What is a DDoS Attack?
A DDoS (Distributed Denial of Service) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming it with a flood of internet traffic.
Unlike a DoS (Denial of Service) attack, which typically comes from a single source, the distributed nature of a DDoS attack makes it significantly more difficult to counter and can cause widespread disruption.
DDoS attacks have been around for a long time and continue to evolve. In Q1 2024, DDoS attacks surged by 76% compared to the previous year, with over 875 million attacks recorded – according to State of Application Security Report.
DDoS attacks can cause significant financial losses, damage to reputation, and disruption of critical services, highlighting the importance of robust defenses and mitigation strategies for organizations and service providers.
Examples of DDoS Attacks
The Distributed Denial of Service attacks have been a significant issue in cybersecurity. Here are a few notable examples:
1. Mafiaboy Attack (2000)
In 2000, ‘Mafiaboy,’ a 15-year-old hacker named Michael Calce, disrupted major websites like CNN, Dell, and Yahoo!, causing stock market chaos and prompting the creation of modern cybercrime laws.
2. Estonia Attack (2007)
In April 2007, Estonia experienced a massive DDoS attack targeting government, financial, and media services amid political tensions with Russia over a WWII monument, marking a significant early instance of cyber warfare and leading to the development of international cyber warfare laws.
3. GitHub (2018)
GitHub, a popular code hosting platform, experienced a DDoS attack in 2018 that lasted for several days. The attack involved a massive influx of traffic aimed at overwhelming their servers.
4. Dyn (2016)
Dyn, a major DNS service provider, was targeted by a series of DDoS attacks in 2016. These attacks disrupted access to many high-profile websites, including Twitter, Netflix, and Reddit, by targeting Dyn’s infrastructure.
5. Estonia (2007)
In 2007, Estonia experienced a series of DDoS attacks that targeted government, banking, and media websites. These attacks were attributed to geopolitical tensions with Russia at the time.
6. ProtonMail (2015)
ProtonMail, a secure email service, faced a significant DDoS attack in 2015 shortly after its launch. The attackers demanded a ransom in Bitcoin, which ProtonMail refused to pay.
7. Mirai Botnet (2016)
The Mirai botnet infected IoT (Internet of Things) devices and was used in multiple DDoS attacks, including against Dyn in 2016. It demonstrated the vulnerability of IoT devices to being hijacked for malicious purposes.
Check out the most famous DDoS attacks in history.
How Does a DDoS Attack Work?
A DDoS attack works by overwhelming a target system, such as a website or server, with an excessive amount of traffic.
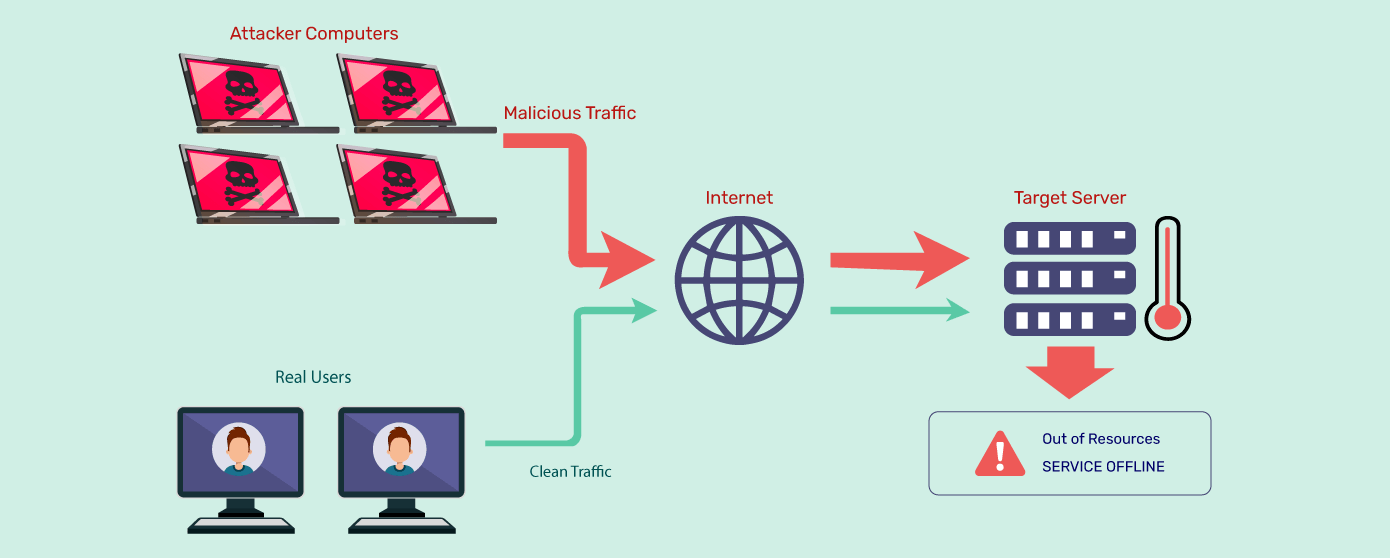
A DDoS attack typically involves the following steps:
1. Botnet Formation: The attacker assembles a network of compromised devices called a botnet. These devices, which can include computers, servers, IoT devices, or smartphones infected with malware, are under the attacker’s control and used to launch the attack.
