What is Web Skimming Attack?
Web skimming is a type of cyberattack in which malicious code (usually JavaScript) is injected into a legitimate website or web application typically targeting e-commerce or payment pages, to steal sensitive information like credit card details.
Key Characteristics of Web Skimming
- Client-Side Attack: The malicious code executes in the user’s browser rather than on the server, making it harder to detect using traditional server-side security measures.
- Data Interception: Web skimming typically targets forms where users enter personal information, such as credit card details, names, and passwords.
- Stealthy Operation: The attack is often invisible to both the user and the website owner. The user may not even realize their data has been stolen until it’s too late.
- No Visible Changes to the Website: Unlike some other attacks, web skimming does not alter the appearance or functionality of the website. It operates in the background, making detection difficult.
How Does Web Skimming Work?
Web skimming typically occurs in the following stages:
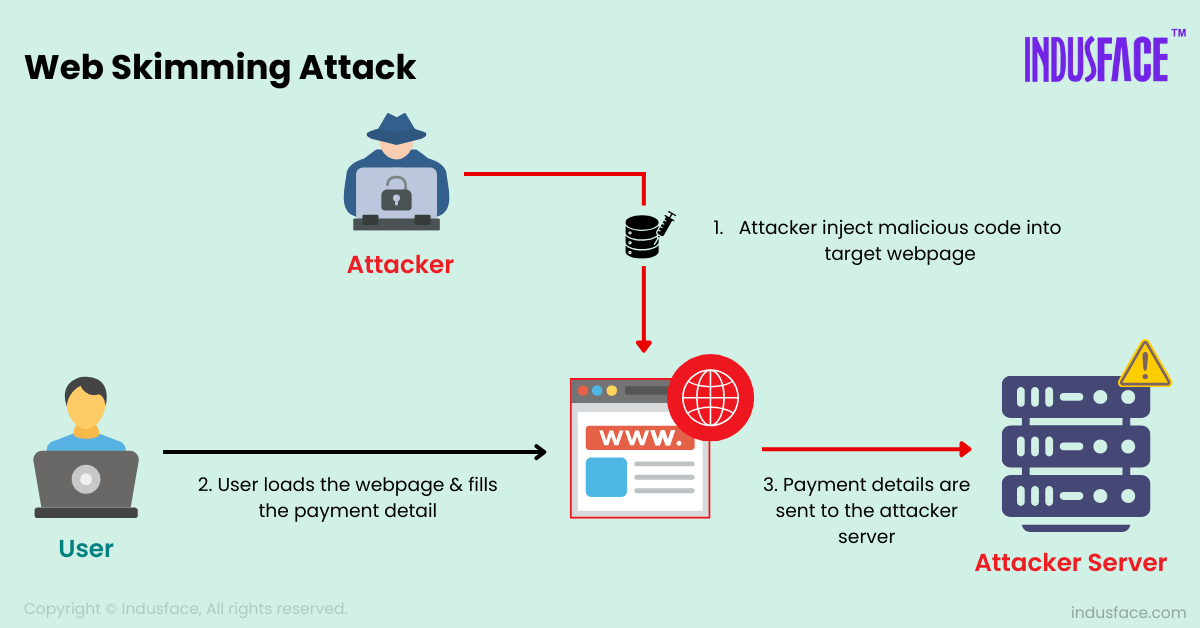
Malicious Script Injection
Attackers inject malicious JavaScript code into a legitimate website. This can be done through various methods, including exploiting vulnerabilities in the website’s code, compromising third-party scripts, or infecting the website through supply chain attacks (e.g., if a third-party service or plugin is compromised).
Once the malicious code is injected, it becomes part of the website’s resources and executes in the browser of anyone who visits the site.
User Interacts with the Website
When a user visits the compromised site, the injected malicious code begins to execute. Typically, this happens when the user fills out sensitive information, such as entering their credit card details or personal data in a checkout form.
Data Capture
The malicious script silently captures the data as it is entered into the form. This could include sensitive details like credit card information, login credentials (username, password), Billing addresses and Social security numbers.
Data Transmission to Attacker
Once the data is captured, the malicious script sends it to an external server controlled by the attacker. The data may be sent in real time, or it could be stored temporarily and sent at a later time.
Data Exploitation
Once the attacker receives the stolen data, they can use it for a variety of malicious purposes, including committing fraudulent transactions, selling the stolen data on the dark web, or using it to steal identities.
