In April 2024, a record-breaking TCP ACK flood hit nearly 840 million packets per second. This attack originated from around 5,000 different IP addresses.
Despite the global attack, two—thirds of the traffic was funneled through just four U.S. PoPs (Points of Presence). This intensity of traffic makes the attack both effective and hard to mitigate.
This blog will explore the mechanics of TCP ACK DDoS attacks, their impacts, and effective mitigation strategies.
What is a TCP ACK Attack?
A TCP ACK attack is a type of DDoS attack that targets the Transmission Control Protocol (TCP) by flooding the victim with a massive volume of ACK (Acknowledgment) packets. These packets are part of the TCP handshake process, used to confirm the receipt of data between two endpoints in a network connection.
TCP ACK attacks operate primarily at the OSI model’s Transport Layer (Layer 4). This layer is responsible for end-to-end communication and error recovery between devices.
How Does an ACK Flood Attack Work?
To understand how an ACK flood attack works, it is crucial to understand the basics of the TCP handshake process:
- SYN Packet: The client sends a SYN packet to the server to initiate a connection.
- SYN-ACK Packet: The server responds with a SYN-ACK packet to acknowledge the request.
- ACK Packet: The client sends an ACK packet to confirm the connection establishment.
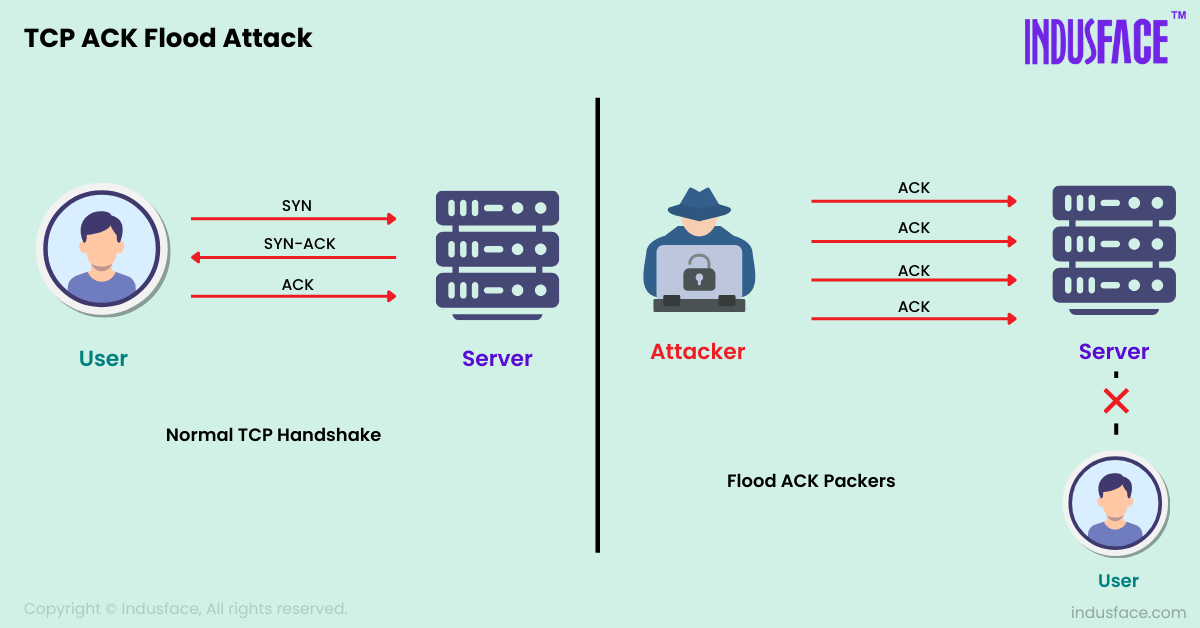
In an ACK flood attack, the attacker skips the initial SYN packet and directly sends a flood of ACK packets to the target. This can lead to several damaging effects:
- Resource Exhaustion: The target server’s resources are consumed in processing the incoming ACK packets, leaving little to no resources for legitimate traffic.
- Network Congestion: The high volume of ACK packets can saturate the network, causing delays and packet loss.
- Service Disruption: Legitimate users may experience slow responses or complete service outages as the server struggles to handle the attack.
TCP Ack Flood vs TCP Syn Flood Attacks
While both TCP ACK and SYN Flood attacks target the Transport Layer, they use different types of packets and have distinct impacts on the target’s network infrastructure.
In TCP Ack attack, the attacker sends a massive number of TCP ACK packets to the target. In a SYN Flood attack, the attacker sends a high volume of TCP SYN (synchronize) packets to the target. The attack exploits the fact that the initial handshake process requires the target to maintain half-open connections, consuming resources and potentially leading to service unavailability. Learn more about the TCP SYN Flood attack here.
How to Prevent TCP ACK Attack?
Preventing and mitigating TCP Ack flood requires a multi-faceted approach involving both proactive measures and real-time responses. Here’s a detailed guide to prevent such attacks:
Network Architecture and Redundancy
Designing your network with redundancy and scalability can help manage the impact of TCP ACK attacks. Implementing load balancing distributes incoming traffic across multiple servers or data centers, reducing the load on any single point.
Content Delivery Networks (CDNs) can further mitigate attacks by dispersing traffic globally. Additionally, ensuring that your network infrastructure is scalable helps in handling sudden surges in traffic.
Rate-Based Limiting and Filtering Rules
Configuring rate limits helps control the number of packets allowed through the network within a given timeframe. Specific filtering rules based on traffic characteristics can block packets that exceed normal rates, thereby reducing the impact of the attack.
DDoS Protection Software
DDoS protection solutions are designed to absorb and mitigate large-scale attacks before they impact your network infrastructure. Choosing a reputable service provider with a proven track record is key. Ensure that the service is properly integrated into your network architecture and configure protection parameters to specifically address TCP ACK attacks.
User Education and Awareness
Providing training sessions and sharing best practices can improve your organization’s preparedness and response to DDoS threats. Ensuring that staff are aware of how to recognize and respond to potential attacks helps in maintaining a secure network environment.
Also check out detailed guide on best practices to prevent DDoS attacks.
By implementing these detailed steps, you can effectively prevent and mitigate TCP ACK attacks, ensuring robust protection for your network infrastructure against these disruptive threats.


