With the rise of online activity, secure connections are no longer optional but essential.
Despite using the HTTPS protocol, cybercriminals can still find ways to intercept traffic and issue fake SSL certificates.
The 2011 cyberattack on the Dutch CS Diginotar remains one of the most significant public Certificate Authority (CA) compromises to date. This breach highlighted that even with HTTPS protocol, cybercriminals could find ways to infiltrate systems and issue counterfeit SSL certificates.
This threat is becoming more widespread, and it’s crucial to take action to protect yourself and your data.
That’s where SSL pinning plays its role—it offers an additional layer of protection that can keep your data safe.
What is an SSL/TLS Certificate?
Secure Socket Layer (SSL) and Transport Layer Security (TLS) ensure encrypted communication over the internet – specified as HTTPS.
The security factors of SSL are based on the security certificates’ “Chain of Trust.” When a sender sends a message, the client checks the server’s SSL certificate to confirm whether Trusted CA issues the certificate.
SSL certificate combines symmetric and asymmetric cryptography to establish a secure connection between the client and server. The server uses its SSL/TLS certificate to authenticate to the client, containing the server’s public key and other identifying information. The client then generates a symmetric key to encrypt data that will be exchanged with the server.
During the SSL/TLS handshake, the client and server agree on a cipher suite for encrypted communication. This includes the encryption algorithm, the key exchange method, and the message authentication code (MAC) algorithm.
Once the handshake is complete, the client and server can exchange encrypted data.
Man-In-The-Middle Attack
Despite the security provided by SSL/TLS, it is still vulnerable to attacks, particularly man-in-the-middle (MITM) attacks. In a MITM attack, an attacker intercepts communication between a web client and a web server, allowing them to eavesdrop on the conversation or even modify the data being exchanged.
In this digital eavesdropping, cybercriminals enter as a proxy and begin communicating between two parties. None of them knows that a third person is between them, who can communicate, change, or remove communication based on their intention.
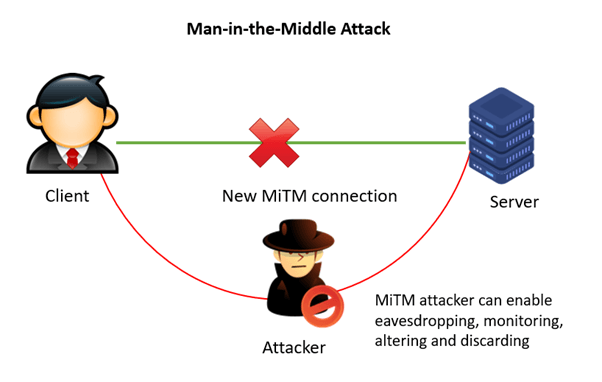
Network-based MITM attacks involve intercepting communication between a web client and a web server over an unsecured network. This can be done by sniffing network traffic or tricking the client into connecting to a fake Wi-Fi hotspot the attacker has set up.
Certificate-based MITM attacks involve the attacker obtaining a fraudulent SSL/TLS certificate from a trusted CA. Certificate mis-issuance occurs in multiple forms, such as compromising the CA’s systems or using social engineering to trick the CA into issuing the certificate.
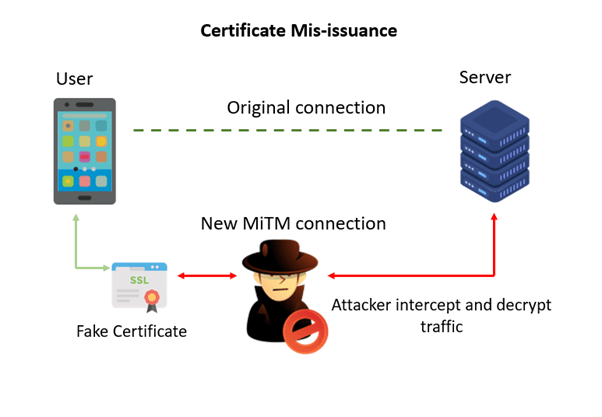
Another approach is to compromise the Certificate Authority (CA) by stealing the root key, which allows criminals to generate fraudulent certificates signed by the compromised root key.
