What is a Fragmented ACK Flood Attack?
A Fragmented ACK Flood Attack is a type of DDoS (Distributed Denial of Service) attack where the attacker sends a large volume of fragmented TCP ACK (acknowledgement) packets to a target server or network device.
These fragmented packets require the server to use additional resources to reassemble them, overwhelming its processing capabilities and leading to significant performance degradation or a complete denial of service (DoS).
A packet is a small piece of data sent over the internet, containing part of the original information and addressing details, which is later reassembled at the destination.
By using fragmented packets of legitimate TCP traffic, the attack often bypasses traditional DDoS defences, which focus more on obvious forms of malicious traffic. The fragmented nature of the packets makes it difficult to differentiate between normal and malicious traffic, allowing the attack to go undetected for extended periods.
TCP 3-Way Handshake – An Overview
To enable data flow between devices, a process known as the TCP 3-way handshake takes place, to ensure authorized communication. This handshake is a principal step in TCP/IP communication, building a secure and solid connection between a client and a server. It involves three key steps:
- SYN: The client initiates the connection by sending a SYN (synchronization) packet, signalling its intent to establish communication with the server.
- SYN-ACK: The server responds with a SYN-ACK packet to confirm receipt of the SYN packet and its willingness to communicate.
- ACK: Finally, the client sends an ACK packet back to the server, completing the association setup.
How Does a Fragmented TCP Flood Attack Happen?
While the TCP 3-way handshake establishes a secure connection, the handshake process itself can be manipulated to trigger different types of DDoS attacks.
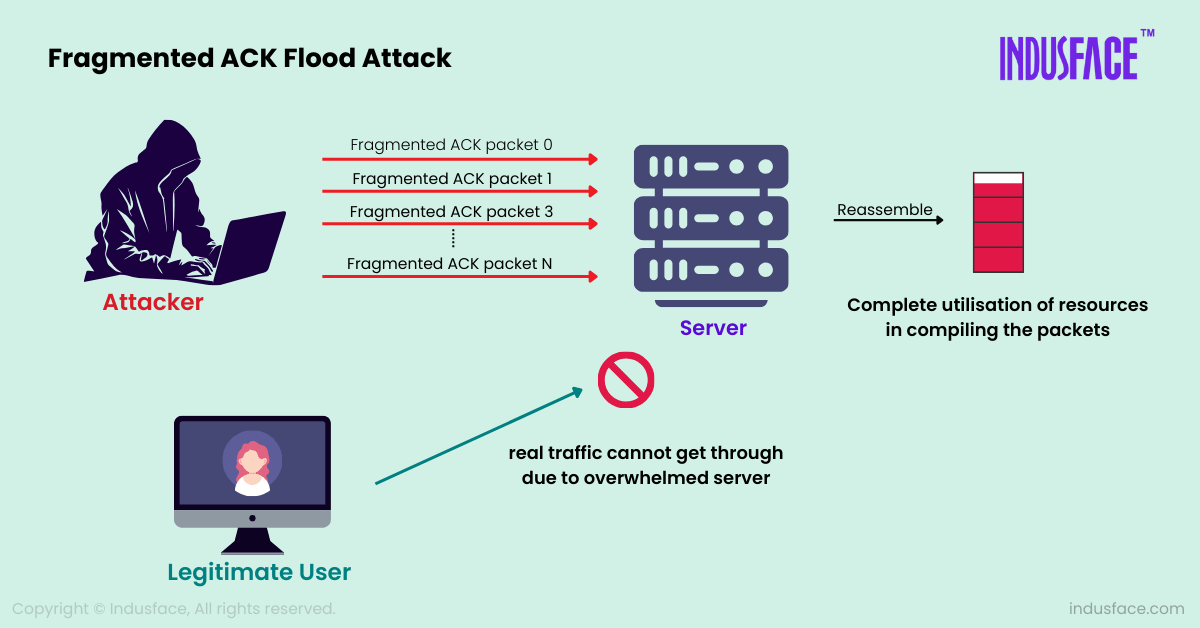
In the Fragmented ACK Flood Attack, for instance, the attackers exploit the TCP protocol by sending multiple fragmented ACK packets to a target server.
The attacker uses multiple compromised machines (a botnet) to generate fragmented ACK packets. These packets are outlined to be incomplete or inaccurately assembled. The fragmented ACK packets are then sent in large volumes to the target system. Since they are fragmented, the target system requires to exert more effort in reassembling and processing them.
The continuous flood of fragmented packets consumes significant resources on the target system, including CPU, memory, and network bandwidth. The target’s network stack is burdened with handling fragmentation and reassembly, which depletes resources. This resource exhaustion leaves little capacity to process additional requests from other users, resulting in severe slowdowns or even a DDoS attack.
When discussing TCP-based DDoS attacks, it is essential to understand the other methods attackers use to overwhelm a target server. Two noticeable DDoS attacks are the SYN Flood and ACK Flood. While each targets the server’s resources, they do so in distinct ways:
- Syn-Flood Attack overwhelms a target by sending a flood of TCP SYN requests, exhausting the server’s resources by leaving connections half-open and preventing legitimate connections from passing through.
- Ack-Flood Attack floods a target with a high volume of TCP ACK packets, overwhelming its processing capabilities and causing network slowdown or denial of service.
A successful Fragmented ACK Flood attack can cause severe disruption, such as e-commerce sites experiencing downtime and losing sales, financial institutions facing transaction halts, and critical infrastructure like healthcare or utilities becoming inoperable.
How to Stop Fragmented ACK Flood DDoS Attacks?
Anomaly Detection: Utilize an IDPS (intrusion detection and prevention system) with anomaly detection capabilities to spot unusual traffic behaviour, such as an unexpected surge in fragmented packets.
Rate Limiting: Implement rate limiting on TCP ACK packets or fragmented packets specifically. This restricts the number of such packets that can flow through the network at once, reducing the attack’s impact.
Traffic Shaping: Implement traffic shaping policies to manage bandwidth allocation, giving priority to legitimate traffic while throttling or delaying potentially malicious fragmented packets, ensuring that critical services remain uninterrupted.
Deep Packet Inspection (DPI): Use DPI tools to thoroughly examine the contents of fragmented packets, enabling the detection of malicious patterns. DPI can effectively filter out malicious traffic, stopping it from reaching critical systems.
Configure Network Devices to Drop Fragmented Packets: Implement network devices that can limit the number of fragments they process.
TCP Reassembly at the Network Perimeter: Implement TCP reassembly techniques at the network perimeter to inspect and filter fragmented packets before they reach internal servers. This can prevent the server from being overwhelmed by the need to reassemble these packets.
Access Control Lists (ACLs): Use ACLs to filter out malicious traffic, including fragmented packets from suspicious IP addresses or ranges.
Cloud-Based DDoS Protection: Use cloud-based DDoS protection solutions such as AppTrana that can absorb and filter out malicious traffic before it reaches your network. These tools are equipped to handle distinct types of DDoS attacks, including fragmented ACK floods.
Explore our in-depth blog on essential best practices for preventing DDoS attacks.


