What is a Path Traversal Vulnerability?
Path Traversal or Directory Traversal attack occurs when an application improperly validates file paths, allowing attackers to manipulate the input to access files or directories outside the application’s intended scope. This vulnerability is often exploited in applications that allow users to upload, download, or retrieve files based on user-provided input.
How It Works
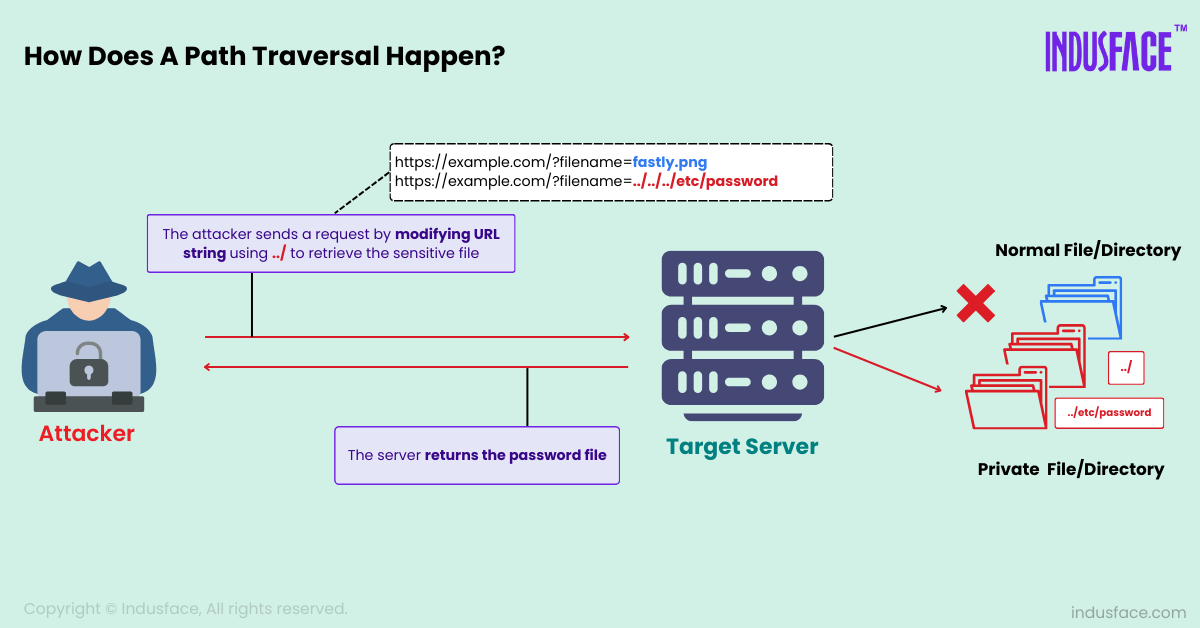
Attackers use special characters like ../ to traverse up the directory hierarchy. By chaining these sequences, they can move outside the permitted directory and access sensitive files. For instance:
Input: ../../etc/passwd
Result: Retrieves the passwd file containing user information on UNIX-based systems.
Common Targets
- Configuration files (e.g., config.php, .env)
- System files (e.g., /etc/passwd, C:\Windows\system32\drivers\etc\hosts)
- Log files
- Source code files
How Does Path Traversal Happen?
Path traversal typically occurs when a web application improperly validates user input used to construct file paths. Here’s a breakdown of how this vulnerability can be exploited:
Unvalidated User Input
Applications often use user-provided input to specify file paths. If this input isn’t sanitized, attackers can inject path traversal sequences such as ../ or ..\ to navigate to parent directories and access files outside the intended directory.
Improper File Path Construction
The vulnerability becomes severe if the application concatenates user input with file paths without validating or restricting the resulting path.
Dynamic File Loading
Applications that dynamically load files based on user input without proper validation are prime targets for directory traversal attacks.
Examples of Directory Traversal Attack
File Retrieval in Websites
<?php
$file = $_GET['file'];
include("/var/www/files/" . $file);
?>
If an attacker inputs ../../../../../etc/passwd as the file parameter, the application includes and displays the contents of /etc/passwd. This demonstrates how a poorly secured application can be manipulated to leak sensitive data.
Path Traversal with Encoding
In many cases, developers implement basic filters to block traversal patterns like ../. However, attackers can bypass these filters using URL encoding, which represents characters in a different format.
