What Is Zero Trust Security?
Zero Trust is a cybersecurity framework that eliminates implicit trust and continuously verifies every user and device trying to access resources. It’s built on the principle of “never trust, always verify”, ensuring strict identity and access controls at every layer of the infrastructure.
This model assumes:
- Every access request could be a threat
- Verification must be dynamic and based on context
- Security must be enforced continuously across all endpoints, workloads, and users
The concept was popularized by Forrester and later adopted and formalized by organizations like NIST, which published the NIST SP 800-207 Zero Trust Architecture (ZTA) framework.
Key Principles of Zero Trust
Implementing Zero Trust isn’t just a technological decision — it’s a strategic mindset. The core principles include:
1. Never Trust, Always Verify
No device or user is inherently trusted. Every interaction must be verified using strong authentication and context-aware access controls.
2. Least Privilege Access
Users and systems are granted the minimum level of access needed to perform their tasks — and nothing more. This principle helps limit the blast radius of any compromise.
3. Assume Breach
Design systems with the expectation that an attacker is already inside. This drives more rigorous segmentation, monitoring, and response.
4. Micro-Segmentation
Rather than trusting broad segments of the network, Zero Trust enforces fine-grained access controls, often down to the application or workload level.
5. Continuous Monitoring and Validation
Access decisions are not a one-time event. Users and devices are continuously assessed based on behavior, posture, and environmental context.
Why Zero Trust Matters Today
Zero Trust isn’t just a trend — it’s a necessary response to the evolving security landscape. The way organizations operate has drastically changed, and traditional security models can no longer keep up. Here’s why adopting Zero Trust is more critical than ever:
1. The Perimeter Is No Longer Defined
In the past, security strategies relied on the idea of a fixed, defensible perimeter — typically protected by firewalls, intrusion prevention systems, and VPNs. Once users were inside the network, they were generally trusted to access systems and data.
But today, the perimeter has effectively disappeared.
- Cloud-first strategies mean applications and data are no longer confined to internal data centers — they’re hosted across public, private, and hybrid clouds.
- Remote workforces access resources from multiple geographies and unsecured home networks, making it impractical to assume a user inside the network is safe.
- SaaS applications such as Salesforce, Microsoft 365, and Zoom handle sensitive operations outside of IT’s direct control.
- BYOD and mobile devices expand the attack surface, as many of them are unmanaged and outside security monitoring.
- Third-party vendors and partners need access to internal applications, increasing the risk of compromise through supply chain and access abuse.
As a result, trust can no longer be granted based on network location. Zero Trust shifts the focus from where access is coming from to who is requesting it, what they’re trying to access, and whether they meet strict verification criteria at that moment.
2. Rising Insider and Lateral Threats
Most high-profile breaches don’t start with sophisticated malware — they begin with compromised credentials, phishing, or malicious insiders. Once attackers get a foothold, they move laterally within the network to find sensitive data or critical systems.
Zero Trust tackles this head-on by minimizing both insider threats and lateral movement:
- Micro-segmentation: Breaks the network into granular zones, so even if an attacker accesses one part of the network, they can’t freely move to others.
- Least privilege access: Limits user and system access to only the data and apps they truly need, closing off unnecessary pathways.
- Continuous verification: Regularly re-evaluates access based on context, such as device posture, location, or behavior anomalies.
- Behavioral analytics: Detects abnormal activities (e.g., a finance user accessing developer tools) and flags them in real-time.
These capabilities reduce the blast radius of any breach, allowing security teams to contain threats faster and minimize damage.
3. Compliance and Risk Management
Zero Trust doesn’t just enhance cybersecurity—it’s a strategic enabler for achieving regulatory compliance. By providing continuous monitoring, fine-grained access control, and full visibility, it helps organizations stay audit-ready, avoid penalties, and build customer trust.
Several compliance frameworks incorporate or support Zero Trust principles. Here’s how:
HIPAA (Health Insurance Portability and Accountability Act)
- 164.312(a)(1) – Access Control: Requires technical policies and procedures to allow access only to those with appropriate rights.
- 164.312(b) – Audit Controls: Calls for hardware, software, and procedural mechanisms to record and examine activity in information systems
PCI DSS v4.0 (Payment Card Industry Data Security Standard)
- Requirement 10: Log and monitor all access to system components and data (supports Zero Trust’s visibility and auditing).
- Requirement 8.4.2: Multi-factor authentication for all access into the CDE (critical for Zero Trust identity enforcement).