MITM attacks can also occur when a client neglects to authenticate the certificate with trusted CAs or when the client is compromised and an illegitimate CA is inserted into the client’s trusted root authority.
In various MITM attacks, the malware redirects users to counterfeit websites where their sensitive information can be collected easily.
When you are unable to detect these threats, your apps become vulnerable to man-in-the-middle attacks. MITM attacks are dangerous since hackers can read, alter, or misuse messages between parties.
For example, if your app handles your customers’ credit card details for a purchase, the man in the middle can misuse the credit card numbers.
What is SSL Pinning?
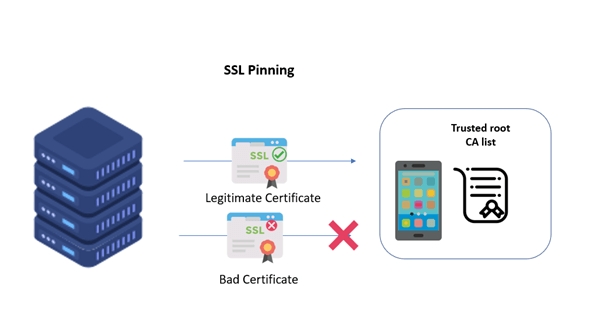
SSL pinning is a technique that helps to prevent MITM attacks by hardcoding the SSL/TLS certificate’s public key into the app or device. This means that when the app or device communicates with the server, it will compare the server’s SSL/TLS certificate’s public key with the one that is hardcoded into the app or device.
If they match, the connection is considered secure, even if a different CA signs the certificate.
Two Techniques Used in SSL Pinning
1. Certificate SSL pinning
SSL certificate pinnning technique involves hard-coding the SSL certificate of a server into the client’s application. The client then compares the server’s certificate with the hard-coded certificate and only allows communication if they match. This ensures the client only communicates with the intended server, not an imposter server with a fake certificate.
This security measure pins the identity of trustworthy certificates on apps and blocks unknown documents from suspicious servers.
With this technique, you can pin an SSL certificate host – a list of trustful certificates to your application during development and compare the server certificates against the list during runtime.
2. Public key pinning
Public key pinning involves hard-coding the public key of the server’s SSL certificate instead of the entire certificate. The client then checks that the server presents a certificate containing the same public key that was hard-coded into the client’s application. This method ensures that even if the server’s certificate changes, the client still trusts the server as long as the public key remains the same.
Both types of pinning have their own advantages and disadvantages, and their suitability depends on the specific use case.
Certificate pinning is easier to implement but may require frequent updates if the server’s certificate changes frequently. Public key pinning provides more flexibility in certificate management but requires more technical expertise to implement.
Types of SSL Pinning
1. Static SSL Pinning
In static SSL pinning, the certificate or public key is hardcoded in the application. This means the application will only trust the specific certificate or public key pre-defined in the code.
If the server’s certificate or public key changes, the application will no longer trust the server, and the user will receive an error message. Static SSL pinning provides strong security against attacks that involve fraudulent certificates or compromised CAs.
2. Dynamic SSL Pinning
In dynamic SSL pinning, the application does not hardcode the certificate or public key. Instead, it retrieves the certificate or public key from the server during the initial handshake and then caches it locally for future connections.
This means the application can detect changes to the server’s certificate or public key and take appropriate action if necessary. Dynamic SSL pinning is more flexible than static SSL pinning but requires more resources.
How Does SSL Pinning Work?
Here is a step-by-step process of how SSL pinning works:
- The client (such as a mobile app) establishes an SSL/TLS connection with the server.
- The server sends its public key, which is used to encrypt the data exchanged between the client and the server.
- The client verifies the server’s identity by checking the server’s digital certificate issued by a trusted Certificate Authority (CA).
- With SSL pinning, the client also checks that the server’s public key matches the hard-coded public key into the client’s code or configuration. If the public keys match, the connection is allowed to proceed.
- If the server’s public key does not match the pinned key, the client assumes that a MITM attack is underway and terminates the connection. This prevents any communication from being intercepted and tampered with.
- If the client needs to update the pinned public key, the app must be updated with a new pinned key.
For example:
You have a mobile banking app that uses SSL pinning. When the user opens the app, the app initiates an SSL/TLS connection with the bank’s server. The bank’s server sends its public key to the app, which verifies the digital certificate against the trusted CA.