Web Skimming Attacks in the Real World
Several high-profile incidents in recent years have brought attention to the dangers of web skimming:
Magecart Attacks
The Magecart group is perhaps the most well-known and notorious cybercriminal group responsible for web skimming attacks. Magecart has targeted a wide variety of e-commerce websites, including some high-profile brands, injecting malicious scripts into the payment pages to steal customers’ credit card information. One notable attack occurred in 2018 when Magecart compromised the payment pages of British Airways, leading to the exposure of thousands of customers’ credit card details.
Ticketmaster Breach
In 2018, Ticketmaster suffered a breach that was caused by web skimming. A third-party vendor that Ticketmaster used to process payments was compromised, and the attackers injected malicious JavaScript into the checkout page. The attack led to the theft of customer payment information over several months before it was discovered.
Newegg Attack
In 2018, Newegg, an online electronics retailer, was also targeted by a web skimming attack. The attackers injected malicious JavaScript into the site’s checkout page, which captured customer payment data as it was entered. This breach went undetected for several months, affecting hundreds of thousands of customers.
The Impact of Web Skimming
Web skimming can have severe consequences for both businesses and consumers. Some of the major impacts include:
Legal and Non-compliance Penalties
Web skimming attacks that expose customer data can lead to severe legal consequences. In regions like the EU, the General Data Protection Regulation (GDPR) mandates strict data protection requirements. A breach from web skimming could result in significant fines and legal actions.
Additionally, businesses handling payment information must comply with the PCI DSS. With the release of PCI DSS 4.0, security measures have become even stricter for organizations processing sensitive payment data.
PCI DSS Requirements for Web Skimming Protection:
- Requirement 6.4.3: This focuses on reducing the risk of skimming by managing the attack surface on payment pages. It requires organizations to:
- Maintain a detailed inventory of all scripts on payment pages.
- Approve and document the purpose of each script.
- Ensure each script’s integrity to prevent unauthorized alterations.
- Requirement 11.6.1: This mandates monitoring for tampered scripts. Organizations must set up alerts for unauthorized changes to scripts, allowing for quick detection and action.
Loss of Customer Trust
When a business is compromised by a skimming attack, the damage to its reputation can be significant. Consumers who have had their personal data stolen may lose trust in the brand and choose to shop elsewhere. If the breach affects high-profile customers or gets widespread media attention, it can severely damage the business’s credibility.
Financial Loss
While the website owner may not directly lose money from a skimming attack, the costs associated with resolving the breach can be significant. Businesses often have to spend money on forensic investigations, legal fees, and notifying affected customers. Additionally, companies may face fines and regulatory scrutiny if sensitive customer data is exposed.
How to Protect Your Website from Web Skimming
Preventing web skimming requires a proactive, multi-layered approach. Here are some key strategies for protecting your website from this type of attack:
Keep Software and Plugins Updated
Web skimming often occurs through vulnerabilities in outdated software or plugins. Regularly updating your website’s platform, third-party libraries, and other software components ensures that known vulnerabilities are patched and reduces the risk of exploitation.
Monitor Third-Party Services
Many web skimming attacks are launched through third-party services, such as payment gateways and advertising networks. Be sure to monitor and audit the security of any third-party services you integrate into your website. Ensure they follow best practices for security.
Use Strong Payment Gateways
When handling payment information, always use a secure, trusted, and PCI DSS-compliant payment gateway. Never store sensitive customer information directly on your site unless absolutely necessary, and consider using tokenization to store payment data securely.
Regular Vulnerability Scanning
Regular vulnerability scanning and penetration testing can help identify potential weaknesses in your website that could be exploited by attackers. Be sure to scan for any potential injection points that could allow malicious JavaScript to be inserted into your site.
Monitor for Anomalies
Use real-time website monitoring tools to track any anomalies, such as unusual spikes in network traffic or suspicious external requests. Early detection of web skimming attacks can help prevent further damage.
Use Content Security Policy (CSP)
Implementing a Content Security Policy (CSP) can greatly reduce the risk of malicious script injection. CSP allows you to define which domains are allowed to serve JavaScript, blocking any unauthorized scripts from running.
AppTrana’s Client-Side Protection integrates CSP headers to prevent malicious code injection, detect malicious scripts, and monitor JavaScript behaviour, strengthening your security.
Watch how AppTrana defends your site from client-side attacks by effectively tracking and controlling all JavaScript files.