Example: Let’s revisit the file retrieval feature in a web application:
<?php
$file = $_GET['file'];
include("/var/www/files/" . $file);
?>
Instead of directly entering ../, an attacker encodes it as %2e%2e%2f. When processed by the application, the encoded input decodes back to ../, successfully bypassing basic input filters.
Input: %2e%2e%2f%2e%2e%2f%2e%2e%2fetc/passwd
Result: Retrieves the passwd file.
This demonstrates how encoding techniques can evade detection and exploit path traversal vulnerabilities effectively.
Attackers often combine traversal with other vulnerabilities like Remote File Inclusion (RFI). For example, they could use path traversal to access external files or malicious scripts stored in other directories, compounding the risk and enabling wider exploitation.
Mitigation Note: To counter such attacks, normalize and decode user inputs before validation. Implement strong checks to reject traversal patterns, even when encoded.
Impact of Path Traversal Vulnerability
Directory traversal vulnerabilities can lead to:
Exposure of Sensitive Data: Attackers can access passwords, application configuration files, and other critical data, potentially exposing the system to further risks.
Privilege Escalation Attacks: If system files are accessed or modified, attackers can escalate their privileges, gaining unauthorized access to restricted areas.
System Compromise: Reading files like “/etc/passwd” or “/etc/shadow” on Linux systems can enable further attacks.
Application Exposure: Attackers may gain access to the application’s source code, revealing more vulnerabilities.
Data Breaches: Unauthorized exposure of sensitive data may lead to legal liabilities and reputational damage.
How to Detect Path Traversal Vulnerability
Detecting path traversal vulnerabilities involves a combination of automated tools and manual testing:
Code Analysis – Inspect the application’s file-handling code for improper sanitization or validation of user-supplied inputs.
Dynamic Application Security Testing (DAST) – Use tools like DAST scanners to inject payloads systematically and check for signs of unauthorized access.
Indusface WAS, an AI-powered DAST scanner, detects Path Traversal vulnerabilities by injecting crafted payloads and analysing server responses for unauthorized file access, ensuring accurate detection with zero false positives.
Manual Penetration Testing – Skilled testers can identify vulnerabilities by experimenting with file path inputs. For example, submitting ../../etc/passwd in file path parameters can help assess susceptibility.
Log Monitoring – Analyse server logs for unusual file access patterns, such as repeated requests for paths containing ../.
How to Prevent Path Traversal Attacks
Below are effective strategies to minimize the risk:
Input Validation
Restrict user input to a predefined set of acceptable values using a whitelist.
Use input validation libraries to sanitize file paths and remove any unauthorized sequences like ../ or null bytes.
Use Secure APIs
Avoid using insecure file APIs that concatenate user input with file paths.
Opt for high-level functions or libraries that handle file paths securely, such as Java’s java.nio.filepackage or Python’s os.path module.
Limit File Access
Implement a virtual directory to segregate public files from sensitive system files.
Restrict access to directories by using the principle of least privilege.
Canonicalization
Resolve file paths to their canonical form before accessing them. This ensures the application understands the actual file location and can enforce proper access restrictions.
Avoid Disclosure of Sensitive Information
Configure error handling to prevent the application from exposing sensitive file paths in error messages.
Regular Security Audits
Periodically review your application’s code, configuration, and infrastructure for vulnerabilities.
Use automated vulnerability scanners as part of your continuous integration/continuous deployment (CI/CD) pipeline.
Indusface WAS integrates seamlessly with your CI/CD pipeline to automate vulnerability scans, create patch tickets, and send logs to SIEMs, ensuring early detection and efficient remediation.
Access Control
Enforce robust access control mechanisms to ensure only authorized users can access specific files or directories.
How AppTrana WAAP helps in preventing Path Traversal
AppTrana WAAP effectively prevents Path Traversal attacks through proactive vulnerability detection and real-time threat mitigation. Its built-in DAST scanner identifies Path Traversal vulnerabilities during routine scans, enabling you to address them before they can be exploited.
On the prevention front, AppTrana thoroughly analyzes all incoming HTTP requests, decodes encoded payloads, and detects malicious patterns such as ../ or obfuscated traversal sequences. Once identified, unauthorized access attempts are instantly blocked, ensuring they never reach the server.
Even in unpatched environments, AppTrana provides robust protection through virtual patching. When a Path Traversal vulnerability is detected, the managed security team creates tailored rules to block specific traversal patterns. These rules are instantly deployed at the WAF level, intercepting and rejecting any malicious requests attempting directory traversal.
With advanced threat intelligence and machine learning algorithms, AppTrana continuously adapts to evolving attack methods, delivering uninterrupted protection.


