What is an SSDP Attack?
An SSDP attack is a type of Distributed Denial of Service (DDoS) attack that exploits the SSDP protocol (Simple Service Discovery Protocol) to overwhelm a target server with a flood of unwanted traffic.
Attackers use this technique to amplify the amount of data sent to the target, effectively consuming the target’s bandwidth and resources, rendering services unavailable to legitimate users.
How Does an SSDP Attack Happen?
Finding Vulnerable Devices: Attackers first scan the internet for devices that have the SSDP protocol enabled. Many devices with UPnP (Universal Plug n Play) turned on are improperly configured, allowing anyone to discover and exploit them.
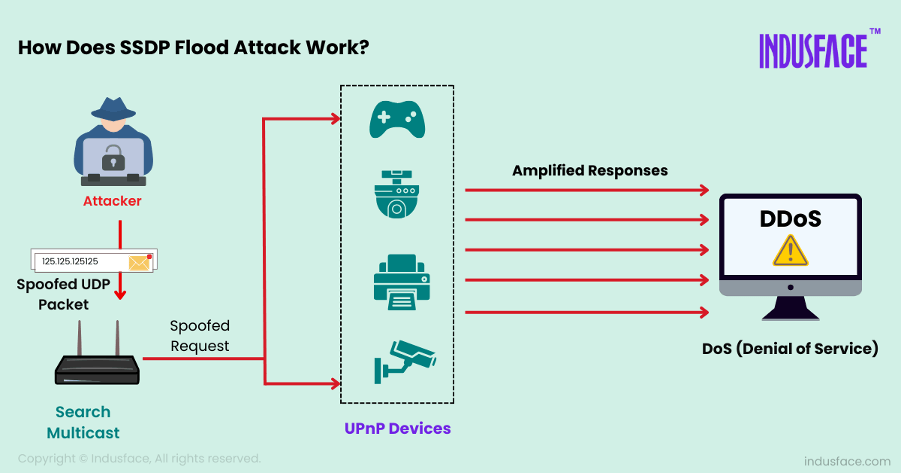
Sending Spoofed Requests: By spoofing the source IP address, the attackers make it seem as though the request came from the target.
Amplifying Responses: Vulnerable devices, unaware that they are participating in an attack, respond to the SSDP requests. Since the responses are significantly larger than the original request (amplification), this increases the total data being directed at the target.
Overwhelming the Target: The responses from multiple devices converge on the victim’s server or network, consuming bandwidth and causing services to slow down or become entirely unavailable.
How to Prevent SSDP Attacks?
Disable UPnP on Devices: The easiest way to prevent SSDP-based attacks is to disable UPnP on devices where it isn’t necessary. UPnP can introduce security vulnerabilities, especially if the device is exposed to the internet.
Filter Incoming Traffic: Filtering incoming SSDP responses at your firewall can help protect against SSDP reflection attacks. Firewalls can be configured to block traffic from known vulnerable SSDP devices or limit responses from non-standard ports.
Deploy Network Monitoring Tools: Use network monitoring and intrusion detection systems (IDS) to watch for abnormal traffic patterns. These tools can help in the early detection of DDoS attempts, allowing for quicker response and mitigation.
Rate Limiting: Enforcing rate limits on incoming requests can prevent your infrastructure from becoming overwhelmed. Rate limiting ensures that no single IP address can send an excessive number of requests within a short period, helping mitigate the effects of reflection/amplification attacks.
Use Access Control Lists (ACLs): Configure Access Control Lists (ACLs) on your router or firewall to block SSDP requests from entering or leaving your network unless they originate from trusted sources. ACLs can restrict access to SSDP services based on IP addresses or other criteria.
Use DDoS Protection Solutions Employ a DDoS protection software that can detect and mitigate SSDP-based attacks before they reach your network. These solutions not only filter out malicious traffic but also ensure that legitimate users continue to have uninterrupted access, providing a seamless experience even during attempted attacks.



