While the notorious Meris DDoS botnet made headlines in 2021 with its record-breaking attacks, the emergence of newer threats in 2023 shows that cybercriminal tactics keep evolving.
The cyber threat landscape constantly evolves, whether exploiting Zyxel’s CVE-2023-28771 or targeting MySQL servers like Ddostf and Mirai’s IZ1H9 variant.
Making things even more complicated, in September 2023, researchers spotted new DDoS botnets linked to the Mirai source code. Three of these, hailBot, kiraiBot, and catDDoS, have become prominent, showing increased activity, and spreading faster.
If you’re unfamiliar with DDoS botnets or how to stop them, keep reading to learn more.
What is a DDoS Botnet?
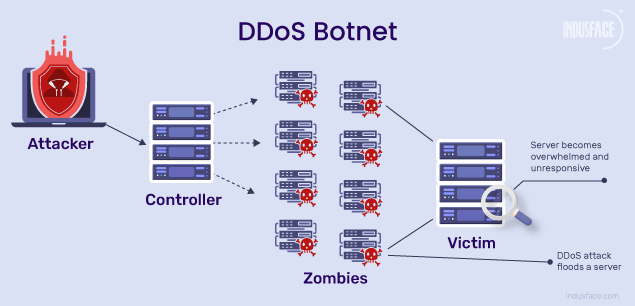
A DDoS botnet is a network of hacked computers used to flood websites or servers with excessive traffic, causing them to crash and become inaccessible.
DDoS botnet malware is not always visible or has a direct/ immediate impact on the device. In some cases, the malware immediately hijacks or takes over the device, while in other cases it runs in the background, silently executing the attacker’s instructions.
DDoS Attacks Led by Botnets
DDoS (Distributed Denial-of-Service) Attacks are cyber-attacks wherein the threat actor seeks to make websites/ web applications/ networks/ infrastructure unavailable to legitimate users by saturating the services and causing downtimes/ crashes. DDoS attacks are of two kinds –
- Application-layer attacks, measured in Requests Per Second (RPS), where seemingly legitimate requests overwhelm the target.
- Network-layer attacks, measured in Gbps (Gigabytes per second) or PPS (Packets Per Second), wherein the target’s upward bandwidth is eroded until the network saturates.
DDoS attacks can be orchestrated either by individuals engaging in coordinated activities or through botnets. The latter is known as a botnet DDoS attack.
Explore the case study on mitigating low-rate HTTP DDoS attacks driven by botnets using AppTrana WAAP
How Do Botnet DDoS Attacks Work?
- The person controlling the DDoS botnet is known as the bot herder or botmaster.
- The botmaster leverages intermediate machines known as the C&C servers to remotely control the bots.
- They use everything from HTTP websites, IRC protocols, and popular services like Reddit, Twitter, and Facebook to communicate with the C&C servers.
- Botnet servers can communicate with other botnet servers to create a Peer-to-Peer botnet.
- This P2P network could be controlled by one or multiple botmasters. So, botnet DDoS attacks could originate from/ be controlled by several people.
- Sophisticated Botnet DDoS tools and Botnet Services are readily available in the market for hire for as low as USD 5. It becomes easy and cheap to orchestrate DDoS attacks for vandalism, competitive gains, extortion, or any other malicious purpose.
Known DDoS Botnets
- Mirai: A self-propagating botnet malware that takes over poorly protected internet-connected devices. It is capable of infecting tens of thousands of devices and coordinating them to overwhelm a chosen target. The Meris DDoS botnet is an augmented and refined version of Mirai.
- Meris DDoS Botnet: The Meris botnet, composed of nearly 250,000 malware-infected networking devices, has been responsible for some of the largest DDoS attacks, including a significant assault on the Krebs on Security site. Unlike IoT-based botnets like Mirai, Meris leverages high-powered professional networking equipment, enabling it to launch record-breaking volumetric DDoS attacks measured in requests-per-second (RPS) rather than gigabits-per-second (Gbps). This increased processing power and high-speed Ethernet capability make Meris particularly dangerous. To protect against Meris, organizations must use advanced DDoS mitigation solutions.
- Nitol / IMDDOS / Avzhan / ChinaZ: This evolving and widely used DDoS botnet malware connects through a TCP socket to the Command and Control (C&C) server upon installation to send performance information from the infected device.