Core Components of Zero Trust Architecture
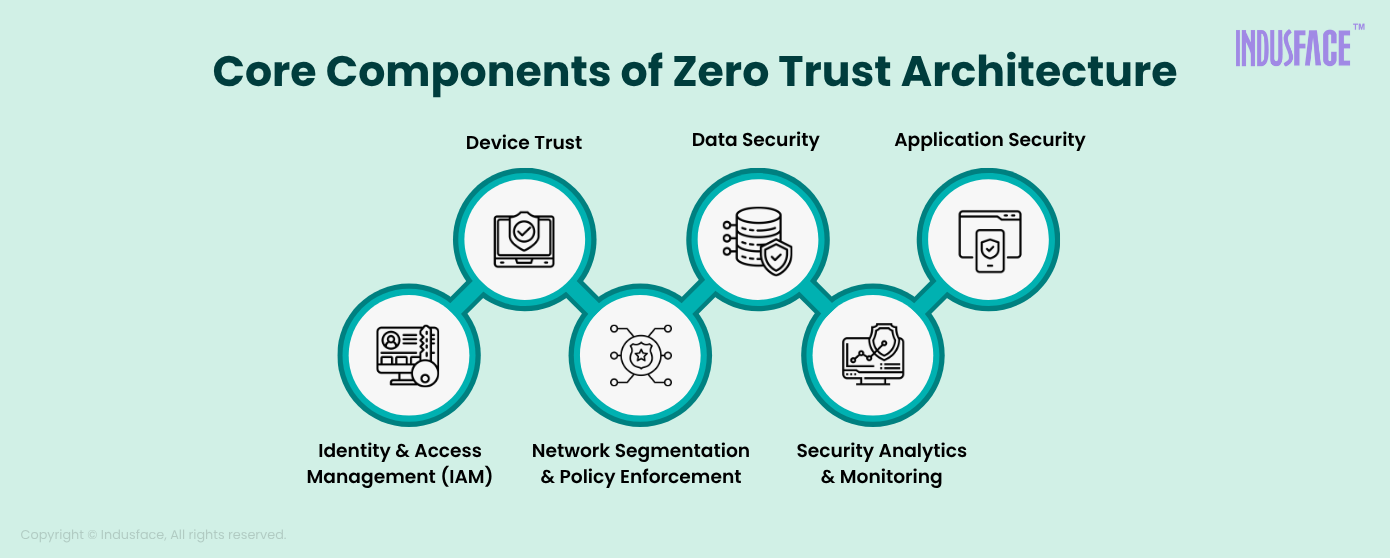
1. Identity and Access Management (IAM)
In Zero Trust, identity is the new perimeter. Before granting access to any resource, the system must validate who is requesting access, what they are trying to access, and why they need it.
Key technologies and practices include:
- Multi-Factor Authentication (MFA): Prevents credential theft by requiring users to verify their identity using multiple methods (e.g., password + OTP or biometrics).
- Single Sign-On (SSO): Streamlines user authentication across multiple systems, while centralizing session control for better visibility and policy enforcement.
- Just-In-Time (JIT) Access: Grants access for a limited time based on specific tasks, reducing standing privileges that attackers could exploit.
- Role-Based Access Control (RBAC): Users get access based strictly on their job function, adhering to the principle of least privilege.
- Identity Federation and Continuous Validation: Leverages trusted identity providers while continuously validating user behavior and session legitimacy in real time.
2. Device Trust
Not all threats come from compromised credentials—infected or non-compliant devices are major risk vectors. In Zero Trust, access is denied unless the device is verified as secure.
Core practices include:
- Device Posture Checks: Evaluate the device’s operating system, patch level, firewall status, and presence of malware before granting access.
- Endpoint Detection and Response (EDR): Continuously monitors endpoints for suspicious behavior, enabling rapid containment and remediation.
- Mobile Device Management (MDM): Enforces security policies on mobile endpoints—blocking jailbroken/rooted devices and enforcing encryption or remote wipe.
- Device Certificates and Trusted Profiles: Devices must present valid certificates to authenticate themselves before accessing enterprise resources.
3. Network Segmentation and Policy Enforcement
Traditional flat networks allow attackers to move laterally once inside. Zero Trust counters this with micro-segmentation, limiting communication between systems to only what’s necessary.
Key mechanisms:
- Software-Defined Perimeters (SDP): Hides applications from public view unless access is explicitly granted. Resources are invisible to unauthorized users.
- Dynamic Access Policies: Access decisions are made based on real-time context — user identity, device trust, location, time of day, and behavioral patterns.
- Policy Enforcement Points (PEPs): These act as gatekeepers, located at network boundaries and application entry points to enforce granular access controls.
4. Data Security
Zero Trust shifts the focus from securing networks to securing data itself — regardless of where it lives or travels.
