What is an ICMP Flood Attack?
An ICMP flood attack, also known as a ping flood, is a type of Denial of Service (DoS) attack. It overwhelms a system by sending a huge number of ICMP packets, specifically echo requests (pings).
This overwhelms the target’s network resources, preventing it from managing legitimate traffic and rendering the system unresponsive.
When attack traffic comes from many devices, it turns into a DDoS (Distributed Denial-of-Service) attack, which can cause even more severe damage.
ICMP flood DDoS attacks can significantly impact systems and networks, ranging from immediate slowdowns to broader effects that disrupt business operations and financial stability.
How do ICMP(Ping) Flood Attacks Work?
ICMP is an internet layer protocol network devices use to communicate and diagnose network communication issues.
In an ICMP flood attack, the attacker sends a massive number of ICMP echo request packets to the target system. These packets are designed to produce an ICMP echo reply from the target.
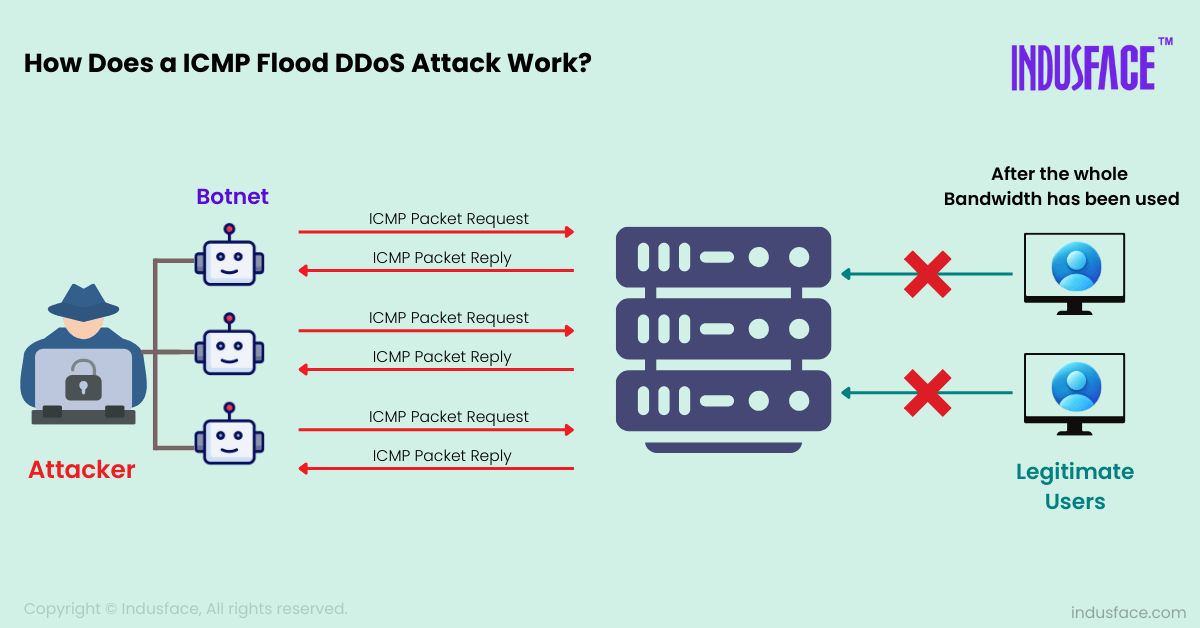
The target system becomes overwhelmed by the sheer volume of incoming ICMP packets. Processing each request and sending a reply consumes CPU, memory, and network bandwidth, leading to degraded performance or complete unavailability.
Types of ICMP Flood Attacks
ICMP ping flood attacks can be classified into three main types depending on the target and how the attacker’s IP address is resolved. Each type has distinct mechanisms and effects on network infrastructure.
- Targeted Local Disclosed
In a Targeted Local Disclosed ICMP flood attack, the attacker aims at a specific computer within a local network. This type of attack requires the attacker to have prior knowledge of the target’s IP address.
For example, an attacker inside a corporate network targets a specific workstation or server by continuously sending ICMP echo requests, causing the system to become unresponsive and disrupting normal business operations.
- Router Disclosed
In this type of DDoS attack, the attacker targets routers instead of individual computers. The goal is to disrupt the communication between computers on the network by overwhelming the router.
The attacker sends a high volume of ICMP echo request packets to the router’s IP address. Routers, being central to managing network traffic, can become overwhelmed by processing these packets, affecting their ability to route legitimate traffic efficiently.
