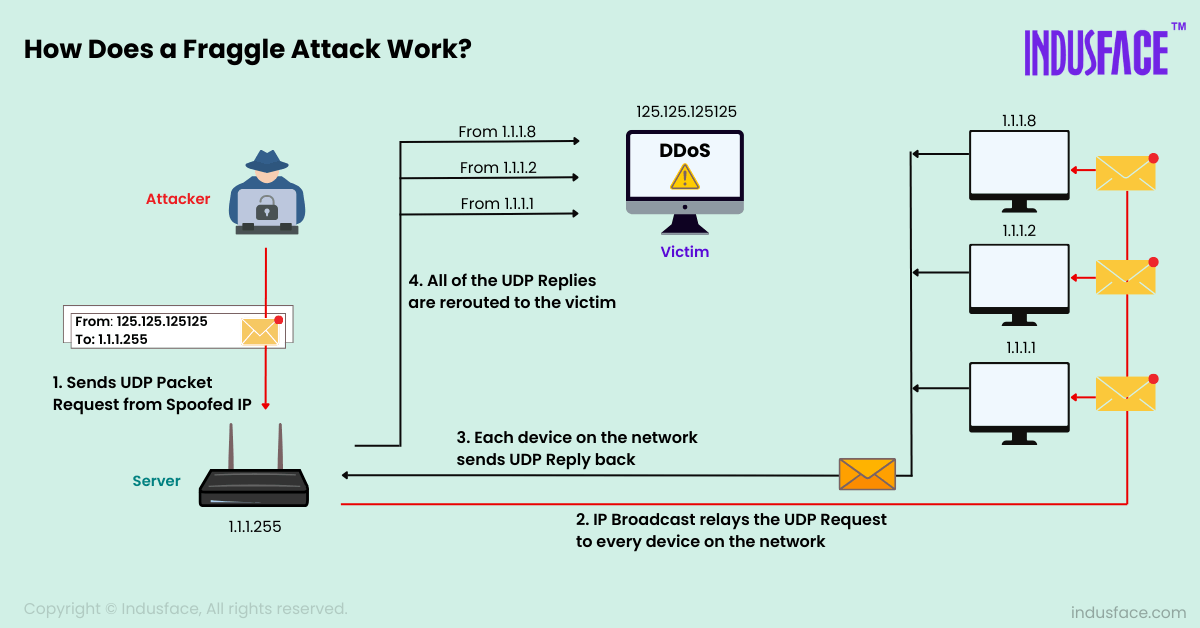
Spoofing Source IP Address: The attacker fakes the source IP address of the packets they send, making it appear as though the target’s device is the source & transfers these packets to the broadcast address of a network. The broadcast address makes sure that every device within the network receives the packet.
Devices Respond to Spoofed IP: The devices on the network, thinking they are responding to a legitimate request from the victim’s device, reply to the victim with UDP responses.
Overload: The victim’s device is flooded with an overwhelming number of UDP replies, consuming bandwidth and system resources, and potentially causing a denial of service.
How to Prevent Fraggle Attacks?
There are several strategies that organizations can adopt to mitigate these attacks:
Disable IP Broadcast on Routers: Since these attacks rely on sending traffic to the broadcast address, disabling IP-directed broadcasts on routers can prevent the Fraggle attack from reaching multiple devices in the network.
Rate Limiting: Rate limiting can restrict the number of requests a server accepts from a single IP address in a given time period which can limit the effectiveness of flooding attacks like Fraggle.
UDP Port Filtering:Configure network devices to filter UDP traffic on unnecessary ports (such as UDP port 7 and 19, which are commonly targeted in Fraggle attacks). Only allow UDP traffic on ports that are necessary for your organization’s operations.
Update Network Hardware: Modern routers and network hardware come with built-in protections against broadcast-based amplification attacks. Keeping network infrastructure updated can significantly reduce the risk of a Fraggle attack.
Deploy Anti-DDoS Solutions: In some cases, Fraggle attacks can be launched as part of a larger DDoS attack campaign. DDoS protection solutions like AppTrana screens network traffic to establish normal patterns. When a Fraggle attack triggers unusual spikes in UDP Echo or Chargen requests, it filters out the malicious traffic while letting legitimate traffic through. Using adaptive learning, the solution improves its ability to distinguish between attack traffic and genuine spikes, reducing false positives and maintaining consistent network performance.



