What is an HTTP Flood Attack?
An HTTP flood is a type of DDoS (distributed denial of service) attack in which attackers send a huge number of HTTP requests to the victim server. Unlike volumetric attacks that rely on high traffic volumes, HTTP Flood attacks exploit legitimate-looking requests, making them harder to detect.
How Does HTTP Flood Attack Work?
Attackers Use Bots or Hijacked Devices: The attacker uses a network of bots or compromised devices (a botnet) to send a large volume of HTTP requests to the target server. These requests can be GET or POST, mimicking legitimate user traffic.
Server Overload: The server is overwhelmed by processing these requests, which consume resources like CPU, memory, and bandwidth. If the server is unable to handle the flood of requests, it becomes slow or unresponsive.
No Signature Detection: Because the requests appear normal and come from various sources, traditional security tools struggle to differentiate between genuine user traffic and malicious traffic.
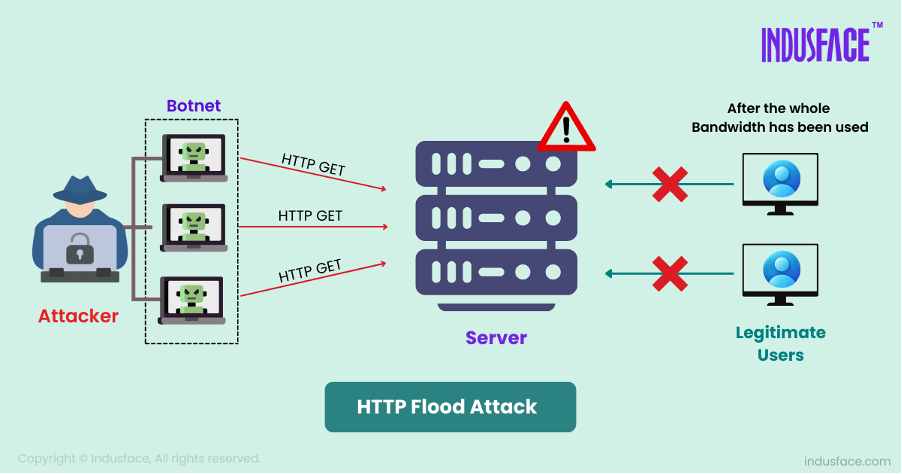
The goal of this attack is to drain the server’s resources (CPU, memory, bandwidth, etc.), slowing down or completely stopping its ability to process genuine requests, which results in downtime and service unavailability.
Types of HTTP Flood Attacks
HTTP GET Flood
Here, the attacker sends many HTTP GET requests to the target. Each GET request typically asks for specific resources like images, documents, or pages from the website. These requests demand server resources to process and deliver the requested information, and the overload can lead to server exhaustion.
Recursive HTTP GET Flood Attack
A Recursive HTTP GET Flood Attack is a variation of the standard HTTP GET flood where attackers leverage nested requests to exhaust server resources. Instead of simply flooding the target server with multiple GET requests, the recursive attack follows links or dynamically generates additional requests, creating a cycle that can be challenging to terminate.
This approach significantly amplifies the load on the server compared to a typical GET flood by forcing it to repeatedly process multiple dependent resource requests, making it even harder to mitigate using static rate limiting or IP-based blocking strategies.
HTTP POST Flood
HTTP POST flood attacks are comparatively more intense than GET floods. In this, the attacker sends large amounts of POST requests, which often require the server to process data, such as handling forms, uploading files, or running back-end functions. Since POST requests demand more computational resources, they are comparatively more challenging for the server to handle.
How to Prevent HTTP Flood Attacks ?
There are several steps organizations can take to prevent such attacks:
Rate Limiting – Limit the number of requests a user can make within a specific time frame (e.g., 10 requests per second) which prevents attackers from sending repeated requests to the server.
Web Application Firewall (WAF) – A WAF helps detect and block malicious HTTP requests by analysing traffic patterns. It can filter out suspicious requests based on IP reputation, behaviour, or other security rules.
IP Blacklisting – Block known malicious IP addresses, to preventing them from sending HTTP requests to the server.
Traffic Anomaly Detection – Use advanced traffic analysis tools to monitor for irregularities in the traffic patterns. If a sudden spike in requests occurs that does not align with typical usage, the tool can automatically flag or block that traffic.
Load Balancing – Distribute traffic across multiple servers or use a content delivery network (CDN) to prevent any single server from being overwhelmed by HTTP requests.
CAPTCHA Implementation – Use CAPTCHA to differentiate between bots and genuine users. Requiring users to complete a CAPTCHA prevents automated scripts from sending mass requests.
Application Layer DDoS Protection – Deploy DDoS protection solutions like AppTrana that focus on mitigating Layer 7 attacks, which are designed to disrupt the application layer (like HTTP Floods).


