What is a Botnet?
A botnet is the collection of malware-infected computers and networked devices (IoT, smart devices, etc.) that work together under the control of a single malicious actor or an attack group often called a “botmaster”.
Such a network is also referred to as a zombie army, with each infected device being called a bot/ zombie.
Botnets are known to be behind the biggest DDoS attacks of the past few years, from the Dyn attack in 2016 to the Mirai botnet-led attacks exploiting command injection vulnerability in 2023.
How Many Bots Are in a Botnet?
The number of bots in a botnet can vary widely, ranging from a few thousand to over a million compromised devices.
For example, the Hide ‘n Seek botnet has around 24,000 compromised devices, while the Mirai botnet, which significantly disrupted internet usage on the US East Coast in 2016, is believed to have had 800,000 to 2.5 million infected devices.
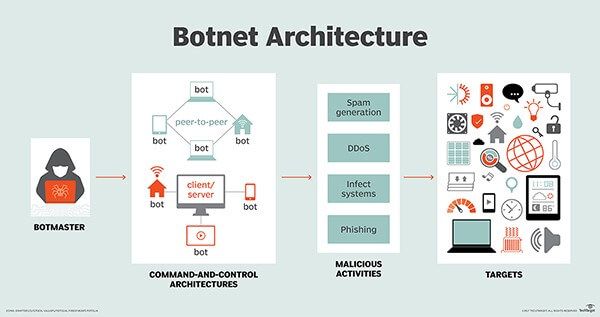
How Do Botnets Work?
Infection Phase
The botmaster initiates the creation of a botnet by distributing malware through various channels.
These include sending malicious email attachments, setting up drive-by downloads on compromised websites, exploiting software vulnerabilities, and deploying Trojan horse programs that appear legitimate but contain malicious code.
Once a device executes this malware, it becomes compromised and joins the botnet as a “bot” or “zombie.” The malware gains control by exploiting system vulnerabilities or deceiving the user into granting necessary permissions.
Communication Phase
Once infected, bots need to communicate with the botmaster for instructions. This is facilitated through a Command and Control (C&C) infrastructure.
In centralized C&C setups, bots connect to a single server or a small cluster of servers, often using protocols like HTTP/HTTPS or IRC.
In more sophisticated botnets, a decentralized peer-to-peer (P2P) approach is used, where bots communicate directly with each other, forming a resilient and difficult-to-disrupt network.
To ensure confidentiality and avoid detection, the communication between bots and the C&C server is typically encrypted.
Command Execution Phase
Bots regularly communicate with the C&C server or their peers to obtain new instructions. These commands direct the bots to perform various malicious activities.
Common tasks include
- Launching DDoS attacks by flooding targets with excessive traffic
- Executing extensive spam campaigns through bot networks
- Stealing sensitive data via keylogging techniques
- Engaging in crypto jacking activities to mine cryptocurrencies illicitly
- Committing click fraud to generate fraudulent ad revenue
- Employing bots as proxies to direct malicious traffic and hide the source of attacks
Maintenance and Expansion Phase
To maintain and expand the botnet, the botmaster can update the malware on infected devices, enhancing their capabilities and improving evasion techniques.
The botmaster continually seeks to recruit new bots by propagating the malware through already infected devices or exploiting new vulnerabilities.
This process ensures that the botnet remains robust and can compensate for any bots that are detected and removed by security measures.
Common Types of Botnet Attacks
A botnet attack refers to malicious activities orchestrated using a network of compromised computers or devices (known as bots) under the control of a cybercriminal.
Botnets execute various types of attacks, each posing a significant threat to businesses. Here are some typical botnet attack methods:
DDoS Attack
Botnets are commonly used to launch DDoS attacks, where a large number of bots simultaneously send a flood of traffic to a target website or server. This exhausts the target’s resources, making it inaccessible to legitimate users.
Get more insights on DDoS Botnet here.
Spam Campaigns
Botnets are often employed to send out massive volumes of unsolicited emails. These spam emails may contain phishing links, advertisements, or malware attachments. By using a botnet, attackers can bypass email filters and reach a large number of recipients, increasing the likelihood of successful attacks. Learn more about spam bots here.
Credential Stuffing
In credential stuffing attacks, botnets use previously leaked usernames and passwords to attempt logins on various websites and services. Bots systematically try these credentials across multiple platforms, exploiting users who reuse passwords.
Data Theft
Botnets can steal sensitive information from infected devices. This includes capturing keystrokes (keylogging), taking screenshots, accessing stored files, and exfiltrating data to the botmaster. Stolen data can include personal information, financial details, and intellectual property.