- Cyclone: Created in the US, this IRC-based DDoS malware kills other bots present in the infected host apart from stealing FTP credentials. It is used to orchestrate HTTP floods, Slowloris attacks, and Apache Memory Exhaustion (ARME) attacks.
- Mr. Black: Also referred to as Trojan.Linux.Spike. The Mr. Black mainly targets Linux platforms. It sends system information to the remote C&C server and executes the control commands received to orchestrate different types of botnet DDoS attacks on the target.
- Cutwail/ Pushdo: Though typically used for email spamming, this botnet was altered in 2010 to orchestrate DDoS attacks against major websites like PayPal, Twitter, CIA, FBI, and 300+ others. It pushes Trojan components onto the targeted devices to run the Windows OS.
-
Examining DDoS Botnet Exploits in 2023
Zyxel Vulnerability (CVE-2023-28771): Targeted Exploitation by DDoS Botnets
In June 2023, a surge in DDoS botnet activities was observed, capitalizing on the Zyxel vulnerability (CVE-2023-28771). This critical flaw, rated at 9.8 on the CVSS scoring system, serves as a gateway for DDoS attacks, with unauthorized attackers potentially executing arbitrary code through a command injection vulnerability in multiple firewall models.
Ddostf Malware: Botnet DDoS attack Directed at MySQL Servers
The ‘Ddostf’ malware botnet has pivoted its focus towards MySQL servers, transforming them into DDoS platforms for cybercriminals. Exploiting vulnerabilities in unpatched MySQL environments, the botnet utilizes brute-force techniques and user-defined functions (UDFs) to execute malicious commands. This strategic move allows the Ddostf botnet to establish persistence on Windows systems, evading takedowns by connecting to new command and control (C2) addresses.
Mirai-based DDoS Botnet: Router Exploits
Through its IZ1H9 variant, the Mirai botnet has extended its reach by integrating 13 new exploit payloads, specifically targeting routers, IP cameras, and more. This expansion of functionalities amplifies the DDoS threat, exploiting vulnerabilities in devices from major manufacturers. The timeline spans 2015 to 2023, encompassing various vulnerabilities and focusing on command execution flaws, illustrating the persistence of recent DDoS botnet attacks.
Docker Engine APIs Facing Persistent DDoS Botnet Threats
A new threat, OracleIV, has emerged, targeting publicly accessible Docker Engine API instances with a unique approach. Researchers from Cado unveiled a campaign exploiting misconfigurations, effectively turning machines into a distributed denial-of-service (DDoS) botnet. Leveraging an HTTP POST request to Docker’s API, attackers fetch a malicious image, ‘oracleiv_latest,’ disguising itself as a MySQL container. Despite including a miner, the container reveals a concise shell script (oracle.sh) designed for conducting DDoS attacks.
Condi DDoS Botnet: Exploiting TP-Link’s Vulnerability (CVE-2023-1389)
FortiGuard Labs has identified recent samples of the Condi DDoS-as-a-service botnet, exploiting the vulnerability (CVE-2023-1389) in TP-Link Archer AX21 (AX1800) routers. This discovery highlights an active attempt to spread, emphasizing the persistent risk associated with unpatched systems in the face of recent DDoS botnet attacks.
Take a closer look at 10 best practices for botnet detection and removal.
Botnet DDoS Attack Prevention and Protection with AppTrana WAAP
Like any cyber-attack, botnet DDoS attacks are costly and must be prevented proactively. With the help of intelligent and comprehensive cloud-based DDoS protection solutions from AppTrana WAAP you can effectively prevent DDoS botnet attacks without having to install any hardware or software.
This fully managed solution is capable of nuanced intrusion detection, traffic monitoring and filtering, and instant bot blocking based on global threat intelligence, real-time insights, and security analytics.
Being a managed security solution AppTrana WAAP ensures that the solution is highly tailored to the unique needs of the organization. Its WAF rules are built with surgical accuracy to prevent a wide range of DDoS botnets and other attacks by default.
With AppTrana DDoS protection, you can be rest assured that your website/ application/ service is always available to your legitimate users.


 AppTrana WAAP Platform
AppTrana WAAP Platform