Key technologies:
- Data Loss Prevention (DLP): Monitors and controls the movement of sensitive data to prevent accidental or malicious leakage.
- Encryption (at rest and in transit): Ensures that intercepted data remains unreadable without the proper decryption keys.
- Cloud Access Security Broker (CASB): Provides visibility and control over data in SaaS and cloud apps — enforcing policies on uploads, sharing, and access.
- Information Rights Management (IRM): Applies access controls directly to files (e.g., read-only or time-bound access), even when data leaves the organization.
- Data Classification & Tagging: Labels data based on sensitivity level (e.g., public, internal, confidential), enabling tiered protection and policy enforcement.
5. Security Analytics and Monitoring
You can’t trust what you can’t see. Continuous visibility and analytics are the backbone of Zero Trust — ensuring that every action is monitored, analyzed, and responded to in real time.
Key solutions:
- Security Information and Event Management (SIEM): Centralizes logs from across the enterprise to detect threats, investigate incidents, and ensure compliance.
- User and Entity Behavior Analytics (UEBA): Uses AI to detect unusual behavior (e.g., a user downloading thousands of files), often missed by static rules.
- Extended Detection and Response (XDR): Integrates threat data across endpoints, networks, cloud workloads, and applications — enabling fast and coordinated incident response.
- Continuous Risk Evaluation: Context-aware engines that recalculate access decisions based on user behavior, threat intelligence, and posture changes.
6. Application Security
Applications are prime targets for attackers — whether hosted on-premises, in the cloud, or delivered via containers. A Zero Trust approach secures applications throughout their entire lifecycle — from code to deployment to runtime.
- Runtime Application Self-Protection (RASP): Embedded within the application, RASP detects and blocks threats in real-time during execution. RASP has deep visibility into how the app behaves internally and can stop attacks based on actual code behavior.
- Secure Coding and DevSecOps: Zero Trust starts in the development phase. By integrating security into CI/CD pipelines (also called “shifting left”), vulnerabilities are detected early through static code analysis, dynamic testing, container scanning, and dependency checks.
- Threat Modeling & Penetration Testing: Applications are continuously reviewed from a threat actor’s perspective. This includes logic-based flaws, broken access controls, and insecure configurations — ensuring developers think like attackers.
- Web Application Firewall (WAF): Acts as the first line of defense by filtering out malicious traffic targeting known application-layer vulnerabilities such as SQL Injection, Cross-Site Scripting (XSS) and remote file inclusion. A Zero Trust-enabled WAF also enforces granular access rules and bot protection.
WAF and Zero Trust Security Model for Application Security
Web Application Firewalls (WAFs) are essential enforcement points in a Zero Trust Architecture (ZTA), particularly for organizations operating in cloud-native, SaaS, and API-driven environments. As traditional perimeters dissolve, WAFs bring Zero Trust principles to the application edge — inspecting, filtering, and blocking malicious traffic in real-time.
Enforcing Least Privilege at the Application Layer
Zero Trust is built on the principle of least privilege — and WAFs extend this control to the application level. By permitting only validated, legitimate requests, WAFs prevent unauthorized users, bots, and anomalous behaviors from accessing sensitive endpoints.
To understand how WAFs enable this level of control, see how a WAF works.
- Policy-based Access Control: Restrict access based on specific URLs, HTTP methods, or request payloads to limit exposure and reduce attack surfaces.
- Geo-fencing and IP Reputation Filtering: Block or allow traffic based on geographic origin and threat intelligence-backed IP reputation, minimizing global threat exposure.
Continuous Monitoring and Deep Inspection
Zero Trust assumes compromise is inevitable. That’s why real-time monitoring, logging, and traffic inspection are vital components — and WAFs like AppTrana are built with this mindset.
- TLS/SSL Inspection: Decrypts and inspects encrypted HTTPS traffic to detect hidden threats.
- Deep Packet Inspection (DPI): Analyzes data payloads for sophisticated injection attempts, data exfiltration attempts, and protocol abuses.
- SIEM Integration & Real-Time Alerts: Seamless integration with SIEM tools ensures every anomaly is logged, correlated, and visible for compliance and forensic investigation.
As your Zero Trust architecture scales, data visibility becomes crucial. AppTrana’s intelligent inspection, logging, and integration of Data Loss Prevention (DLP) at the application layer help you identify where sensitive data resides and block unauthorized access or exfiltration attempts — securing data even after attackers breach perimeter defenses.
By acting as a real-time, intelligent gatekeeper for web applications and APIs, WAFs / WAAPs support key pillars of the Zero Trust security model — ensuring access is tightly controlled, threats are rapidly contained, and data stays always protected.