The app also checks that the public key matches the pinned key, which is hard-coded into the app’s code or configuration.
If the public keys match, the app proceeds with the connection, allowing the user to perform banking transactions. If the public keys do not match, the app terminates the connection and displays an SSL certificate not trusted error message, indicating a potential MITM attack.
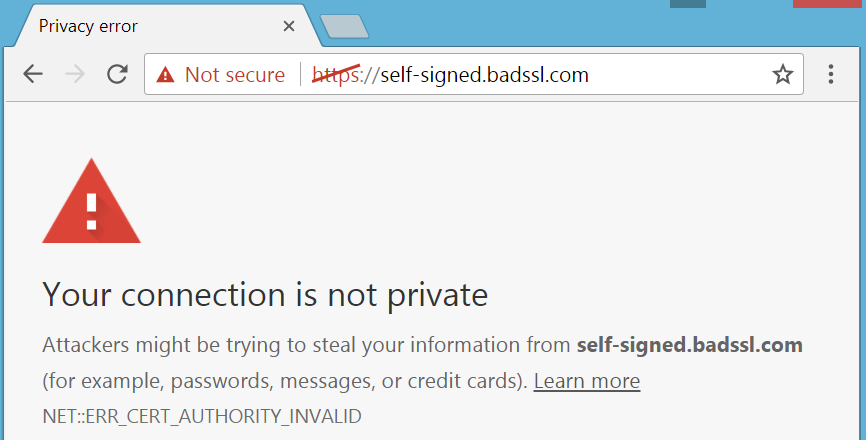
The error message indicates that the browser does not recognize the certificate authority (CA) that issued the certificate as a trusted provider or that the server self-signed the certificate.
SSL Pinning and Reverse Proxy Compatibility
Enabling SSL pinning in applications (such as mobile apps, APIs, or web apps) creates difficulties for customers when trying to introduce security solutions or in-path devices that rely on reverse proxy technology due to SSL termination.
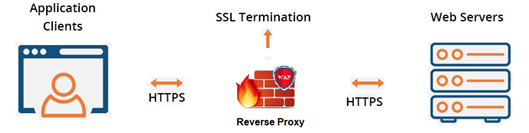
When a reverse proxy solution is implemented between the client and server, the SSL handshake occurs between the application clients and the reverse proxy. The client receives an SSL certificate installed on the reverse proxy, which can lead to the client rejecting the connection as it considers it an untrusted server connection.
Advantages of SSL Pinning
- Enhances Security: One of the most significant benefits of SSL pinning is that it enhances the security of network communications by adding an extra layer of protection against man-in-the-middle attacks. By requiring a pre-configured certificate or public key, SSL pinning ensures that the client device communicates only with the intended server and not with an imposter.
- Mitigates Certificate-Based Attacks: Certificate-based attacks, where an attacker can compromise a certificate authority (CA) or issue fake certificates, can be prevented using SSL pinning. By hard-coding the certificate or public key of the intended server, SSL pinning prevents attackers from presenting their own fake certificates and decrypting encrypted traffic.
- Improves Performance: Another advantage of SSL pinning is that it can improve the performance of applications. Since SSL pinning eliminates the need for the client device to validate the server’s SSL certificate with the trusted CAs, it can save processing time and reduce latency.
- Ensures Trust: By requiring that the client device verify the server’s identity through a trusted certificate or public key, SSL pinning ensures trust between the client and server.
Limitations of SSL Pinning
- Complicates Deployment: SSL pinning complicates deployment and maintenance, which is one of its main drawbacks. Since SSL pinning requires that the certificate or public key be hard-coded into the client application, any changes to the server’s SSL certificate or public key will require an update to the client application.
- Adds Development Overhead: Implementing SSL pinning requires additional development overhead, as developers must ensure that the client application can securely store the pinned certificate or public key.
- Limits Flexibility: By pinning an app, it becomes cumbersome to change the security certificate. You must update an Android app and send it again to Google Play for your users to reinstall it.
Conclusion
Though this process is tedious and complex, the pinning SSL certificate is worth the effort as it decreases the risk of data leaks and serves as countermeasures against MITM attacks.