2. Reconnaissance: The attacker identifies potential targets to disrupt or disable, such as websites, servers, or network infrastructure. This can be done through automated scanning or by gathering information about vulnerable targets.
3. Command and Control (C&C) Setup: The attacker sets up a command-and-control infrastructure to communicate with the compromised devices in the botnet. This infrastructure allows the attacker to issue commands and coordinate the attack.
4. Initiation of the Attack: The attacker instructs the botnet’s compromised devices to send massive amounts of traffic or requests to the target system. This flood of traffic overwhelms the target’s resources, such as bandwidth, processing power, or memory.
5. Traffic Redirection: To amplify the attack, the attacker may use techniques like IP spoofing or reflection/amplification attacks. IP spoofing involves forging the source IP address of the attacking traffic to make it appear as if it’s coming from legitimate sources.
Reflection/amplification attacks exploit vulnerable servers or services that respond with more traffic than they receive, magnifying the attack’s scale.
6. Impact on the Target: The target system’s resources become overwhelmed due to the excessive traffic volume. As a result, the target system experiences performance degradation or becomes completely inaccessible to legitimate users. This disruption can lead to financial loss, damage to reputation, and potential security vulnerabilities.
7. Attack Persistence: The attacker may attempt to sustain the attack over an extended period, adjusting the attack strategy or targeting different parts of the infrastructure to evade DDoS detection or mitigation measures.
Check out how the DDoS mitigation solution works.
What is the Motivation Behind DDoS Attacks?
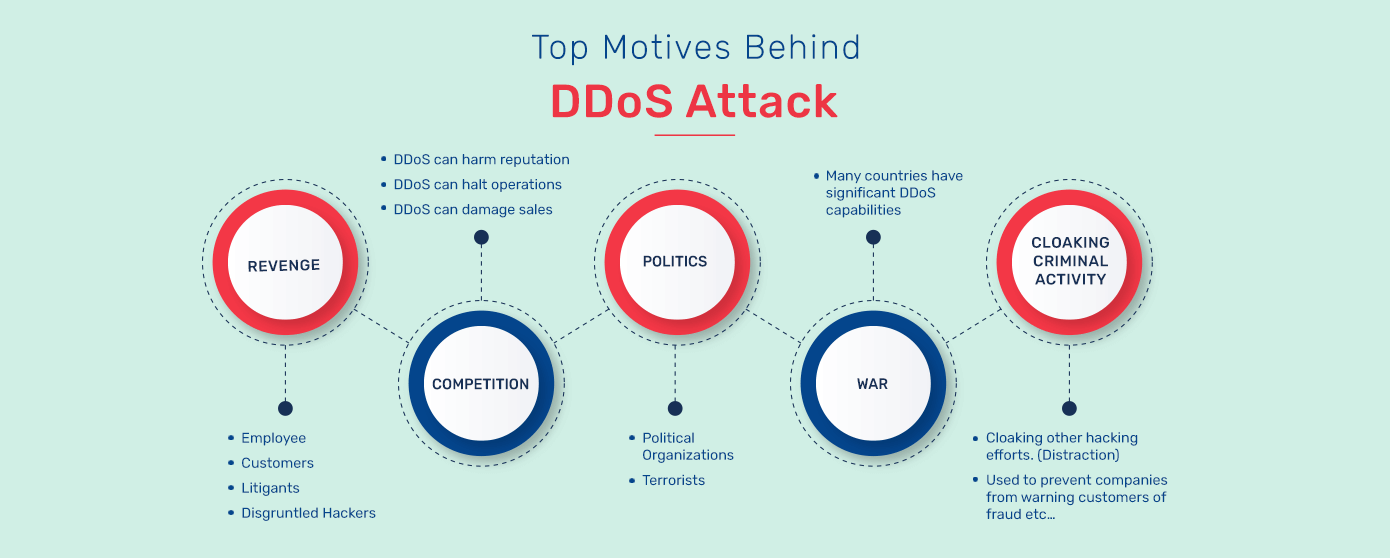
DDoS attacks are motivated by various factors, including:
Financial Gain: Attackers may launch DDoS attacks to extort money from the target. They may threaten to continue or escalate the attack unless a ransom is paid.
