What is UDP Flood Attack?
A UDP Flood Attack is a type of DDoS attack that overwhelms the target system with a flood of User Datagram Protocol (UDP) packets. UDP is one of the core protocols of the Internet Protocol (IP) suite, commonly used for tasks like streaming video or online gaming, where speed takes priority over reliability.
Attackers exploit the connectionless nature of UDP to send a relentless stream of packets, overwhelming the network and disrupting its ability to function normally. This overload can cause significant network degradation or even complete system shutdown.
How Does a UDP Flood Attack Happen?
Attack Initiation: The attacker generates a large volume of UDP packets using a botnet or other means, directing them toward the target’s IP address. These packets often have spoofed IP addresses, making it difficult to trace the source.
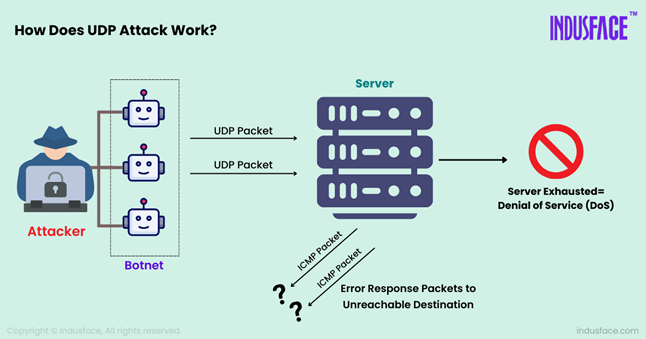
Server Overload: The packets are sent to random ports on the target system. Since UDP is connectionless, the target system is forced to check for an application listening on each of those ports.
No Application Response: When no application is found on a port, the target system typically responds with an ICMP “Destination Unreachable” packet, further consuming its resources.
System Exhaustion: As the volume of incoming packets increases, the server becomes overwhelmed, leading to network performance degradation or complete denial of service.
How to Prevent UDP Flood Attacks
Here are some proactive measures:
Implement Rate Limiting: This technique controls the number of requests a server can handle within a specified time frame, preventing it from being overwhelmed. Get a detailed insights on rate limiting.
Use Intrusion Detection and Prevention Systems (IDPS): An IDPS can monitor network traffic for signs of an attack and automatically respond by blocking malicious traffic.
Disabling Unnecessary UDP Services: If certain UDP services are not required, disabling them can reduce the attack surface & limits the number of potential entry points an attacker can exploit.
Engage in Regular Security Audits: Regular security audits help in identifying vulnerabilities that could be exploited in an attack.
Deploy DDoS Protection Solutions: Comprehensive DDoS protection solutions like AppTrana detect and block suspicious traffic in real-time, including UDP flood attacks. Using machine learning and behavioural analysis, they identify abnormal traffic patterns and automatically block malicious IP addresses, often from botnets. These solutions can also dynamically adjust thresholds based on the target’s capacity, ensuring that legitimate traffic is prioritized, while attack traffic is mitigated.



