What is Smurf Attack?
A Smurf attack is a type of DDoS attack that leverages ICMP echo requests (ping packets) to flood a victim’s network or server with traffic.
The code was originally written by hacker Dan Moschuk (TFreak). The first Smurf attack (or one of the first) occurred in 1998 with the University of Minnesota as the target. It resulted in data loss, network slowdown, and computers across the state shutting down.
Other notorious protocol attacks include SYN flood, Ping Flood, and Fraggle Attack.
How Does a Smurf Attack Work?
The attack works by exploiting the ability of ICMP to send an echo request to a network’s broadcast address, causing all hosts on that network to respond simultaneously to the spoofed source address – the victim’s IP address.
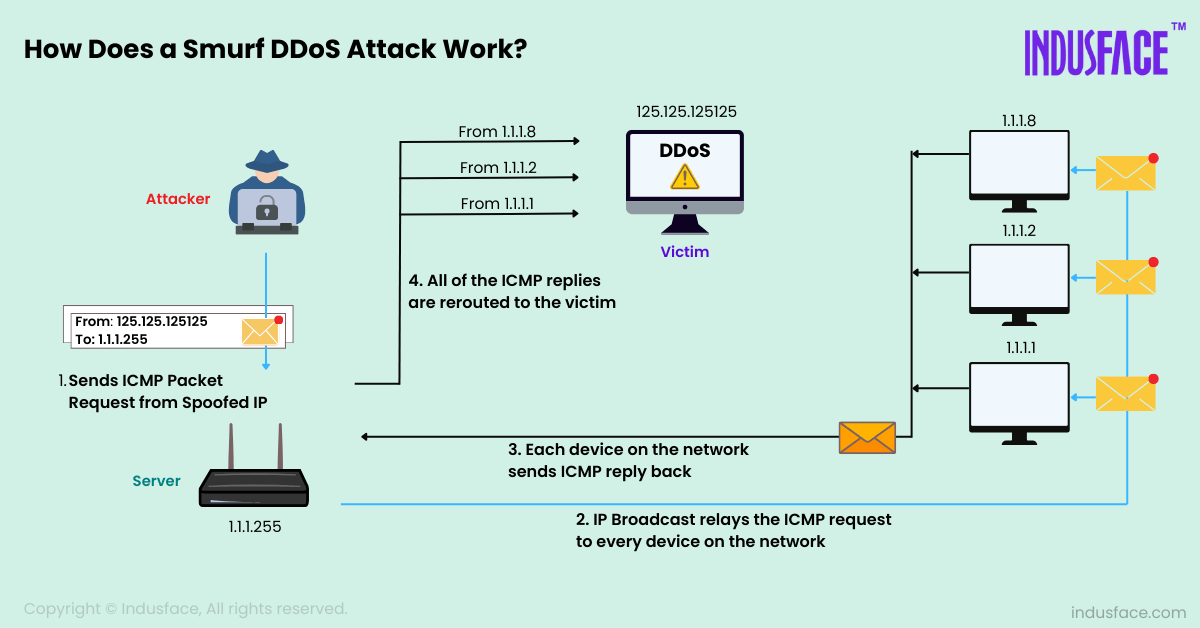
This results in a flood of responses overwhelming the victim’s network capacity and causing it to become unreachable to legitimate users. In this regard, smurf attacks are similar to ping floods.
Unlike Smurf attacks, ICMP ping floods directly flood a target with ICMP echo requests (pings) without relying on the amplification effect from multiple sources.
Smurf attacks are typically considered more severe in impact because they leverage amplification from multiple sources on the network, leading to a significant volume of traffic overwhelming the victim’s network resources.
What Types of Smurf Attacks Are There?
There are two types of smurf attacks:
Basic Smurf Attack – A basic Smurf attack utilizes infinite ICMP request packets to overload networks. Since every device on the network receives the request to issue a reply, traffic surges rapidly, taking down the system in the process.
Advance Smurf Attack – An advanced Smurf attack begins just as a basic attack would. Echo requests, however, can be configured to target additional third-party victims. Hackers utilize this technique to target larger networks and/or larger sections of the web.
How to Prevent Smurf Attacks?
Implement these essential strategies to prevent and mitigate Smurf attacks in your network infrastructure:
Disable ICMP Echo Responses
Configure routers and network devices to disable ICMP echo responses to broadcast addresses. This prevents devices from responding to ICMP requests directed at the broadcast address, mitigating the amplification effect.
Implement Ingress Filtering
Implement ingress filtering at network borders to discard packets with spoofed or invalid IP addresses. This prevents attackers from using the victim’s IP address as the source address in ICMP packets.
Apply Rate Limiting
Implement rate-limiting policies on routers and firewalls to control the rate of ICMP requests sent or received. This strategy helps reduce the impact of ICMP flood attacks by restricting the amount of traffic directed toward the victim.
Segment Network Traffic
Segment network traffic and isolate critical infrastructure from less critical systems. This helps restrict the spread of ICMP flood traffic across the network, thereby minimizing the impact of a Smurf attack.
Enable Source Address Validation
Enable Strict Unicast Reverse Path Forwarding (uRPF) or similar techniques to verify the legitimacy of source IP addresses on incoming packets. This helps prevent attackers from spoofing IP addresses and launching Smurf attacks.
Deploy DDoS Protection Tools
Utilize dedicated DDoS mitigation tools that specialize in detecting and mitigating ICMP-based attacks. Such tools can detect unusual traffic patterns signaling a Smurf attack and promptly apply mitigation measures.
Monitor Network Traffic
Implement continuous monitoring of network traffic and performance metrics to detect sudden increases in ICMP traffic volume. Anomaly detection tools can help identify and mitigate potential Smurf attacks promptly.
Update and Patch Network Devices
Ensure that all routers, switches, and network devices are updated with the latest security patches and firmware updates. This helps mitigate vulnerabilities that attackers could exploit to launch Smurf attacks.
Educate and Train Personnel
Educate network administrators and IT staff about the risks and characteristics of Smurf attacks. Training should include incident response procedures and protocols for quickly identifying and mitigating DDoS attacks.


 AppTrana WAAP Platform
AppTrana WAAP Platform

