What is a LAND Attack?
A LAND (Local Area Network Denial) attack is a type of layer 4 DoS (denial-of-service) attack where the attacker sends a malicious packet to the target system with the source and destination addresses set to the same IP address.
This causes the system to attempt to communicate with itself, leading to confusion and exhaustion of system resources. It was first discovered in 1997 by security researcher Pieter Zatko.
How Does a LAND Attack Work?
A LAND attack exploits gaps in the way certain operating systems and network devices handle network packets.
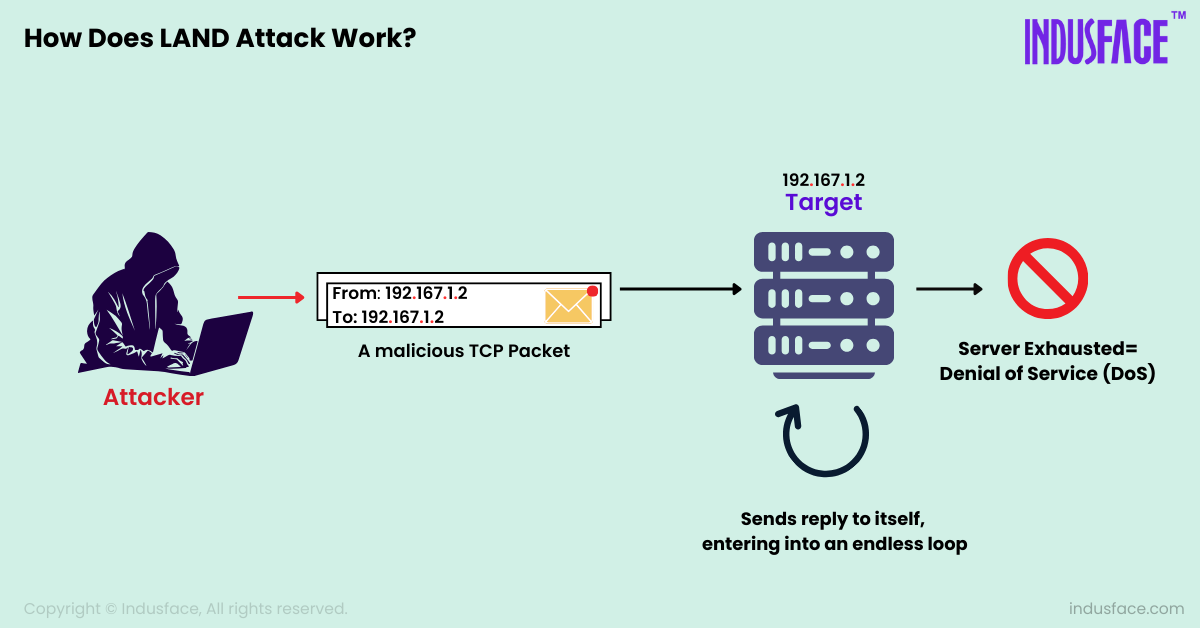
The attacker crafts a malicious packet with both the source and destination IP addresses set to the same value. When this packet is sent to the target system (server), it appears to be both coming from and going to the identical IP address. As a result, the system tries to process and respond to the packet as if it were communicating with itself.
This can lead to excessive CPU and memory usage as the system repeatedly processes the packet, causing severe performance issues or even system crashes. The attack disrupts normal operations and causes a denial of service (DoS) for legitimate users.
LAND attacks take advantage of weaknesses in packet processing mechanisms, which older systems and devices may not handle correctly, although modern systems have mechanisms to mitigate these vulnerabilities.
Impacts of a LAND Attack
Although the LAND attack is an older form of network attack, its impact can still be significant if systems are not properly protected. Here are a few of the possible impacts:
Denial of Service: The primary goal of a LAND attack is to cause a denial of service by making the target system unavailable to legitimate users. In severe cases, the continuous processing of attack packets can lead to a system crash, requiring a restart or manual intervention to restore functionality.
Increased Security Risks: An unprotected system vulnerable to a LAND attack might also be vulnerable to other forms of attacks. Exploiting the same vulnerabilities used in LAND attacks can enable attackers to launch broader network compromises.
How to Protect Against LAND Attacks?
Here are some effective measures to safeguard your systems:
Update and Patch Systems: Ensure that all network devices, operating systems, and software are up to date with the latest patches and security updates. Many vulnerabilities exploited by LAND attacks have been addressed in modern updates, so regular checks are crucial.
Configure Network Devices Properly: Configure network devices such as routers and switches to filter out malformed packets and prevent them from reaching your systems. Implement strict packet filtering rules to help you block malicious traffic. Enable anti-spoofing features in routers to drop packets with identical source and destination IPs.
Segment Your Network: Segmenting your network can limit the spread of a LAND attack. By isolating critical systems on separate network segments, you can reduce the impact of an attack on your overall network.
Train Employees: Train employees by educating them on recognizing signs of network attacks, including unusual system behaviour, and providing guidelines on reporting and responding to potential threats like LAND attacks. Regularly conduct drills and simulations to reinforce their awareness and response skills.
Cloud-based DDoS Protection Solutions – Solutions like AppTran WAAP can also help mitigate LAND attacks by filtering and blocking malicious traffic before it reaches your network. These solutions can identify abnormal traffic patterns and block malicious packets that might signal an attack.


