Buffer overflow attack, a critical concern in cybersecurity, occurs when a program exceeds its memory buffer’s capacity, resulting in potential data corruption or program crashes.
Hackers know this and can manipulate buffers to execute device takeovers and compromise security.
Notorious hacking incidents like WhatsApp VoIP (2019), Stagefright (2015), and Morris Worm (1998) stand as examples of the devastating consequences caused by buffer overflow attacks.
What is a Buffer Overflow?
A buffer is a sequential section/ area of memory storage where data is temporarily stored while in transition/movement from one location to another. They usually live temporarily in the RAM and are used to improve the performance and speed of data access.
For instance, online streaming services often use them to avoid interruptions in the service. The player streams from the buffer where x% of the video is downloaded and stored at a time.
Buffers are designed to store only a specified amount of data at a time. Unless it has built-in instructions to discard data automatically when it is too full, it will bleed into and overwrite in the adjacent memory locations. This anomaly is a buffer overflow/ buffer overrun.
Root Causes of Buffer Overflows
Buffer overflows occur due to programming errors and inadequate input validation in software. Here are some common reasons why buffer overflows can happen:
Insufficient input validation
When a program fails to validate the size and integrity of incoming data, it becomes vulnerable to buffer overflow attacks. If the program does not check the input boundaries, it may accept more data than the buffer can hold.
Poor memory management
Improper handling of memory allocation and deallocation can lead to buffer overflows. For example, if a program dynamically allocates memory but fails to release it properly, it can cause buffers to overflow.
Insecure coding practices
Programming mistakes, such as using unsafe functions or not properly terminating strings, can introduce buffer overflow vulnerabilities. Ignoring secure coding guidelines and failing to follow best practices can contribute to buffer overflow issues. Here is a detailed blog on how security misconfiguration harms your business.
Legacy code and outdated software
Older software systems may not have incorporated robust security measures against buffer overflows. Outdated libraries or components may contain vulnerabilities that attackers can exploit.
Complex software architecture
Large and complex software applications with numerous interconnected components can increase the likelihood of buffer overflow vulnerabilities. Ensuring proper input validation and memory management in such complex systems can be challenging.
How do Attackers Orchestrate Buffer Overflow Attacks?
Attackers attempt to identify the program’s memory layout to find memory areas that hold executable code. By leveraging the buffer overflow vulnerabilities present in the application/ software, they deliberately flood the buffer and overwrite adjacent areas of memory, especially those containing executable code.
Through their carefully crafted inputs, they replace the executable code with malicious code to modify how the application works and fulfill its objectives.
Attackers orchestrate buffer overflow attacks by taking advantage of programming vulnerabilities to manipulate the behaviour of a program. Here’s an example that illustrates how a buffer overflow attack can be executed:
Consider the following vulnerable code snippet written in the C programming language:
#include <stdio.h>
void vulnerableFunction(char* input) {
char buffer[8];
strcpy(buffer, input);
printf("Buffer: %s\n", buffer);
}
int main() {
char maliciousInput[20] = "MaliciousInput";
vulnerableFunction(maliciousInput);
return 0;
}
In this example, we have a function called vulnerableFunction () that accepts a character array (input) as an argument and copies its content into a fixed-size buffer (buffer) of size 8.
The vulnerability lies in the lack of bounds checking. If an attacker provides input that exceeds the buffer’s size, a buffer overflow occurs. The attacker can overwrite adjacent memory areas, potentially modifying program variables or injecting malicious code.
An attacker could provide an input larger than the buffer size to exploit this vulnerability. For instance, they might input a string of length 20, as shown in the maliciousInput array in the main () function. When vulnerableFunction () is called with this input, it exceeds the buffer’s capacity, resulting in a buffer overflow.
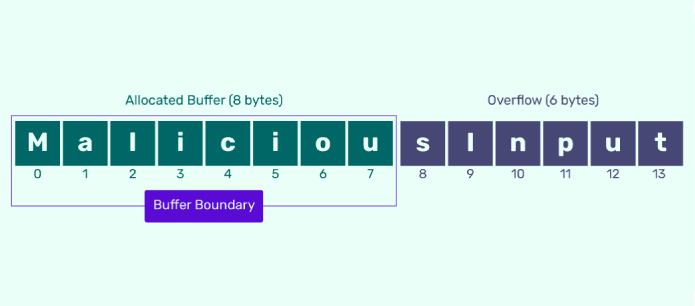
The consequences of this attack can vary depending on the attacker’s intent. They could overwrite program variables, modify the control flow, inject shellcode, or even gain unauthorized access to the system.
Different Types of Buffer Overflow Attacks
Stack-based buffer overflow
This is the most common type of buffer overflow attack. It occurs when a program writes more data to a buffer on the stack than it can hold. By overwriting adjacent memory areas, attackers can modify return addresses, inject malicious code, or gain control of the program’s execution flow.
Heap-based buffer overflow
In contrast to stack-based buffer overflows, heap-based attacks target dynamically allocated memory on the heap. Attackers exploit vulnerabilities in memory allocation and deallocation processes, such as double-free or use-after-free, to overwrite heap metadata or execute arbitrary code.
Format string attacks
Format string vulnerabilities occur when a program uses user-supplied format strings without proper validation. Attackers can leverage this weakness to read sensitive data from memory, modify variables, or execute arbitrary code.
Integer overflow
In an integer overflow attack, an attacker exploits the limited range of integer data types to cause unexpected behaviour or buffer overflows. By providing input that exceeds the maximum representable value, attackers can manipulate calculations and cause buffer overflows.