Since routers are critical for directing traffic, their damage can lead to widespread network outages, affecting all connected devices.
Even if the router does not crash, the additional load can cause significant delays in packet forwarding, leading to increased latency for all network communications.
In severe cases, the router may crash or enter a fail-safe mode, resulting in a complete loss of network connectivity.
- Blind Ping
In a Blind Ping Flood attack, the attacker does not initially know the IP address of the target. Instead, they use external programs or techniques to discover the target’s IP address before launching the ICMP flood attack.
The attacker uses tools or services to scan for active IP addresses within a certain range or domain.
After identifying the target IP address, attackers generate a large volume of ICMP traffic to overwhelm the target’s network resources.
ICMP Flood Attacks Vs Other Network Attacks
ICMP Flood Vs. Ping of Death (POD)
An ICMP flood attack and a Ping of Death attack are both types of Denial of Service (DoS) attacks leveraging the ICMP protocol, but they differ in their methods and objectives.
The Ping of Death attack exploits a specific vulnerability in older operating systems or network devices. It involves sending ICMP packets larger than the maximum allowed size (often 65,535 bytes), causing a buffer overflow and potentially crashing the target system’s network stack.
While both attacks can lead to service disruptions, the ICMP flood attack is more about sheer volume and resource exhaustion, whereas the Ping of Death attack targets vulnerabilities in packet handling, making mitigation strategies distinct for each.
ICMP Flood vs. Smurf Attack
While an ICMP flood attack directly targets a system with a high volume of ICMP echo requests, a Smurf attack amplifies the impact by exploiting IP broadcast addresses.
In a Smurf attack, the attacker sends ICMP echo requests to the broadcast address of a network with the spoofed IP address of the target. This causes all devices on the network to respond to the target IP, overwhelming it with the responses.
ICMP Flood vs. SYN Flood Attack
ICMP Flood and SYN Flood attacks are distinct in their approach and impact. While ICMP Flood attacks flood the target with ICMP echo request packets, SYN Flood attacks flood the target with TCP SYN packets, using spoofed IP addresses to initiate TCP connections.
The target allocates resources to respond with SYN-ACK packets but awaits an ACK packet to complete the three-way handshake. As the attacker fails to send the final ACK, the target’s resources are tied up in incomplete connections, leading to service unavailability for legitimate users.
How To Prevent and Mitigate ICMP Flood Attack?
To prevent ICMP flood attacks, a multi-layered DDoS protection approach combining network configuration, monitoring, and security best practices is essential.
- Firewall Configuration
Start by configuring firewall rules to limit or block unnecessary ICMP traffic. Access your firewall’s management interface and create rules that deny inbound ICMP echo requests from untrusted sources and allow ICMP traffic only from known trusted IP addresses.
- Rate Limiting on Routers and Switches
Next, implement rate limiting on routers and switches to control the number of ICMP packets allowed per second, preventing network overwhelm. Access your router or switch configuration, set rate limits for ICMP traffic, and monitor the impact, adjusting as needed.
- Network Segmentation
Identify critical assets and segment your network using VLANs (Virtual Local Area Networks) to separate different parts of your network. Implement strict access controls between segments to limit ICMP traffic to necessary paths only.
- Intrusion Prevention Systems (IPS)
Select an IPS solution, install and configure it according to the vendor’s guidelines, and ensure it is set to detect and block ICMP flood patterns. Keep the IPS signatures up-to-date to detect the latest attack methods.
- Network Traffic Monitoring
Establish normal traffic baselines to identify anomalies and configure alerts for unusual spikes in ICMP traffic. Investigate alerts promptly and take action if an ICMP flood attack is detected.
- Regular Security Audits and Updates
Regularly conduct security audits and updates to maintain effective network and firewall configurations. Keep all network devices, firewalls, and software current with the latest security patches. Periodically review security policies to ensure they align with the latest threats and industry best practices.
- Implement DDoS Mitigation Solutions
Leverage DDoS mitigation solutions like AppTrana WAAP, which act as a shield against all types of DDoS attacks, ensuring the target system remains available and performs optimally.
These tools continuously monitor incoming traffic for patterns indicative of an attack. When abnormal traffic patterns are detected, the service filters out malicious traffic before it reaches the target network.
- Staff Education and Training
Conduct training sessions to educate IT staff about ICMP flood attacks and prevention techniques. Develop and practice incident response plans for handling ICMP flood attacks and keep staff informed about the latest security trends and threats.