Ideological or Political Reasons: Hacktivist groups or individuals may carry out DDoS attacks to promote a particular agenda, express dissent, or protest against specific organizations, governments, or ideologies.
Competitive Advantage: Competitors or malicious entities may launch DDoS attacks against rival businesses to disrupt their operations, gain a competitive edge, or sabotage their online presence.
Revenge or Personal Vendetta: Individuals with grudges against a particular organization, individual, or community may launch DDoS attacks as an act of retaliation or to cause harm.
Distraction or Cover: DDoS attacks can be used as a diversionary tactic to divert the attention of security teams or overwhelm security infrastructure. In contrast, other attacks, such as data breaches or malware infections, are carried out.
Demonstrating Technical Ability: Some attackers launch DDoS attacks to showcase their hacking skills, gain notoriety within the hacker community, or simply for the thrill of causing disruption.
Disrupting Critical Infrastructure: DDoS attacks can target critical infrastructure, such as financial institutions, government websites, or public utilities, to cause widespread disruption, instill fear, or undermine trust in these systems.
Testing Security Defenses: DDoS attacks can test the resilience and effectiveness of an organization’s security infrastructure and identify potential vulnerabilities that could be exploited in more targeted attacks.
How are DDoS Attacks Categorized?
DDoS (Distributed Denial of Service) attacks are categorized based on several factors, such as the type of traffic used, the method of attack, the attack’s duration, and the attack’s target. Here are some common categories:
Volumetric Attacks
Targeted websites are flooded with voluminous malicious requests using amplification and other techniques to create massive traffic and deplete the bandwidth and other resources.
Examples – UDP Flooding, NTP Amplification, ICMP Flooding, and DNS Amplification.
Protocol Attacks
The vulnerabilities and weaknesses in Layers 3 & 4 of the protocol stack are leveraged in these state-exhaustion attacks to deplete the server resources or other network hardware/ intermediate communication equipment (firewalls, load balancers, etc.) in the middle.
Examples – SYN floods, Ping of Death, Smurf Attacks, and fragmented packet attacks.
Application-Layer Attacks
The vulnerabilities, security misconfigurations, and business logic flaws in the targeted websites are leveraged in orchestrating these Layer-7 attacks. These are cheaper for the attacker to execute as there is a smaller resource/ device requirement.
Examples – Slowloris, HTTP Floods, and/ or targeting a specific vulnerability in the application with the intent of bringing it down.
Types of DDoS Attacks
There are many sub-types of DDoS attacks that fit into the above-mentioned categories, each with distinct characteristics. Here’s a breakdown of types of DDoS attacks:
1. SYN Flood
A SYN Flood is a DDoS attack targeting the TCP (Transmission Control Protocol) handshake process. The attacker sends many TCP SYN packets to the target server but needs to complete the three-way handshake process. This causes the server to allocate resources for each incoming connection attempt but never frees them up, ultimately causing the server to become unresponsive.
2. LAND attack
A LAND attack is a type of DDoS attack that exploits a vulnerability in the TCP/IP protocol stack. The attacker sends a spoofed TCP SYN packet where both the source and destination IP addresses are set to the target server’s IP address.