In what ways can buffer overflows pose a significant threat?
Buffer overflow attacks pose significant threats to the security and integrity of software systems. Here are some key threats associated with buffer overflow attacks:
Code execution
One of the primary threats of buffer overflow attacks is the ability of attackers to execute arbitrary code on a compromised system. By injecting malicious code into the program’s memory, they can gain control over the program’s execution flow, allowing them to run unauthorized commands, install malware, or perform other malicious actions.
Privilege escalation
Buffer overflow vulnerabilities can be exploited to elevate privileges within a system. By manipulating the stack or overwriting critical variables, attackers can bypass access controls and gain higher privileges than originally intended. This enables them to access sensitive resources, modify system configurations, or perform actions reserved for privileged users.
Remote code execution
In some cases, buffer overflow attacks can be conducted remotely without direct access to the targeted system. By exploiting a vulnerability in a network service or an application accessible over the internet, attackers can remotely trigger a buffer overflow and execute arbitrary code on the targeted system. This can lead to a complete compromise of the system and potentially allow attackers to pivot to other systems on the network. Learn more about remote code execution.
Denial of Service (DoS)
Buffer overflow attacks can also launch Denial of Service attacks. By causing a program to crash or consuming excessive system resources, attackers can render a system or service unavailable to legitimate users. This can disrupt business operations, causing financial losses and reputational damage.
Information disclosure
Buffer overflow vulnerabilities can lead to the exposure of sensitive information stored in memory. Attackers can overwrite variables or data structures, potentially disclosing confidential data such as passwords, encryption keys, or personal information. This information can be exploited for identity theft, fraud, or further attacks on the affected individuals or organizations.
How to Detect Buffer Overflow Vulnerabilities?
Vulnerability assessment and software testing methodologies effectively identify buffer overflow errors within functions and other sections of the source code. Two primary approaches can be utilized in software testing: static testing and dynamic testing.
Static testing involves activities such as code reviews, proofreading, or inspections. However, manually scrutinizing numerous lines of code for potential buffer overflow errors can be daunting and time-consuming. Moreover, there is always the risk of overlooking critical errors due to human oversight.
The process of executing code using a predefined set of test cases, whether performed manually or through automation, is known as dynamic testing. Dynamic application testing tools, such as Indusface WAS, automate the execution of the target program and verify if its runtime behaviour meets the expected security criteria.
DAST tools play a vital role in detecting buffer overflow vulnerabilities throughout development. They can also ensure the desired code quality and adherence to quality assurance standards.
How To Prevent and Mitigate Buffer Overflow Attacks?
Secure Coding Practices
Follow secure coding guidelines and best practices to minimize the risk of buffer overflow vulnerabilities:
- Choose languages with built-in protection mechanisms such as C#, Java, JavaScript, PERL, etc.
- If using C/ C++ languages, standard library functions that do not have bounds-checks should be avoided.
- Use special security procedures in the code to minimize the likelihood of buffer overflow vulnerabilities.
- Review all custom codes and codes that accept user inputs via HTTP requests used in the application.
- Ensure that all input sizes and bounds are checked.
- Proactively identify and fix coding errors.
Runtime Protection
Modern Operating Systems offer several runtime protections that help prevent buffer overflow attacks.
- Structured Exception Handler Overwrite Protection (SEHOP): The Structured Exception Handler (SEH), a built-in system, helps handle software and hardware exceptions. SEHOP enables businesses to prevent attackers from overwriting and attacking the SEH.
- Address Space Randomization (ASLR): ASLR randomly moves around the address spaces of data locations. It is nearly impossible to execute buffer overflow attacks without knowing where the executable code exists.
Data Execution Prevention
By marking certain memory regions as executable and non-executable, attackers are prevented from executing malicious code in non-executable areas.
Input Validation
Implement robust mechanisms to validate and sanitize user input. This helps prevent malicious input from causing buffer overflow conditions. Validate input length, range, and format, and reject any input that exceeds defined limits.
Use Safe Programming Languages
Choose languages that provide built-in memory management and automatic bounds checking, such as Java or C#. These languages help prevent common buffer overflow vulnerabilities by handling memory allocation and deallocation automatically.
Regular Security Updates
Keep all software and libraries up to date with the latest security patches. Many buffer overflow vulnerabilities are discovered and patched over time, so ensuring that your systems are running the most secure versions is crucial.
Penetration Testing and Vulnerability Scanning
Conduct regular penetration testing and scanning to identify and address any existing buffer overflow vulnerabilities. These assessments help uncover potential weaknesses and allow for proactive remediation.
User Privilege Separation
Implement strong access controls and enforce the principle of least privilege. Separating user privileges and limiting access to critical resources reduces the potential impact of buffer overflow attacks.
Security Awareness and Training
Educate developers and users about the risks of buffer overflow attacks and the importance of secure coding practices. Provide training on identifying and mitigating vulnerabilities to promote a security-conscious culture.
How Indusface Can Help
Indusface offers a comprehensive set of solutions designed to assist businesses in mitigating and preventing buffer overflow attacks. Among these solutions, the AppTrana WAF safeguards crucial business applications by intercepting and blocking malicious requests that have the potential to trigger a buffer overflow condition, effectively preventing their access to your applications.
Additionally, it enhances the security of organizations’ attack surface as it evolves with the introduction of new features, updates to existing features, and the exposure of fresh web application programming interfaces (APIs).


 AppTrana WAAP Platform
AppTrana WAAP Platform

