What is Ping of Death?
The “Ping of Death” (PoD) is a type of Denial of Service (DoS) attack where attackers send excessively large ping packets to a computer system or network device. This can lead to the target system crashing, becoming unstable, or experiencing other malfunctions.
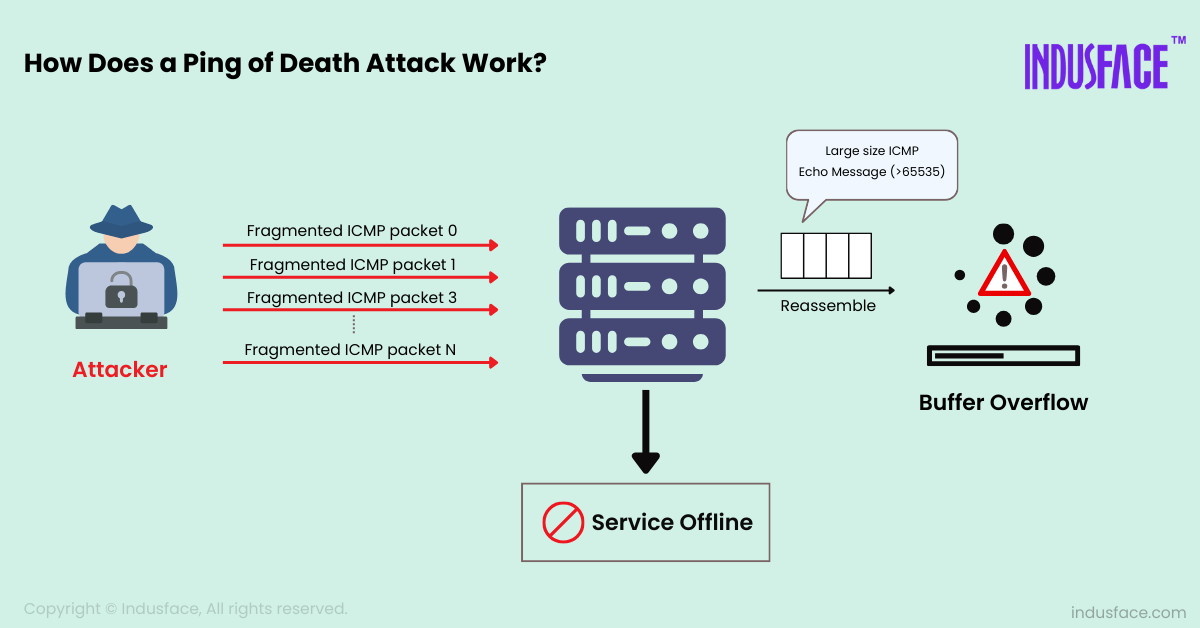
What is the Process of Ping of Death Attack?
ICMP Protocol: The attack specifically exploits the ICMP (Internet Control Message Protocol), commonly used for network diagnostics. One of the functions of ICMP is to send “ping” messages to check the reachability of a network device.
It sends error messages and operational information indicating success or failure when communicating with another IP address.
Packet Fragmentation: Normally, an ICMP packet is 64 bytes, but it can be as large as 65,535 bytes, including the IP header. In a Ping of Death attack, the attacker sends an ICMP packet that exceeds this maximum size by fragmenting the packet.
Reassembly: When the target system receives these fragments, they are reassembled to form the original oversized packet. Due to the excessive size, the reassembled packet exceeds the buffer allocated by the system for handling such packets.
System Crash: The target system, unable to handle the oversized packet, may crash, freeze, or restart. The system’s network stack overflows, causing unpredictable behavior and disrupting normal operations.
Check out the effective ways to detect and mitigate buffer overflow attacks.
Examples of Ping of Death Attack
2013 IPv6 Networks Attack
In August 2013, the Ping of Death attack targeted IPv6 networks by exploiting a flaw in the ICMP implementation for IPv6.
The main targets were Windows XP & Windows Server 2008 R2 systems. These operating systems were particularly vulnerable due to a weakness in their handling of OpenType fonts.
Disabling IPv6 on affected systems could have prevented the attack. Additionally, patching the operating systems was crucial in protecting against this vulnerability.
2020 TCPIP.sys Vulnerability
Another significant resurgence of the Ping of Death attack occurred in October 2020. This time, the vulnerability was found in the Windows component TCPIP.sys, a critical kernel driver.
The vulnerability affected multiple versions of the Windows OS, making any unpatched system susceptible to attack.
Attackers exploited a vulnerability in TCPIP.sys by sending malformed ICMP packets. When these packets reached the target system, the kernel driver was unable to handle them, leading to a hard crash and subsequent reboot.
Modern operating systems have been fighting these threats with updates since the late 1990s. Despite this, old vulnerabilities can sometimes reappear.
That said, it is important to understand the strategies to prevent DDoS attacks and ping of death.
How To Prevent the Ping of Death?
Mitigating a Ping of Death DDoS attack requires a multi-layered approach, combining network configuration, system updates, and active monitoring.
Here are detailed steps to mitigate such attacks:
System and Network Hardening
- Ensure all operating systems and network devices are updated with the latest security patches. Most modern systems have been patched to handle oversized packets properly.
- If ICMP (ping) is not necessary for your network operations, consider disabling it. Be aware that this may impact network diagnostics and troubleshooting. Alternatively, restrict ICMP to trusted sources only.
- Set up firewalls to block oversized or fragmented ICMP packets. Many firewalls can be configured to detect and drop such packets automatically.
Network Monitoring and Detection
- Deploy IDS/IPS systems that can detect and block malicious traffic patterns, including oversized ICMP packets.
- Regularly monitor network traffic for unusual patterns that might indicate an ongoing attack.
Rate Limiting and Throttling
Configure rate limiting on routers and firewalls to control the rate of ICMP requests.
Example for a Cisco router:
access-list 100 permit icmp any any echo
access-list 100 permit icmp any any echo-reply
access-list 100 deny icmp any any
rate-limit access-group 100 10 20 50 conform-action transmit exceed-action drop
Redundant and Scalable Infrastructure
Use load balancers and distribute your network services across multiple servers and locations. This makes it harder for a single point of attack to take down your entire network.
Utilize cloud-based DDoS protection services from providers like AppTrana WAAP. These tools are designed to mitigate DDoS attacks across layers 3 to 7. They utilize advanced AI and machine learning to analyze traffic patterns, detecting and blocking malicious traffic before it impacts the target network.
Incident Response Plan
Develop and regularly update an incident response plan specifically for DDoS attacks. This plan should include steps for identifying an attack, mitigating its effects, and restoring normal operations.
Conduct regular drills to ensure your team is prepared to respond quickly and effectively.