Additionally, random source and destination port numbers are used. This causes the target server to send a SYN-ACK packet back to itself, creating a loop that can render the server unresponsive.
3. ACK & PUSH ACK Flood
An ACK & PUSH ACK Flood is a DDoS attack targeting the TCP protocol by sending many TCP ACK or TCP PUSH packets to the target server. This can cause the server to become overwhelmed and unresponsive.
Also take a look at the ACK Flood DDoS attacks.
4. Fragmented ACK Flood
A Fragmented ACK Flood attack is a type of Distributed Denial of Service (DDoS) attack that targets the network and transport layers of the Internet Protocol (IP) suite. This attack exploits the way TCP/IP handles fragmented packets, specifically the acknowledgment (ACK) packets, to overwhelm and disrupt the target’s network infrastructure.
5. Spoofed Session Flood
A Spoofed Session Flood, also known as a Fake Session Attack, overwhelms a target system by creating a large number of fake sessions using spoofed IP addresses. These spoofed requests appear to be from legitimate sources, causing the server to allocate resources to handle the influx of new session initiations. As the server tries to manage the flood of fake sessions, its resources, such as memory and CPU, become exhausted, leading to performance degradation or complete inaccessibility for legitimate users.
6. UDP Flood
A UDP Flood overwhelms a target system with a large volume of User Datagram Protocol (UDP) packets. This attack exploits the connectionless nature of UDP, which does not require a handshake process like TCP, making it easier to flood the target with unsolicited traffic.
7. DNS Flood
A DNS Flood attack targets Domain Name System (DNS) servers by overwhelming them with a high volume of DNS requests. Attackers send a massive number of requests to the DNS servers, often with spoofed IP addresses, causing the servers to become overwhelmed and unable to respond to legitimate queries. This results in disrupted services and inaccessibility of websites that rely on the targeted DNS servers for name resolution, leading to potential downtime and loss of business for affected websites.
8. VoIP Flood
A VoIP Flood DDoS attack targets Voice over Internet Protocol (VoIP) systems by overwhelming them with a large volume of SIP (Session Initiation Protocol) or RTP (Real-time Transport Protocol) packets. Excessive traffic disrupts normal call processing and depletes the system’s resources, causing significant degradation in call quality, dropped calls, or complete service unavailability.
9. CHARGEN Flood
A CHARGEN Flood exploits the Character Generator Protocol (CHARGEN), which is typically used for testing and debugging purpose. Attackers send spoofed requests to a server running CHARGEN, which then responds by generating a stream of characters based on the received request.
Attackers take advantage of CHARGEN responses being larger than the initial requests to increase the traffic volume aimed at the target server.
10. SSDP Flood
In SSDP Flood, attackers exploit SSDP’s multicast capabilities by sending a high volume of spoofed SSDP packets to numerous devices on a network. This flood of packets overwhelms the devices’ resources, causing network congestion and potentially leading to service degradation or unavailability.
11. SNMP Flood (SNMP Amplification)
An SNMP Flood DDoS attack overwhelms devices that run the Simple Network Management Protocol (SNMP) by flooding them with a barrage of SNMP requests. Attackers exploit SNMP’s management capabilities to send a high volume of requests, exhausting the target device’s processing capacity and network bandwidth.
12. HTTP Flood
An HTTP Flood DDoS attack overwhelms a web server with a huge number of requests. Attackers use botnets to send so many requests that the server can’t handle them all, causing the website to slow down or crash. This disrupts normal access for users and can lead to financial losses and damage to the website’s reputation. Defending against HTTP Floods involves using tools like firewalls and specialized services to filter out malicious traffic and keep the website accessible.
13. Recursive HTTP GET Flood
A Recursive HTTP GET Flood DDoS attack involves sending an overwhelming number of HTTP GET requests to a web server. Unlike a typical HTTP Flood where requests are straightforward, in a recursive attack, each request is crafted to trigger the server to generate subsequent requests to itself or to another server in a loop. This recursive behavior exponentially increases the load on the server, quickly consuming its resources such as bandwidth, CPU, and memory.