Click Fraud
In click fraud attacks, bots are used to generate fake clicks on online advertisements. This artificially inflates the number of clicks, generating revenue for the attacker or causing financial loss to the advertisers. Click fraud can distort marketing analytics and waste advertising budgets.
Cryptojacking
Botnets can exploit the computing power of compromised devices for cryptocurrency mining. This type of attack, known as cryptojacking, can significantly slow down the performance of the compromised devices and increase electricity usage, resulting in higher costs for the victims.
Financial Fraud
Botnets can be used to carry out financial fraud, such as automating transactions, manipulating stock prices, or executing unauthorized bank transfers. These attacks can cause significant financial losses and disrupt financial markets.
Social Media Manipulation
Botnets can be deployed to create and manage fake social media accounts. These accounts can be used to spread misinformation, generate fake likes and followers, and influence public opinion. Social media botnets can manipulate online discourse and amplify certain messages or campaigns.
Examples of Botnet Attacks
Mirai Botnet
The Mirai botnet attack, launched in late 2016, was one of the most famous cyberattacks in recent history. It targeted IoT devices by exploiting their default or weak passwords. The botnet’s massive scale allowed it to infect hundreds of thousands of devices, which were then used to launch powerful DDoS attacks.
These attacks interrupted major websites and services, including popular platforms like Twitter, Spotify, and Netflix, highlighting the vulnerabilities of IoT devices and the potential for widespread internet disruption caused by botnet attacks.
Zeus Botnet
The Zeus botnet, also known as Zbot, is a notorious example of malware designed to steal sensitive information from infected devices. It surfaced around 2007, primarily affecting Windows-based systems.
Zeus infects computers through malicious email attachments, drive-by downloads, or exploit kits. Once installed, it operates stealthily to capture sensitive data.
The Zeus botnet was responsible for numerous financial fraud incidents, including unauthorized bank transactions and identity theft. It targeted financial institutions and individuals alike, causing substantial financial losses and reputational damage.
Mariposa
Mariposa, discovered in 2008, was a sprawling botnet infecting millions globally through sophisticated malware known as “Butterfly Bot.” It enabled cybercriminals to remotely control compromised devices, facilitating extensive theft of personal and financial data.
Gorilla Botnet
The newly identified Gorilla botnet, built on Mirai’s leaked code, has launched extensive DDoS attacks in over 100 countries, executing more than 300,000 attack commands. This botnet targets IoT devices and cloud hosts using various flood methods, such as ACK and SYN floods, and exploits a vulnerability in Apache Hadoop YARN RPC for remote code execution.
How to Protect Your Device from Botnets?
Botnets present a dual threat to businesses: they can infect one or multiple devices within your network or pool their resources to conduct DDoS and other targeted attacks against your business infrastructure.
Check out the 10 effective botnet detection best practices to protect your business from attacks.
It’s crucial to prevent devices from joining botnets to avoid potential issues such as higher internet costs and compromised data. Legal consequences can also be severe if devices are involved in botnet-driven attacks.
Here are effective botnet protection strategies to protect devices:
- Strong Passwords: Create and enforce strong passwords across all devices and accounts to prevent unauthorized access by botnet malware.
- System Maintenance: Regularly wipe and restore systems to eliminate potential malware infections and restore system integrity.
- Code Execution Control: Restrict execution permissions for third-party code to trusted and whitelisted entities only, minimizing the risk of malware infiltration.
- Software Updates: Ensure devices are regularly updated with the latest security patches and software updates to minimize vulnerabilities botnets exploit.
- WAAP Implementation: WAAP defends against DDoS attacks by analyzing traffic patterns in real time, filtering out malicious botnet traffic, and employing behavioral analysis to detect anomalies. Integrated bot management complements these defenses, providing comprehensive protection against various botnet threats like credential stuffing and data scraping and prevent botnet attacks.
How to Disable an Existing Botnet?
- Understand how bots communicate with each other and the C&C infrastructure, whether through centralized or P2P methods.
- Immediately isolate infected devices from the network to prevent the botnet from spreading.
- Disconnect compromised systems from both the internet and internal networks to contain the spread of malicious activities.
- Block communication channels used by the botnet to connect with C&C servers. This involves blocking specific IP addresses, domains, or ports associated with botnet operations.
- Implement firewall rules and network filtering to prevent bots from communicating with C&C servers or other compromised devices.
- Continuously monitor network traffic to detect any attempts by bots to reconnect to C&C servers or switch to alternative communication channels.


 AppTrana WAAP Platform
AppTrana WAAP Platform