14. ICMP Flood
An ICMP Flood DDoS attack overwhelms a network or device with a large number of ping requests. Attackers send so many requests that the target’s bandwidth and processing power get maxed out, causing slowdowns or making services unavailable. Defenses involve setting limits on how many ping requests can be processed and filtering out excessive traffic to keep networks running smoothly.
15. Smurf Attack
A Smurf DDoS Attack targets networks by exploiting the ICMP protocol’s broadcast feature. The attacker sends a large amount of ICMP packets with a spoofed source IP address to a network’s broadcast address, causing all devices on the network to respond to the request and flood the victim’s network with traffic.
16. Fraggle Attack
A Fraggle attack is a type of DDoS attack that uses UDP packets to flood the victim’s network with traffic. It is similar to a Smurf attack, but instead of using ICMP packets, it uses UDP packets to amplify the attack. The attacker sends a request to a vulnerable UDP service, such as the charge service, and the response is amplified and sent to the victim’s IP address. This causes the victim’s network to become overloaded and unresponsive.
17. Ping of Death Attack
A Ping of Death sends an oversized ICMP packet to the victim’s network or web server. The packet size is larger than the maximum allowable size of an ICMP packet, causing the victim’s system to crash or become unresponsive. This attack has existed for decades but is still effective against vulnerable systems.
18. Slowloris
A Slowloris attack is a type of DDoS attack that targets web servers by opening multiple connections and keeping them open for as long as possible. The attacker sends partial HTTP requests to the victim’s web server but never completes them, keeping the connections open. This exhausts the server’s resources and makes it unable to respond to legitimate requests.
19. ReDoS
A ReDoS attack, or Regular Expression Denial of Service, is a type of DDoS attack that targets vulnerable applications that use regular expressions to parse user input. The attacker sends malicious input to the application that triggers a regular expression with exponential matching possibilities, causing the application to enter an infinite loop and consume all available resources.
Why are DDoS Attacks Dangerous?
- DDoS attacks are on the rise. There is a 76% increase in DDoS attacks. 875M vs 498M (Q1, 2024 vs Q1, 2023) – State of Application Security Q1, 2024
- One in two attacks successfully disrupted the services of the targeted platform.
- DDoS attacks are not used to breach the security perimeter of a website directly; they are often the smokescreen used to orchestrate other types of attacks/ malicious activities.
- DDoS attacks are not always volumetric; Layer-7 attacks, for instance, are smaller (1GB or less in magnitude), sneakier, and more silent.
- Multiple attack vectors are used by targeting a combination of network layers today to orchestrate DDoS.
- The financial costs attached to post-incidence response and recovery are high. The reputational losses from DDoS attacks are high owing to the high noticeability factor. The cost (financial and reputational) of a DDoS attack is estimated to be USD 120,000 for small businesses and USD 2+ million for large companies.
How to Protect Against DDoS Attacks?
DDoS attacks can be simple, from one source, or complex, using multiple methods to overwhelm a target. Multi-vector DDoS attacks use multiple pathways to overwhelm targets, making defense more challenging. For example, combining a DNS amplification attack (affecting layers 3/4) with an HTTP flood (layer 7) demonstrates their complexity.
To defend against these attacks, start with a robust network infrastructure capable of handling heavy traffic. Implement basic defenses such as traffic filters to block malicious packets and rate limiting, which can help initially.
However, static rate limiting has limitations as it may not adjust quickly enough to new attack patterns or unexpected traffic surges, potentially allowing some attacks to bypass defenses.
DDoS mitigation software like AppTrana WAAP utilizes AI and ML algorithms to analyze vast amounts of traffic data in real-time. By continuously learning from patterns and anomalies, they can effectively detect and mitigate DDoS attacks faster and more accurately than traditional methods.
These solutions dynamically adjust their defense strategies based on evolving attack techniques, automatically adapting rate limits and traffic filtering rules based on traffic behavior to counter sophisticated attacks.
Explore our detailed best practices guide for protecting against DDoS attacks
Achieve optimal security and uninterrupted service with AppTrana WAAP’s unmetered DDoS protection solution, boasting exceptional 99.99% uptime and robust protection against layer 3-7 DDoS attacks.


